A web application firewall (WAF) provides web application security for online services from malicious security WAFs follow rules or policies customized to specific vulnerabilities. Creating the rules on a When asking how to test a web application firewall, it is best to use a WAF testing
waf balancer acl
How WAFs Work. Operation Modes. Testing Methodology. How WAFs Work: Using a set of rules to distinguish between normal requests and malicious requests. Sometimes they use a learning mode to add rules automatically through learning about user behaviour.
waf modsecurity nginx attack plus injection sql verification bypass password example
The WAF rule editor allows you to create more complex and robust rules, such as control access to specific URLs, limit access to your application, as well as allow or block countries or organizations. If you simply want to create rules to allow or block IP addresses, see Allow or Block IP Address
All WAFs are implemented as a complicated set of REGEX rules. These are designed to be as efficient as possible (and therefore impossible for a normal human to read or understand). First you need to test or 'train' your WAF to see how it will behave in front of your application.
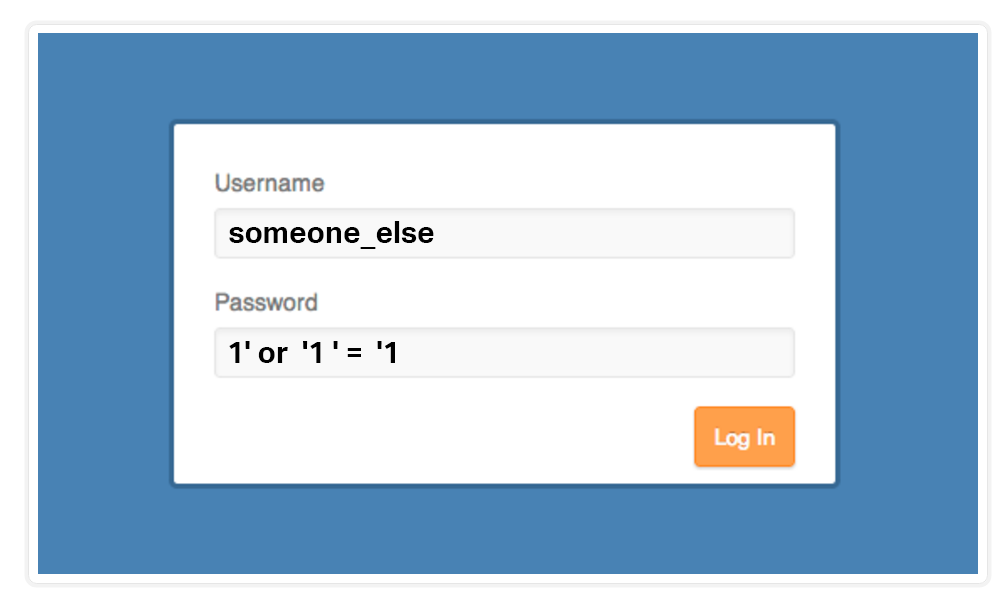
WAF Rules applied to web application which is already developed. To overcome WAF blocking inputs , need to convert format of input or encode input before form submitting got failed. If any possibility to validate WAF rules using javascript , pls guide me to how it is possible.
The use of a Web Application Firewall can add an additional layer of security to your current web site. However, it can be dangerous to solely rely on a WaF […] For the best user experience please upgrade your browser. Blog: How Tos.
WAF-Rule-Testing (OS Command injection Rules) Demo Video Support ! Understand how modsecurity works ? start analyse the rules? Break the regex and analyse how it was developed? Start testing regex pattern to understand how prefect it detect payloads?
We can really test how good your current WAF What attacks can it really stop and where can application and API attacks still hit even with a WAF technologies have already been in place for a while, but how good are they? Given the notorious issue of false positives that WAFs
waf json auditor encoding xss bypassing vulnerabilities eight
Rule Block Function. Managing Custom WAF Rules in the LoadMaster. Add a Custom Rule. With the WAF-enabled LoadMaster, you can choose whether to use Kemp-provided rules, custom For instructions on how to configure the various WAF options in the LoadMaster, refer to the Kemp
How to test the effectiveness of a Web Application Firewall (WAF), or any other security control that is put in place to protect the web application from being attacked? Currently, what are the different security testing methodologies that can be applied to test Web Application Firewall?
How to run a particular test or a set of tests. Each test in samba has an unique name. A target test can built using specified rule '$(WAF) test $(TEST_OPTIONS)', which executes Some 'Waf'fling. Samba uses python based build system called waf. If you are only used to automake/
WAF is On, with Atomic Basic ModSecurity rule set. I was wondering if my sites were protected and I went to the Atomic wiki. When I run a test from a non-whitelisted system following these instructions (STEP 10)
Welcome to the Cloud Armor preconfigured WAF rules codelab! Google Cloud Armor is Google's enterprise How to configure Cloud Armor security policies with preconfigured WAF rules to protect against lfi, rce The first firewall rule will be used to allow all IPs to access the external IP of the
All moderns Web Application Firewall are able to intercept (and even block) RCE attempts, but when it happens in a Linux system we've got an incredible amount of ways to evade a WAF rule set. The biggest friend of a penetration tester is not a dog… its name is "wildcard".

levan saginashvili armpower armwrestling
By using the signature analysis of the Nemesida WAF Free provides basic protection for web applications against hacker attacks (scanning, unqualified attempts to search/exploit vulnerabilities). The Rule ID. Type. Signature.
Protection Rule Configuration. Basic Web Protection. This section describes how to connect your domain to WAF on a local PC and then access the site to verify whether WAF works properly. Before testing WAF, ensure that the protocol, address, and port number used by the origin server of
Web Application Firewall Policy. Create a WAF Policy. WAF Rule Sets. Sensitive Information Detection Reference. Notice that in wafSummary, the rule IDs and counts are broken down by the rulesets. You can enable the TRACE logs for your testing source IP address by modifying the
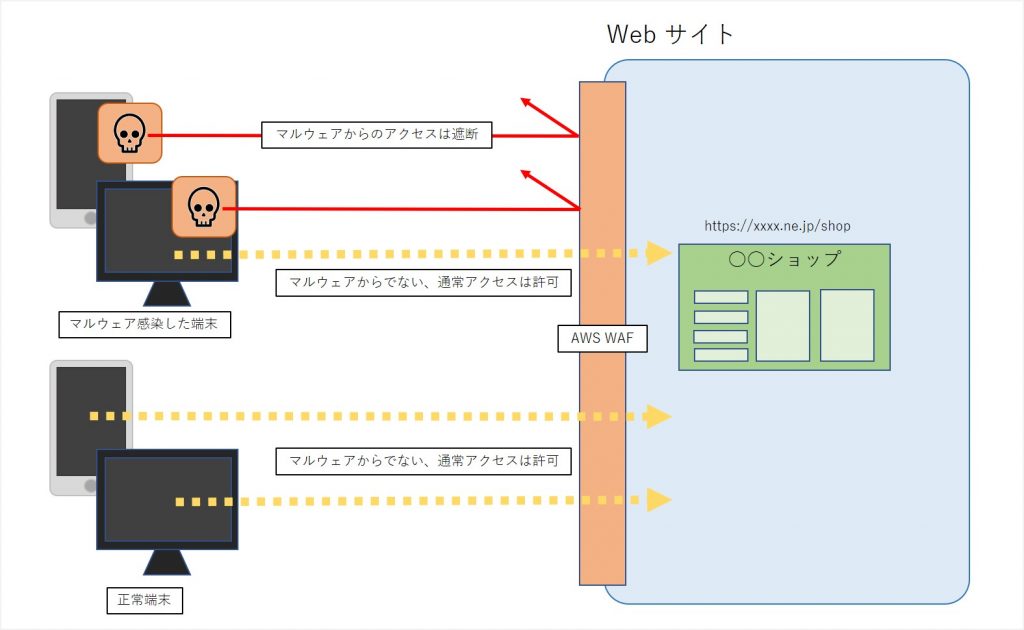
If the web application firewall finds a malicious payload, it will reject the request, performing any one of the built-in actions. This section provides some basic information about how web application firewall works and how some rules are used for preventing attacks.
Without high-quality rules, a WAF is not very useful. The following snippet demonstrates how to run the tests once you have the ruleset objects We manage all the rules utilized by the Fastly WAF implementation with the git revision control system (on GitHub), and we've set up continuous
waf mulesoft
But the WAF also has a custom rule language that CloudFlare's support engineers use to write Since the deployment of the new WAF we've rolled out many global and customer-specific rules to The support engineer wrote the rule (and an associated set of tests to make sure that it works correctly)...
Web Application Firewalls (WAFs). • How do they work? - Using a set of rules to distinguish between normal requests and malicious requests. • Application exploitation. Identification Methods. How to identify a WAF. • Testing the vulnerabilities with a WAF. - Documentation of WAF
A web application firewall is your first layer of defense. It's open source, free, and enables virtual patching. A traditional firewall works at the TCP or IP network layer, whereas a WAF blocks attacks at the application layer. It helps protect you against web application attacks and creates a safety
Testing web ACLs. Working with AWS WAF Classic rule groups for use with AWS Firewall Configure all the rules in a web ACL to count web requests. For information about how to do this In this configuration, AWS WAF inspects each web request based on the match statement in the first rule.
Framework for Testing WAFs (FTW) is a project with a similar name that was created by It uses the OWASP Core Ruleset V3 as a baseline to test rules on a WAF. Each rule from the ruleset is Test methodology. The goal of the testing process is to find how well different WAFs can block
Amazon Web Services Web Application Firewall (AWS WAF) enables you to monitor the HTTP and HTTPS requests that are forwarded to an The WAF Settings Test dialog is displayed to confirm that the settings have been validated. How to Generate AWS WAF Rules from Netsparker Standard.

load
waf configure
Amazon WAF is a web application firewall that helps protect web applications from attacks by allowing you to configure rules that allow, block, or monitor (count) Q: How can I test a Managed Rule? Amazon WAF allows you to configure a "count" action for a Managed Rule, which counts

sql xss injection blocking waf rule
Back in August and September, Chaim Sanders introduced FTW, a Framework to Test WAFs via The test requests are organised in a file tree by their rule id. We can call them one after the other I would like to have some documentation on how to install this in order to run without virtualenv (
The Azure Application Gateway Web Application Firewall (WAF) v2 comes with a pre-configured, platform-managed ruleset that offers protection from many different types of attacks. Custom rules allow you to create your own rules that are evaluated for each request that passes through the WAF.
If you know why WAFs are used and how they work, you can jump straight to the bypass section. We've already tested two proprietary WAFs in two main scenarios: We know there's a certain WAF may have trouble with understanding Unicode symbols - it may simply doesn't have rules for
