Spear phishing is an email spoofing attack targeted towards an individual or an organization to steal sensitive information such as your financial information or account details. Cybercriminals can also use it to install malware on the target computer. Unlike a regular phishing attack, spear phishing
phishing
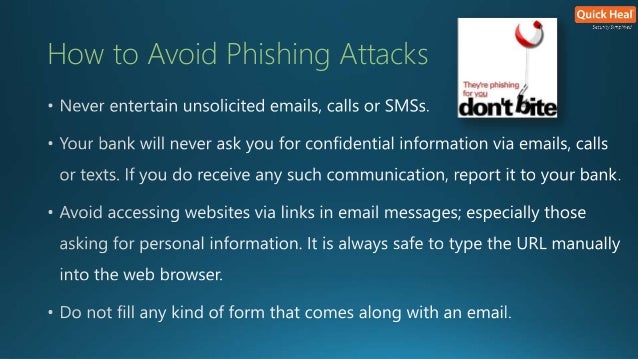
Stop and think before carelessly clicking links. Call and Confirm With the Sender. Spear-phishing emails often purport to be from trusted businesses. Keep Your Secrets Secret. How safe you and your information remain depends in part on you being careful not to post personal information online.
How Spear Phishers Make Their Messages Look Legit. Regular phishing emails are easy to spot if you know what to look for. But unlike the generic phishing emails that are sent out in bulk, a spear phishing attack is targeted to you specifically. The phishers use techniques to make their
How does spear-phishing work? The act of spear-phishing may sound simple, but spear-phishing emails have improved within the past few years and are now extremely difficult to detect without prior knowledge on spear-phishing protection. Spear-phishing attackers target victims who put
How Does Spear Phishing Work? Spear phishing usually takes the guise of in-house emails, asking employees to fill in credential requests. Why would someone be willing to share his/her credentials via email? Well, think of it this way: how likely are you to nix an email from your
Spear Phishing vs. Phishing Spear Phishing is a type of phishing email sent to a specific individual with the intent of acquiring sensitive information Spear Phishing emails have improved over the past few years and now are extremely difficult to detect. Once the bad guys have chosen a target,

phishing spear example

comic
Spear phishing is targeted email fraud with the purpose of accessing sensitive data. Learn about its meaning, how to prevent attacks, and more from KnowBe4. Spear phishing is an email targeted at a specific individual or department within an organization that appears to be from a trusted source.
Spear phishing is more focused than normal phishing. To protect against this type of phishing, your entire company will need to be educated and There are a few ways you can identify a phishing email: Check the From field in the email closely. Spear phishers will use names and domains

engineering social spear phishing ai
Spear phishing attacks continue to increase in popularity among cybercriminals, and businesses must take steps to protect against them or risk seeing Spear phishing attacks are particularly dangerous because they are designed to get around traditional email security like spam filters, the report found.

tessian phishing
How Spear Phishing Works. Phishing schemes are any cyber or phone-based schemes designed to trick a victim into giving up personal details. That information is then later used in some sort of scam. It's a common hack, and most phishing scheme perpetrators target thousands of people with the goal
Spear-phishing emails are getting more sophisticated all the time. One that Inky would have prevented, had it been deployed, was the DocuSign Recently, the podcast Reply All, which runs on a site called Gimlet , highlighted how easy it is to spear-phish people, and even demonstrated that
While spear-phishing is only a subset of phish, the campaigns are highly effective because of the trust users gain seeing a known sender name or domain. Impersonations are also often of individuals in highly placed positions, such as C-level executives, so emails elicit quick response and action
So what exactly is spear phishing? How can MSPs recognize spear phishing attacks before it's too late? With such alarming numbers, it's clear that The best way to identify and stop spear phishing attacks is to go on the offensive. Study up on spear phishing and the possible scenarios you or
Change how your security message is delivered to employees. Start with a monthly email, webinar and Intranet post. Just asking employees to watch out for suspicious-looking emails doesn't drive home the urgency of spear-phishing. Rip it from the headlines.
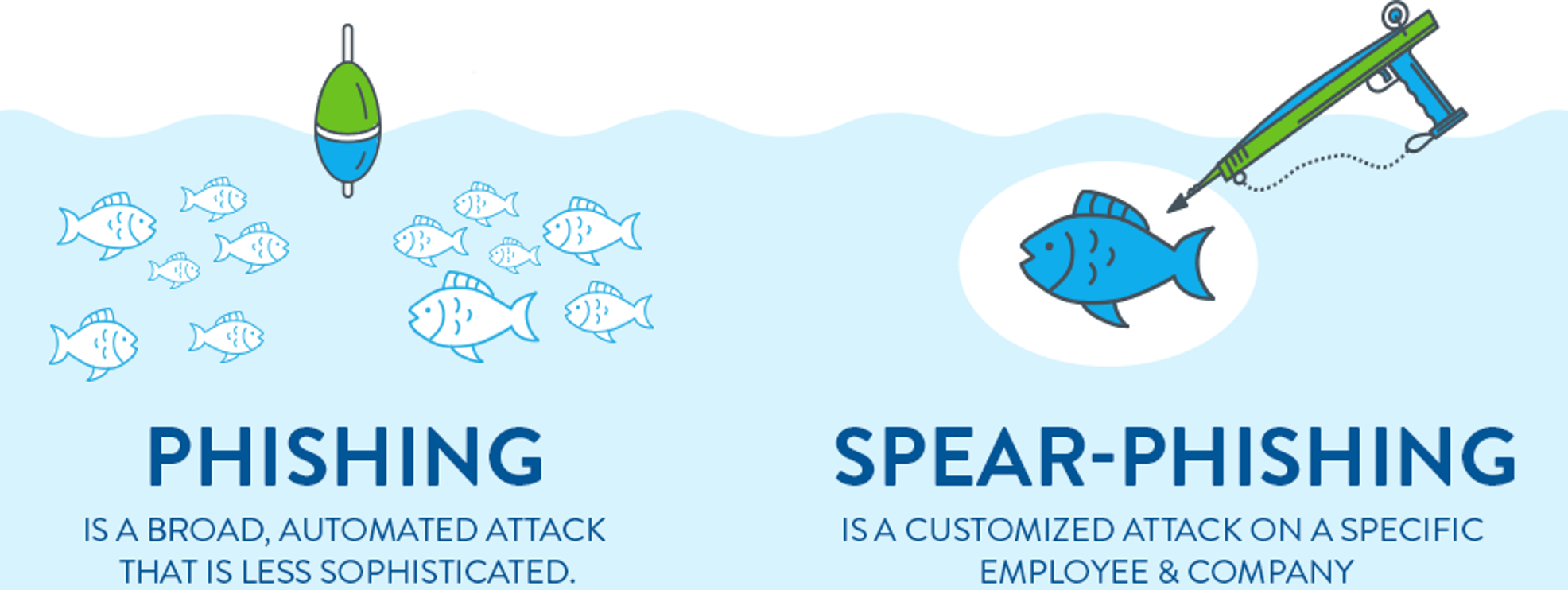
Phishing vs Spear Phishing Attacks. As the name implies, spear phishing is a much more targeted approach. Rather than try to grab many small victims of Common Spear Phishing Email Traps. Here are some common situations that spear phishers use to target high priority companies and employees.
Spear Phishing Protection - Definition & How To Recognize Spear Phishing Email. by Brittany Day. Published: 15 August 2019. Spear phishing emails can include personal information obtained through social engineering such as information pertaining to a person's job, a phone number or
Spear-phishing is a targeted attempt to steal sensitive information such as financial data from a specific individual. The attacker uses personal information of friends, family members, work colleagues or associates to impersonate a trustworthy individual that is well known to the victim.
How does spear phishing work? Spear phishing email attacks are more sophisticated in nature compared to phishing attacks because they are customized Fortunately, there are a number of tried-and-tested measures that you can deploy to combat this menace and stop spear phishing attacks.
Hackers have learned that sending large amounts of email is easily detected for anti-virus programs. With spear phishing attacks, they've changed to
Learn all about spear phishing attacks and how they differ from other phishing attack types. Who does spear phishing target? Enterprises are especially susceptible to spear phishing attacks, as Enable your employees to report suspected phishing messages so that your team can stop

support tech microsoft emails links phishing scam scams fake lead sample messages order suspicious scammers link error text cancellation number
How Do You Recognize Spear-Phishing Email Attacks? There are several ways to spot and Spear-phishing comes in many forms, as fraudsters work across email and other communications channels Learn more about stopping a spear-phishing attack with help from Mimecast and
phishing spearphishing emails techreen
You can stop spear phishing if you're careful enough. How To Prevent Spear Phishing Attacks was originally published in Hacker Noon on Medium, where people are continuing the conversation by highlighting and responding to this story.
On the other hand, spear phishing is very targeted. The attack is personalized because it's intended to affect just one specific individual or business. While phishing is usually conducted via email or social media, spear phishing might go so far as to include phone calls and text messaging.
How does spear-phishing work? Spear-phishing works by targeting a specific individual or organization. Conventionally, spear-phishing targets the victim using email, although variations, such as phishing messages over services such as SMS or Skype, and voice phishing ("vishing") are
Spear phishing tactics use trust to scam victims. Find out about spear phishing attacks, including examples and tips for preventing an attack. Spear phishing is a more targeted type of phishing. The perpetrator typically already knows some information about the target before making a move.
"Spear-" Phishing: How to avoid and help stop phishing. От rogue best buy employee. How to recover phished items, avoid phishing scams, and stop phishers who try to scam. Наградить. В избранное.

phishing avoid scams

phishing spear attack difference between prevention examples
Learn how to prevent spear phishing - the latest and most dangerous technique in the cybercriminal's arsenal - from infiltrating your networks and compromising your customer data, intellectual property, and valuable trade secrets.
To stop spear-phishing attacks security teams must first train users to recognize, avoid and report suspicious emails—it is important for every employee to recognize that their roles grant them access to different data, the currency of the information economy. Second, security teams must
