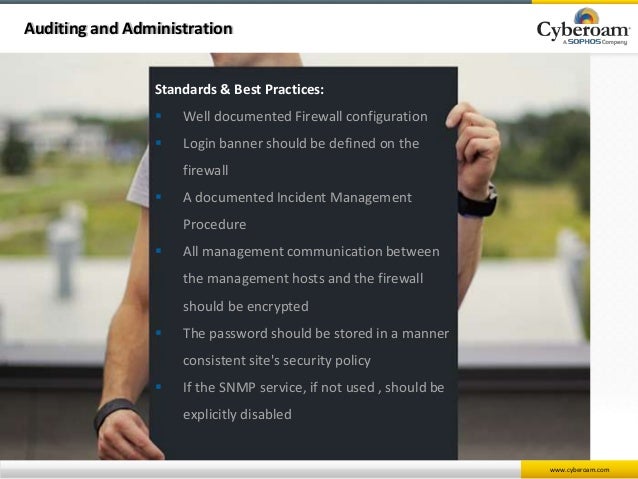
How to Perform Firewall Audit? Firewall audits help you identify vulnerabilities in your network security posture and determine areas where you must customize your security policies.

remedy change itsm bmc management request integration audit screenshots
How much of an issue these rules are depends upon the position of the firewall. This is certainly a tool that is more likely to be owned and operated by the client than an auditor or consultant, but the data it produces provides value on a daily basis, not just at audit time.
How can I audit a firewall? In computing, a stateful firewall (any firewall that performs stateful packet inspection (SPI) or stateful inspection) is a firewall that keeps track of the state of network connections (such as TCP streams, UDP communication) traveling across it.
This firewall configuration audit tool audits the complete firewall security and provides detailed firewall configuration analysis. This firewall audit tool cross verifies the exsisting firewall rules against a preset firewall audit checklist. This not only measures the impact, but also rates
video explains how to audit firewall in 10 configuration Rule base audit
firewall
6 How to Audit a Firewall? ( Firewall Audit 101 ) As explained in the previous section, frequent and thorough firewall audits are critical to reduce business risk exposures on an on-going basis, and are also required for to demonstrate compliance with many information security regulations and

firewall

faar firewall

udaap future
In this video you can learn How to use Nipper studio for Firewall Auditing.
Firewall audits can help prove how secure a network actually is -- as opposed to how secure your customer thinks it is. Here, Hamelin, chief security architect at Tufin Technologies, provider of network security solutions, discusses the importance of the firewall audit, and how to get one done.

firewall
I've been looking for a way to make auditing the Windows Firewall a little easier. The main items I am concerned with are pulling the correct profile If not, how would I go about separating the string in to discreet elements (interestingly, if I do something like $gpoRules | Get-Member, the output
Here you may to know how to audit firewall. Watch the video explanation about The 7 Most Common Firewall Configuration Mistakes Online, article, story, explanation, suggestion, youtube.
How to Audit Firewall, what are the standard Practices for. 8 hours ago A quarter of UK and US businesses have had to re-do more than 60% of all firewall changes since they were not implemented correctly the first time 4. Firewall Audit Procedure Baselines and
04, 2021 · Obtain previous audit reports. Obtain internet policy, standards, and procedures regarding firewall inspection. Access to firewall logs, which the firewall rule base can analyze to determine which rules are being used. Obtain existing …
Preparing for a firewall audit. Network security audits are getting a lot of coverage these days To help you better understand the depth and breadth of a full firewall audit, we have compiled the How are changes managed? What is the procedure that is used to receive requests, track them,

firewall conducting risk
18, 2011 · 1) Auditing the Change Process. The first technical step in a firewall audit is normally an examination of the firewall change Reading Time: 8 mins
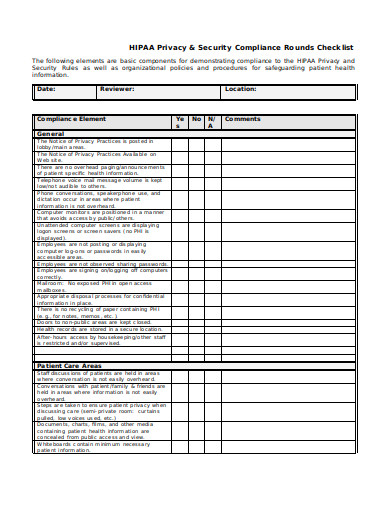
1 Introduction to Firewall Audit Checklist: 2 Record checklist details. 3 Pre-Audit Information Gathering: 4 Make sure you have copies of This Process Street firewall audit checklist is engineered to provide a step by step walkthrough of how to check your firewall is as secure as it can be.
crowdstrike fehlerbehebung protokollierung
Firewalls form the first line of defense for hazardous incoming or outgoing information in a network. By protecting systems from hacking attempts to While not a comprehensive list, these steps should serve to provide a sense of how one prepares for a full firewall audit. By getting highly familiar
How do we conduct a basic firewall audit. Strategic audit strategics the auditing skill to be further understood and can be a tool for competition on business. There are some techniq ... read more.
How Firewall Audits and Reporting works. A firewall device is a network security system that monitors and controls incoming and outgoing network traffic based on specific security policies. This device establishes a barrier between a trusted internal network and untrusted external
I'm looking to perform policy audits against firewall configurations and/or rulesets. This should be performed independently of any configuration management systems, ideally by operating off the running config. I am most interested in inspecting Cisco PIX/ASA/FWSM and Juniper
Below, the firewall audit checklist for firewall auditing, optimization, and change management processes How often are backups made? Is encryption used when backing up? What are the results of the A successful firewall audit requires validation of secure configuration and regular audits
For optimal protection, use a script to audit your firewall settings regularly.
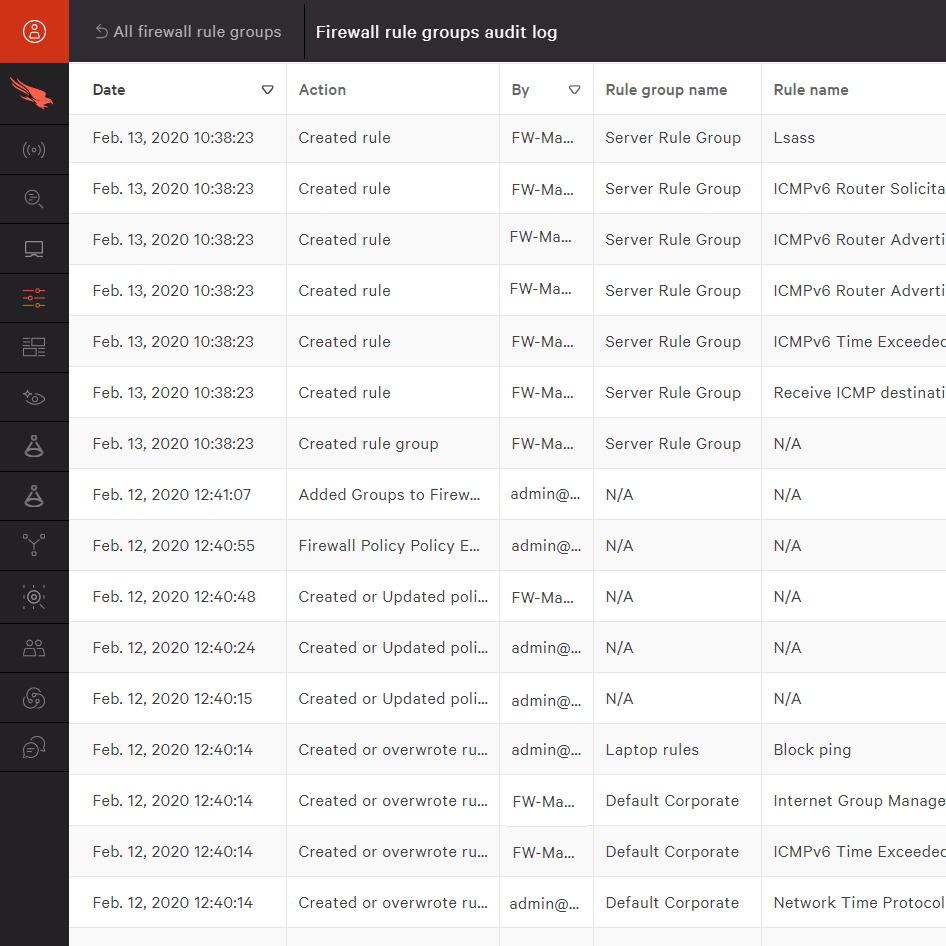
The firewall audit process is arduous. Each new rule must pre-analyzed and simulated before it can be implemented. A full and accurate audit log of each change must be maintained. Once you have gathered this information, how are you going to aggregate it and storing it?
Process Street firewall audit checklist is engineered to provide a step by step walkthrough of how to check your firewall is as secure as it can We recommend utilizing this firewall audit checklist along with the other IT security processes as part of a continuous security review within your organization, provided you are able to do so with the resources you have.


audit

firewall
27, 2020 · Collect Key Information Before Beginning the Audit Your firewall audit probably won’t succeed if you don’t have visibility into your network, which includes hardware, software, policies, as well as risks. The critical information you need to gather to plan the audit work includes: Copies of pertinent security policies
Improved firewall audit. Example flow of debugging packet drops with filter origin. The next section describes the improvements made to audits 5157 and 5152, and how the above filter origins are used in these events.
Getting started with Oracle Audit Vault and Database Firewall for Database auditing and Firewall monitoring. Describes how to register a target for audit collection, setup an audit trail to collect audit records, and configure the Database Firewall to monitor SQL traffic to the target.
Change auditing of Windows Firewall is part of a defense-in-depth strategy because it can be used to generate alerts about malicious software that is attempting to modify firewall settings. Auditing can also help administrators determine the network needs of their applications and design
A firewall audit is a process that provides visibility into your firewall's existing access and connections, identifies vulnerabilities, and reports on firewall changes. How many rules does the firewall security policy have? How many did it have at the last audit?

advanced infographic persistent threats threat apt apts

firewall audit fillup locatoin
Auditing of networks has a big role to play in keeping your system safe. One audit which can help you to ensure that your network connections and internet use are secured is the firewall audit. This helps to establish how well secured the network is, rather than how secure customers or IT staff believe that
Help simplify firewall security audits with an event log management tool that provides out-of-the-box compliance report templates and log file analysis. Monitoring and visualization of machine data from applications and infrastructure inside the firewall, extending the SolarWinds® Orion® platform.

unece escrypt cybersecurity adopted wp29 regulations
31, 2019 · Why Firewall audit is important? Once a firewall is in situ, activity regular firewall audits at a minimum on AN annual basis is important to the protection of any business. Annual audits increase the probabilities of catching any weaknesses in your network’s security. additionally to the firewall-related code, security controls and policy ...

Firewalls continue to secure a countless number of organizations across the world and remain first line of defense against known cyber attacks and network risk… This can aid in prosecution in some jurisdictions and also serves as a preventive measure to unauthorized access. How to Audit
Auditing One Firewall With Active Scanning. Our first scenario considers a very simple network that has one firewall. On one side is the Internet and How you answer these questions will be determined by your threat model, your firewall auditing requirements and maybe even external information
03, 2013 · 6 Steps to Acing Your Next Firewall Audit Step 1: Gathering Pertinent Information Before You Undergo an Audit. Without understanding what’s in your network, Step 2: Review Your Firewall Change Management Process. Poor documentation of changes, including why the change Step 3: Audit Your ...
A tool for analyzing firewall rules. Contribute to conix-security/audit-springbok development by creating an account on GitHub.
How to Audit a Firewall? ("Firewall Audit 101"). As explained in the previous section, frequent and thorough firewall audits are critical to reduce business risk exposures on an on-going basis, and are also required for to demonstrate compliance with many information security regulations and
firewall audit process is crucial as compliance must be continuous, not simply at a point in time. The firewall audit process is arduous. Each new rule must pre-analyzed and simulated before it can be implemented. A full and accurate audit log of each change must be maintained. Today’s security staffs now find that being
22, 2021 · The first technical step in a firewall audit is usually a review of the firewall change process. The goal of this step is to make sure that requested changes were properly approved, implemented and documented. You can accomplish this in a few different ways - depending on whether you have a tool to assist you or you are doing it manually. You'll first …
This how to will walk you through some best practices to conduct an audit of your From outside your network run port scanning utilities against your firewall and all external IP addresses. Based on your audit you should have an idea of what you expect to be accessible.
1: Gathering Pertinent Information Before You Undergo an Audit. Step 2: Review Your Firewall Change Management Process. Step 3: Audit Your Firewalls' Physical and OS Security. Step 4: Cleanup and Optimize Your Rule Base. Step 5: Conduct a Risk Assessment and Remediate Issues. Step 6: Ensure Ongoing Audit-Readiness.

domain multi management security checkpoint domains secure software environment components communications graphical layout
hipaa ahima
