Let us go through how the SNYK works. SNYK offers two modes of operation :CLI and UI. In graphical user interface , this is the first screen you will While using CLI the process is pretty straightforward. You need to clone the Git repository via CLI and then install dependencies after reaching to
How to use snyk on a hosted gitlab. I have tried Dependabot, to no avail. Snyk looks promising but our code is on a hosted instance of gitlab, does anyone have any idea how I could adapt the steps located in the following link, to tell ...
11, 2021 · Another impressive free online education site offering ease of use and convenience is Memrise. Available both on desktop and as an app, Memrise is a particularly powerful tool if you are studying a language. The site encompasses many other topics as well, though some of the course material is user generated content.

docker snyk vulnerability extend dockers labomedia

vulnerabilities javascript security snyk source code
How can I use Snyk behind a proxy? - Support Portal Snyk. Snyk Code scanning added to the Snyk Visual Studio. Windows. Details: To use these services, you simply need to register for a free Snyk account using your GitHub, Gmail, or other credentials.
Learn how you can leverage the use of Snyk inside your Docker engine installation. Now we can. Version of the Docker engine also includes the Snyk components needed to inspect the Docker images directly from the command line
integrates directly into development tools and automation pipelines, making it easy to find, prioritize, and fix security vulnerabilities in code, dependencies, containers, and infrastructure as code. Backed by industry-leading vulnerability intelligence, and designed by developers for developers, Snyk fits into your development workflow ...
This topic describes how to use the Snyk Service Broker for VMware Tanzu after it has been successfully installed. For more information on managing service instances, see Managing Service Instances with the cf CLI. After the Snyk tile is installed, you can see the snyk-service-broker and
This article will walk you through how you can use Snyk to make your applications more secure. Getting Started. If you don't have one handy, you can use the demo application we'll review in this article, snyk-demo-app. Simply run these lines to clone it and install its dependencies
over developers who build securely with Snyk Get started for free. No credit card required . We will not make any use of the auth provider without your permission. By ... We will not make any use of the auth provider without your permission. By logging in or signing up, ...
Snyk for C / C++ - Snyk User Docs. Design. Offer Details: As Snyk uses file signatures to find the closest possible match to an open source library, your Users only need to install Snyk locally and use its CLI. You only need to know how to use a couple of commands. And these commands can

imgview npm scrolling thesaurus localstorage lichess sensor virtualized sendgrid nfc homebridge snyk markdown loader webpack contrib nodemailer mssql validator typeorm
Users only need to install Snyk locally and use its CLI. You only need to know how to use a couple of commands. And these commands can be integrated into the git-flow via git hooks. Snyk provides a free plan for open source projects. It includes unlimited tests and fixes for open source vulnerabilities.
chore: execute snyk and snyk-protect using bin file. Snyk is really powerful when you are continuously scanning and monitoring your projects for vulnerabilities. Use one of our integrations to stay secure.
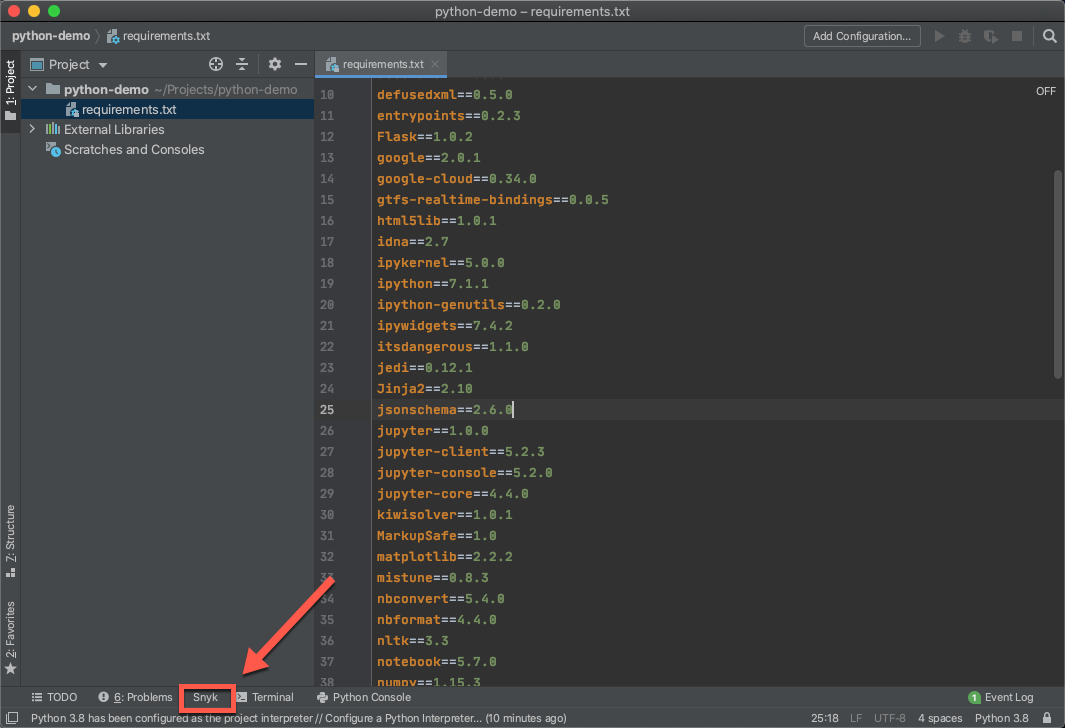
Snyk extension can be installed directly from IDE. To install it open Extensions > Manage Extensions menu. Search for Snyk. Once installed, open the Snyk tool window by going to View > Other Windows as shown in the screenshot below. Once the tool window appears, wait while Snyk extension downloads the latest Snyk CLI version.
is a developer security platform. Integrating directly into development tools, workflows, and automation pipelines, Snyk makes it easy for teams to find, prioritize, and fix security vulnerabilities in code, dependencies, containers, and infrastructure as code.
Snyk is an editor specializing in analyzing vulnerabilities in the code of infrastructure configuration files, including those present in containers and. Snyk Infrastructure as Code, on the other hand, analyzes the vulnerabilities and fixes them in the JSON and YAML Kubernetes configuration files.
To use Snyk Open Source or Snyk Code using an IDE plugin, you do not have to give Snyk access to your GitHub repositories. Snyk provides you with a number of ways to secure your code very early on in development — in your IDE, using Advisor, and the Snyk CLI.

vulnerabilities snyk
Snyk is really powerful when you are continuously scanning and monitoring your projects for vulnerabilities. Use one of our integrations to stay Expected behaviour. snyk protect requires the Unix patch utility, which is not available on windows. A logical workaround is to install git

snyk vulnerability sdlc cli
You may use your Google, Bitbucket, or Github credentials to sign up. Snyk utilizes these services for authentication and does not store your password. In this post, you learned how to leverage various AWS services to build a fully automated CI/CD pipeline and cloud IDE development environment.

snyk kubernetes
And how to achieve it with OWASP Dependency-Check. This post describes another tool, which can be used to eliminate vulnerable dependencies -- Snyk. Before you can use Snyk, you need to install it using NPM. Make sure you have installed to do so. Then you can simply run
Using Snyk and the Podman API in this way provides container image scanning directly in your local command line, helping developers and admins to scan images and check for By default Snyk doesn't know those images exist locally in Podman, or how to use Podman to interface with upstream.
Docker and Snyk recently entered into a partnership to provide container vulnerability scanning. How does Docker Scan work? Docker included a new command in or later versions called docker scan. When running the `docker scan` command, scans local images against the Snyk
This article mainly describes how to use Nessus for host scanning and use SNYK to perform Docker image scanning. Docker mirror production, using Supermin to pack the host into a Docker image. 1 Introduction Supermin is a tool for creating mini virtual environments, aiming to create a mini
How do you use Snyk for running SAST? Hi peers, From what we have read, Snyk needs us to upload a copy of the source code to Snyk for at least 24 hours for them to perform SAST. I wanted to ask if that's what others are doing or is there a way to not upload source code and perform SAST analysis
08, 2022 · The affected plugins use plexus-archiver to unpack dependencies to disk and have been identified as potential triggers for exposing the vulnerability if dependencies are compromised. See full description for more details. Credit: This issue was identified by the Snyk Security Research Team. CVE-2013-0253 Apache Maven Severity: Medium
Snyk's cloud native application security platform is designed to work like a developer tool - making it not only easy to find issues, but to fix them quickly. Tune in to this live demo of Snyk to see how developers use this tool to secure their proprietary code, open source libraries, container images,
plugin snyk pycharm vulnerabilities
Snyk Container uses the same snyk/scan command with a few parameters. Since the image needs to be built to scan it, add the command to the Visit the Snyk documentation to learn how to understand Snyk Container CLI results , and be sure to explore the section on base image remediation.
is a developer security platform. Integrating directly into development tools, workflows, and automation pipelines, Snyk makes it easy for teams to find, prioritize, and fix security vulnerabilities in code, dependencies, containers, and infrastructure as code.

devsecops gartner snyk
You can also use Snyk to fix vulnerabilities right from the CLI. When it finds a problem in any dependency within your pipeline, it will either give you an option to fix it automatically with a patch, or Perhaps the only real shortcoming in Snyk is that its name is hard to remember how to spell correctly.
Snyk aims to help developers secure use of open source code. To address this, Snyk integrates securing open source into the existing workflow of a developer — for example, by integrating with GitHub — so that vulnerabilities are checked as you go rather than relying on a one-off code
Details: For these use cases, Snyk uses the local Docker client, either through the Registry API or by using the Docker socket. Since there is no Docker Details: How to install the SBT dependency graph plugin to test Scala projects with Snyk CLI The need for the sbt plugin is due to the fact that there
How to use Snyk. 10 видео 2 869 просмотров Обновлен 6 апр. 2021 г. Official Snyk how-to videos for all roles and subscription plans.

injection sql orm snyk
04, 2022 · [DEPRECATED] Core Java Library + PDF/A, xtra and XML Worker. Only security fixes will be added — please use iText 7 - GitHub - itext/itextpdf: [DEPRECATED] Core Java Library + PDF/A, xtra and XML Worker. Only security fixes will be added — please use iText 7
How can I use Snyk behind a proxy? - Support Portal Snyk. News Post. Details: In Windows, run a ipconfig /all command and look for your proxy settings. You must retrieve the following information: http or https. private IP of the proxy. port (80, 8080 or 443 typically). To run Snyk from behind a proxy,
Snyk is a company that provides security tooling which helps to enable more than 400K developers to find and fix vulnerabilities in open source libraries. It's primary free offering for Node comes in the form of the snyk CLI which is available as an NPM module.
While PR analysis within Code Insights and Snyk Pipes are available to use right now, we're rolling out a native Security tab in Bitbucket Cloud. This Snyk score, which is weighed by maturity and severity, helps teams prioritize what to work on and is paired with contextual information with advice on how
Read the StarWind article to find out how to verify that your images are free of known vulnerabilities or exposures to enhance your security posture. Snyk integrates with many different systems to offer a centralized security console. In this article we will first use Snyk.
Once docker has successfully pulled the file you can see just how big the alpine operating system is with the following docker command: docker image ls -a. Once you have your credentials please log in to Now you can use the command line to authenticate snyk inside of your alpine image
