One of Wireshark's strengths is its statistical tools. When using Wireshark, we have various types of tools Using the statistics for capture file properties menu. In this recipe, we will learn how to get general information from the data that runs over the network. Penetration Testing News. Podcasts.
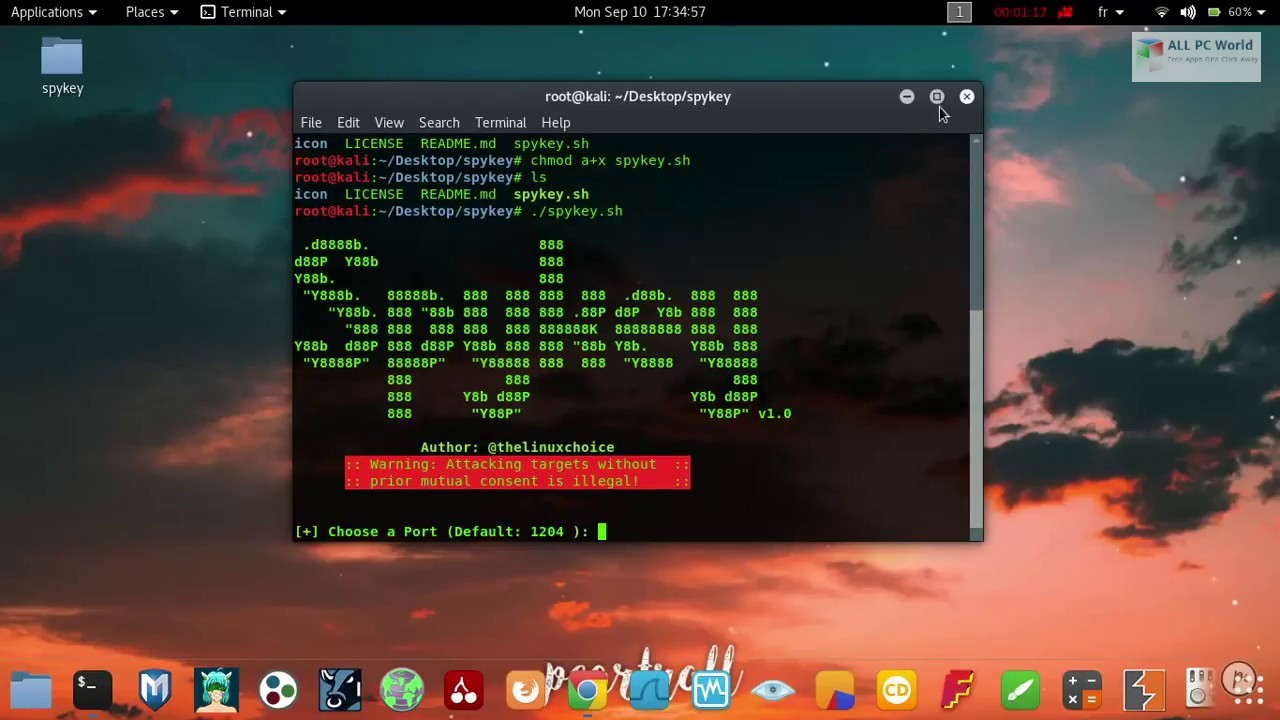
kali linux os system pc security network version cali features operating port aircrack penetration ng testing wireless packets legal
Nmap is used to scan whole networks for open ports and for mapping networks and a lot more things. It is mainly used for scanning networks and discover the Note: If you are really interested in Network administration and penetration testing then knowing how to use Wireshark is a required skill.

kirchner
Wireshark is a must-have (and free) network protocol analyzer for any security professional or systems administrator. It's like Jaws, only for packets.
Wireshark Download and Installation How to Use Wireshark to Capture Packets Troubleshooting With Packet Capture How to Read Wireshark And Using Wireshark to view network traffic is great, but Wireshark cannot be used for intrusion detection purposes. It won't alert you when something

commando vm hacking distribution windows based
Although Wireshark uses a separate process to capture packets, the packet analysis is single-threaded and won't benefit much from multi-core systems. You will find a lot of information not part of this user's guide. For example, it contains an explanation how to capture on a switched network,
Wireshark, a tool used for creating and analyzing PCAPs (network packet capture files), is The installation for Wireshark is very easy and typically comes with a packaged GUI wizard. Before going into detail about how to analyze each protocol in a PCAP we need to understand the ways to gather
Filters using logical operands can be used to build rather complex structures, but apparently, usage of the same filter with comparison operators is buggy. Since web proxies use HTTP Basic and Digest authentication to authenticate users, you can use the appropriate Wireshark filters.
How to Use Wireshark. As mentioned above, Wireshark is a network protocol analysis tool. Colorize packets. Generate Statistics. Most users use Wireshark to detect network problems and test their software. As an open-source project, Wireshark is maintained by a unique team keeping
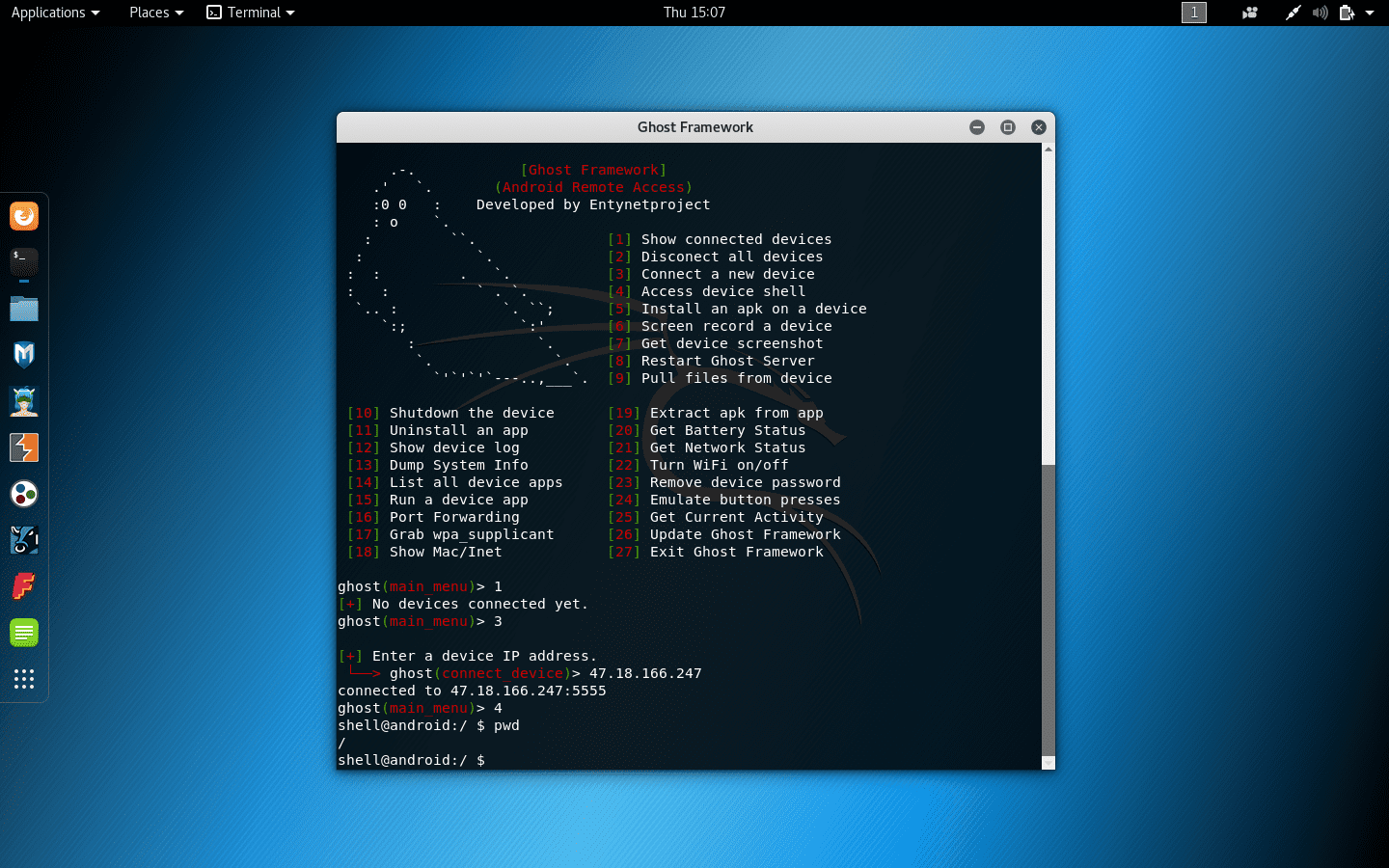
How Penetration Testing Works. To lay it out plainly, entrance testing is a recreated assault on your framework to recognize any recognizable weaknesses. Wireshark is an unquestionable requirement that have network convention analyzer. It is broadly used to catch live organization traffic for

cheat sheet sans powershell testing penetration sheets pdf windows linux security test power commands pen shell forensics study computer ipv6
Penetration testing. Wireshark is a very useful tool for information security professionals and is thought of by many as the de facto standard in network packet and protocol analysis. In this Series. PCAP analysis basics with Wireshark [updated 2021]. How to use Wireshark for protocol
A Wireshark tutorial for beginners that shows users how to track network activity, view specific frame, tcp, ip and http information, view specific
By using Wireshark, you can filter different packets based on their port number. Why would you want to do this? Because in that way, you can filter out all the packets you don't want in your computer for How Does Wireshark Capture Port Traffic? Wireshark captures all the network traffic as it happens.

commando fireeye pentest hackers hackersonlineclub pentesters teaming
Earlier we discussed how to use display filters in Wireshark and tshark, but let's take a closer look at how these expressions are built, along with some examples. A typical display filter expression consists of a field name, a comparison operator, and a value.
Application Penetration Testing. Wireshark is an essential tool for pentesting thick clients and most things in a Windows environment. As a pentester you surely will find it often more convenient to use tcpdump as a collector and use Wireshark on a different system to analyze the traffic.
How do i win this? You should now be able to see PC2 traffic in wireshark. This will also HAVE to be HTTP as you aware, HTTPS would require decryption of the session. Not the answer you're looking for? Browse other questions tagged wireshark penetration-testing or ask your own question.
To see how to use Wireshark for capturing packets, just read the next section. Now that you know how to use Wireshark, the best thing to do is try on your own. Just try to surf the web, send emails or even play online games while sniffing the traffic.
How to Download and Install Wireshark. Wireshark can be downloaded at no cost from the Wireshark Foundation website for both macOS and You must be logged in to the device as an administrator to use Wireshark. In Windows 10, search for Wireshark and select Run as administrator .
How do we find such host information using Wireshark? Depending on how frequently a DHCP lease is renewed, you might not have DHCP traffic in your pcap. Fortunately, we can use NBNS traffic to identify hostnames for computers running Microsoft Windows or Apple hosts running MacOS.
Posts about Wireshark written by Administrator. This technique is stealthier than the active and it can be used in a scenario when we are attacking a corporate wireless network especially in the morning when there will be a variety of devices that will try to connect and unveil it's presence.
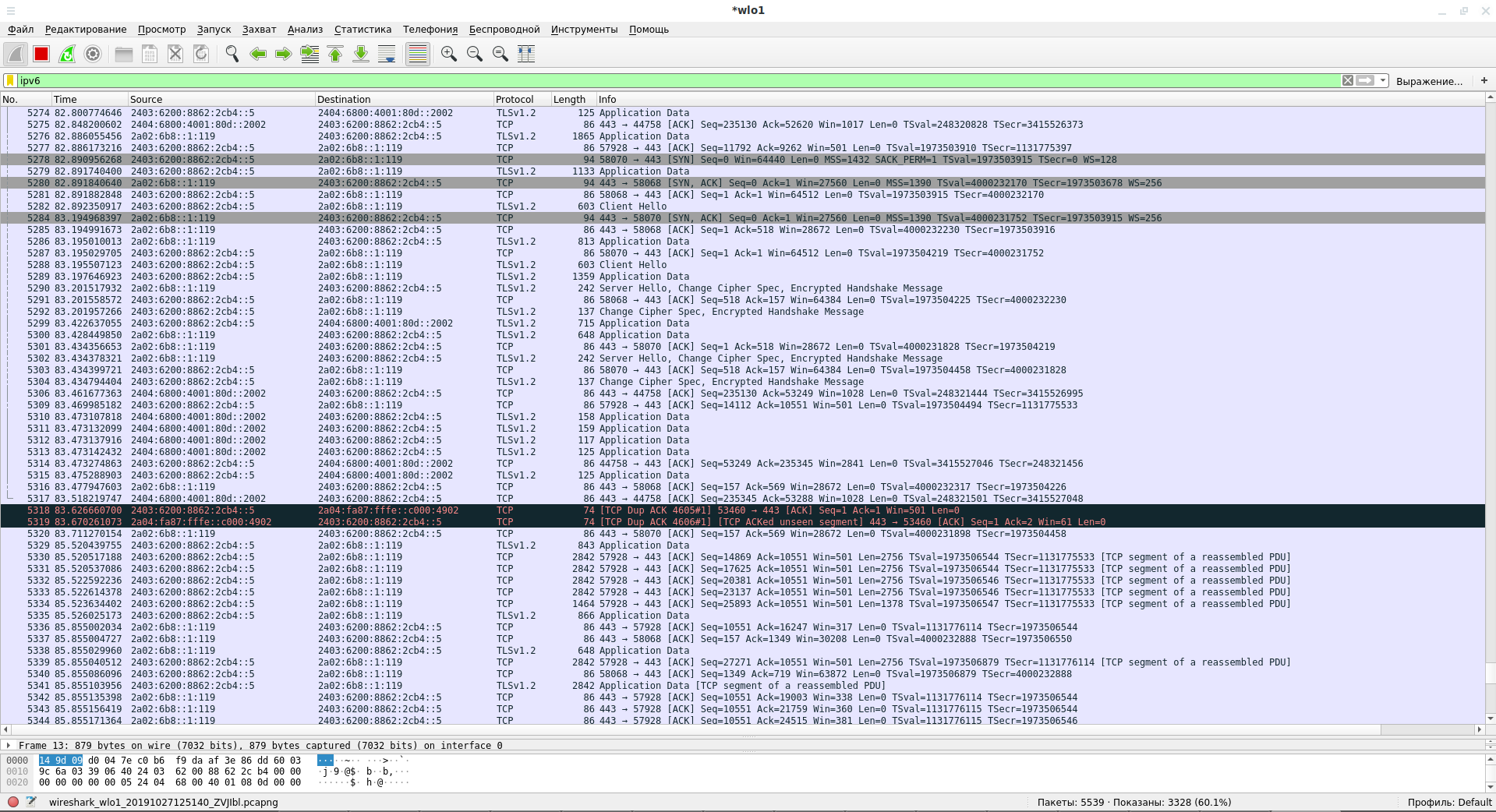
ipv6 analyzing configuring
Besides, they provided a sample for basic penetration testing using Wireshark. ... The PEN testing allows a PEN tester to check the functional aspects of a system that how much a system is vulnerable to the Network security & intrusion attacks & to see its defense mechanisms to
The usage of Wireshark also ensures that the procedure followed is up to the required standards. This paper discussed about the need to utilize penetration testing, the benefits of using Wireshark for the same and goes on to illustrate one method of using the tool to perform penetration testing.
Home. » Penetration Testing. » Wireshark For Pentester: A Beginner's Guide. Wireshark is an open-source application and it is the world's foremost and widely-used network protocol How to filter packets in Wireshark. ….and much more things!! Wireshark can be started through

sql sqlmap hackersonlineclub vulnerabilities microsoft
How to Use Wireshark. You can download Wireshark for free at It's also freely available, as an open source application under the GNU How to Install Wireshark on Windows. If you're a Windows operating system user, download the version appropriate for your particular version.
Wireshark can be used to capture the packet from the network and also analyze the already saved capture. See the screenshot to understand live capture. Also, look for Wireshark's indication for "live capture is in progress" at the bottom of Wireshark.
use "-G help" for more help. Dumpcap can benefit from an enabled BPF JIT compiler if available. You might want to enable it by executing: "echo 1 Wireshark can decode too many protocols to list here. This is a meta-package for Wireshark. Installed size: 74 KB How to install: sudo apt install wireshark.
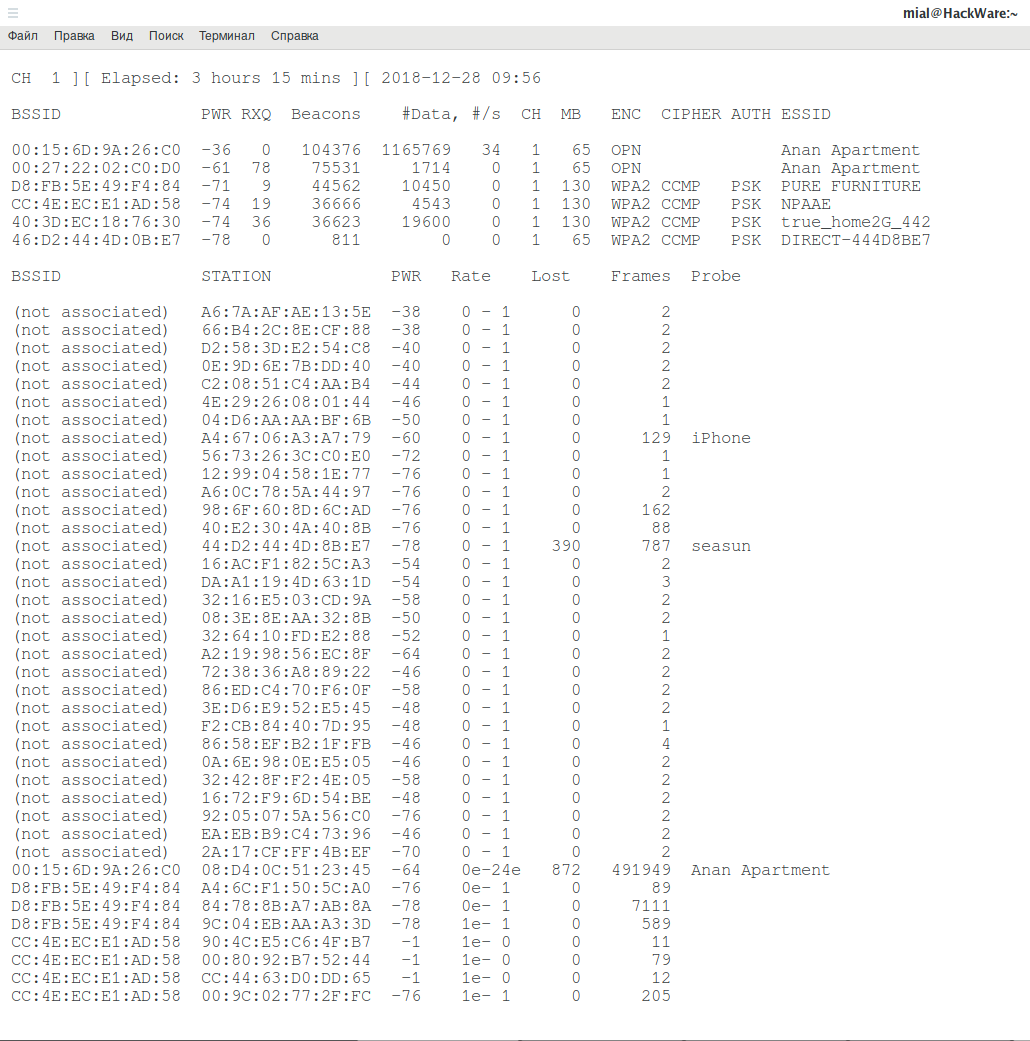
analyze intercept traffic wi fi open airodump ng
What is Wireshark Used for? As mentioned previously, the uses for Wireshark are virtually limitless, and are only bound by the number of protocols and But Wireshark isn't the only method of capturing packets. As a penetration tester, you're going to need to know how to use several different types
Penetration testing is a process used by companies to test the security of their software and infrastructure. In penetration testing, a group of security professionals act as attackers in order to identify holes before hackers do. A pen tester's goal is to provide information to the company
