Test your screen if you're not sure. Touch the screen with the tip of a pen cap. If the device responds, it is has a resistive or infrared touch screen. Leave about ¼ of an inch of sponge sticking out to touch your screen with. For more tips, including how to make a stylus for a Nintendo DS or e-reader, read on!

tespen ukur fungsi induksi
Use 25+ easy to use pen testing tools & features in a single online platform. Combines Recon, website pentesting, network pentest tools, reporting & automation. in a nutshell. Watch how to scan a target, add manual findings, polish your pentest report, and export it in under 3 minutes.
A penetration test, also called a pen test or ethical hacking, is a cybersecurity technique organizations use to identify, test and Pen tests are not the same as vulnerability assessments, which provide a prioritized list of security weaknesses and how to amend them, but they are often performed together.
Interviewer: How would you test a pen? Candidate : What kind of pen is it? Is it a ball pen, pilot pen, roller pen, sketch pen? … many questions later Candidate: Ok, so as I understand it, we have a pen that is being targeted at 5—10 year olds. The pen has a felt tip and comes in red, green, blue
Welcome back to my third post of the "How to Test" series. I have already written on how to test a mosquito repellent and water bottle . My testing mission for this post will remain the same as I have mentioned in the first post of the series. You might want to take a look at the testing mission .
Pen tests often have two goals, to establish how thoroughly a system's integrity can be compromised and how much user or company data can be accessed. Pen testing provides much-needed insight on where cybersecurity weaknesses particular to a company. Not all companies are alike, and while
Test the pen. If your pen does not work properly, try these fixes first. Hold your pen within 10 mm ( inch) of the surface of the device while watching the Pointing Device Info. You should see a value appear after Proximity, Device Name, Device Type, and Device S/N (serial number).
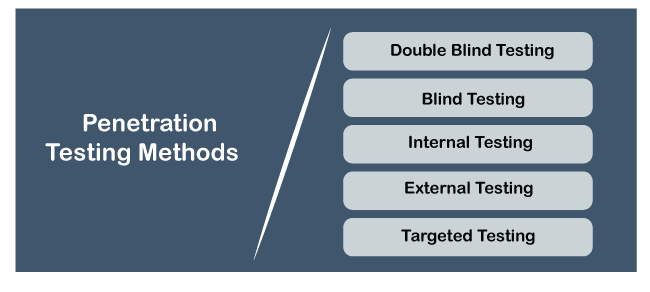
In black box penetration testing, tester has no idea about the systems that he is going to test. He is interested to gather information about the target network or system. For example, in this testing, a tester only knows what should be the expected outcome and he does not know how the
15, 2019 · To get the best feel for a nib, draw figure 8’s in several sets, completing each at increasing speed. You can also draw sideways figure 8’s, doing one set from bottom to top and the next from top to bottom. Unbroken waves and figure 8’s. Oval loops, clockwise and counterclockwise, height x and 2x. Horizontal figure 8s, top to bottom ...Estimated Reading Time: 6 mins

trueline
Test your pen applying a very low pen pressure, and make sur the flow of ink is constant. How is the feel of the nib on paper while you draw. Bonus: Get a retractable pen. I am the kind who always lose his cap. And I am pretty sure I am not the only one. Are you ? Hehe. Some more a pen with no cap
pen testing web application design pen tests web application penetration testing. How I designed an online thrifting app during the pandemic — A UX Case StudyYou will find a detailed account of all the decisions made to design a thrifting app for the Indian market during the pandemicA few months
Each pen spinning trick level has stars or a name. Use CTRL+F to find a trick, which you are interested in. Also you can open videos playlists to watch video Here you can find only a very short list of pen spinning tricks, in fact, there are much more tricks with a pen, than that. But for your reference

kite chinese craft kites crafts simple preschool easy activities activityvillage china paper firecracker dragon idea flying fly printables own firecrackers
pen test javatpoint testing
Much depends on how the pen test is scoped. NIST cautioned that "considering the complexity of the information technologies commonly employed by A pen test is the security equivalent of running a mission. The post-test debrief is vital to getting the most out of a penetration test. What worked?
Penetration testing is the practice of launching authorized, simulated attacks against computer systems and their physical infrastructure to expose potential security weaknesses and vulnerabilities. Should you discover a vulnerability, please follow this guidance to report it responsibly.
Pen Testing. Защита программного обеспечения. Also, identified how software security should be combined with software development. Penetration Testing: Introduction10:11. Pen Testing14:28.

pen motion slow spinning

comptia pentest
Test Cases/Scenarios For All Types of PenNegative Test Cases/ScenariosPerformance Test Cases/ScenariosOut of Scope Test CasesConclusionPrerequisite for performing all these test cases is, a Pen must have a refill and the refill must have ink. 1. The grip of the pen:Verify if you are able to hold the pen comfortably. 2. Writing:Verify if you are able to write smoothly. 3. Verify that the pen is not making any sound while writing. 4. Verify the ink flow. It should not overflow nor get a break either. 5. …See more on
hours ago · The pen testing-as-a-service approach is an outsourced model providing a platform-driven customer experience that offers not only traditional, time-bound methodology-driven tests but the option ...
Pen Testing a SCADA plat- Ryan Oberto, William R. Whitney III, Marcelo Zúñiga Torres 28 form Senior Consultant/Publisher: Paweł Marciniak by Stefano The next thing to do for a beginner new to de- velopment or pentesting is explain how ZAP's ad- vanced components can be useful as a tools in
Pen test - an abbreviation for the "penetration test", is a controlled real hacking attack. Imagine publishing an online challenge such as "Hack me!" The difference lies in the fact that white hats signed a contract with you, the terms and procedure of the testing process were agreed upon and you
Penetration testing is a lot like how it sounds. It involves penetrating a computer system, network or application in the same way that a hacker might in order to A penetration test, also known as a pen test, is a simulated cyberattack against your computer system to check for exploitable vulnerabilities.
Is Penetration TestingPenetration Testing StagesPenetration Testing MethodsPenetration Testing and Web Application FirewallsA penetration test, also known as a pen test, is a simulated cyber attack against your computer system to check for exploitable vulnerabilities. In the context of web application security, penetration testing is commonly used to augment a web application firewall (WAF). Pen testing can involve the attempted breaching of a…See more on Reading Time: 4 mins
drawing app samsung pro galaxy sketchbook note
08, 2014 · Negative Test Cases for Pen: 26. Check pen stress testing by dropping pen down from practical height and check if nothing is breaking, no any damage to pen and pen is working without any issues. 27. Hold the pen upwards direction for some time and try to write on paper. 28. Keep the pen in water and try to write on paper. 29. Check how pen is working at …Estimated Reading Time: 5 mins
Learn how to conduct pen tests to uncover weak spots and augment your security solutions and policies. A penetration test, also known as a pen test, is a simulated cyber attack against your computer system to check for exploitable vulnerabilities.
In this article, I tried to prepare a write-up for the "CC: Pen Testing" room on tryhackme. The idea behind this room is to provide an introduction to various tools and concepts commonly encountered in penetration testing.

IN THIS VIDEO: I am pen testing some new pens and trying out something new after using Paper Mate Inkjoy Gels for ... In this video I set out to test some popular pens among the planner community. I'll be comparing how they rank between three ...
rows · Sep 21, 2021 · This is to test the hovering range for a Windows pen device. Hover …TOPICDESCRIPTIONBarrel ButtonThis is a test for the barrel button ...BufferingThis is to test the data buffering ...Contact accuracyThis is to test the contact position ...Custom GesturesThis is a test to indicate whether or not ...See all 20 rows on
Penetration testers can use Acunetix Manual Tools with other tools to expand their knowledge about a particular security issue detected by an automated web vulnerability scanner or to find advanced security vulnerabilities that automated scanners cannot detect.

penetrant dye testing surface visible ndt pt advantages
22, 2020 · Pen testing or penetration testing is an ethical hacking process which involves assessing an application or an organization’s infrastructure for different types of vulnerabilities. This process of pen testing helps to exploit the various vulnerabilities within the system and the reasons for these vulnerabilities include certain misconfigurations, poorly designed …Estimated Reading Time: 3 mins
Method 2: Dip Pens and Glass Pens. Another way to get an apples-to-apples test would be using the same pen (as opposed to a large number of identical pens). The problem with doing this with a fountain pen is that no matter how thorough you clean a pen, it'll always retain some ink and water from
., How to test the keyboard. Everything is simple here. Press the button on your keyboard (with a pen or with a not sharp pencil), see which one lit up on the screen and put it in place.


testing intelligence test disadvantages equivalency benefits standardized pen ball state know things sat act getty synonym
A penetration test, colloquially known as a pen test, pentest or ethical hacking, is an authorized simulated cyberattack on a computer system, performed to evaluate the security of the
Penetration testing is vital, but are you doing it right? Here are some common mistakes and advice on how to avoid them.

pen water mini cheap sets fineliner washable wenzhou watercolor detailed tip pc
Typing Test - 10fastfingers offers a free online Typing Speed Test Game in multiple languages. You can measure your typing skills, improve your typing speed and compare your results with your friends.
Penetration Testing, commonly known as Pen-Testing, is on a roll in the testing circle nowadays. The reason is not too hard to guess - with the change in the Wondering, why tools? Even if you design a test on what to attack and how to leverage it, a lot of tools that are available in the market to hit

carol concert carols valley test values church celebration
Learn how they work together and how to combine them with human expertise to simplify manual review. Much like craftsman's toolbox, a pen tester's toolbox has wide variety of pen tester tools to work with based on the business objective.

Know how to use your products: For example, rather than letting an attacker continually hammer away at your WordPress system, block their IP address This introduction to security tools and how to use them is just the tip of the iceberg. To dive deeper, you might want to look into the following resources
28, 2019 · Stage 1 – Information Gathering and Client Expectations. When you are discussing the goals of the network penetration test, there are a few important things to consider. Penetration tests fall into three main categories, black …Estimated Reading Time: 10 mins
