In Part III, we sent our Zeek logs to Splunk and unlocked a new level of analysis and visualization capabilities. Fortunately for us, Elastic natively supports Zeek logs and is a great way to analyze and visualize Zeek data. To do this, we'll walkthrough these steps
Learn how using Splunk in Java to accept log messages, do indexes using log messages, and provide metrics using log messages. HTTP Event Collector (HEC) enables users to send data over HTTP and HTTPS protocol directly to the Splunk Enterprise and Splunk Cloud from application code.
Solved: We are running R80 GA and I need send logs to a new splunk server. Looking to see if anyone is doing the same.
How do I push VPC flow logs to Splunk using Amazon Kinesis Firehose?
I am trying to implement splunk connect for one of our clusters and I would like to send only application logs (container logs) , I was able to filter out the other kube related pods and network related pods from sending the logs to
splunk spotlight
While Splunk Cloud is a fabulous platform for collecting logs and detecting potential security issues — the documentation on how to make it all fit together is, let's be diplomatic here, less 1: Configure our AWS EC2 Linux server to collect logs locally and send them to Splunk Cloud using a splunkforwarder.
splunk mulesoft logs

heroku
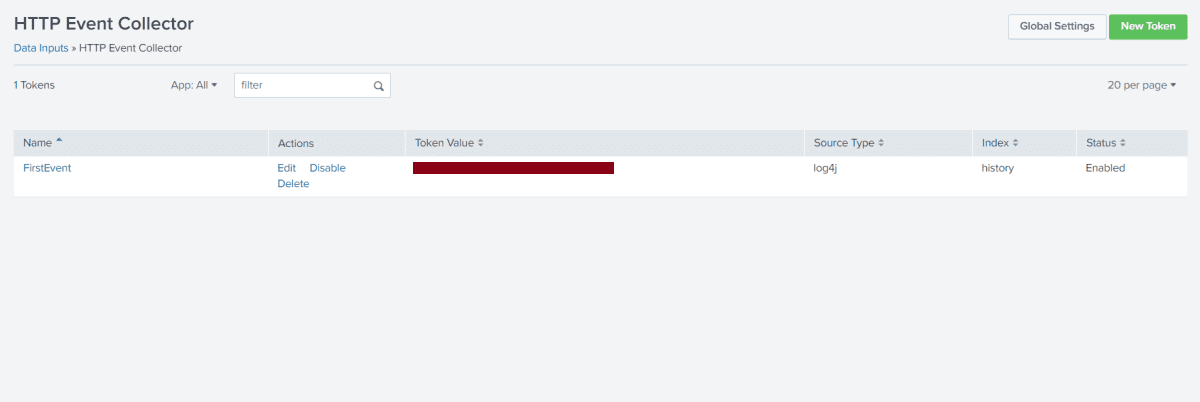
To learn how to do this, see Splunk's Use the HTTP Event Collector documentation. BATCH_SIZE: The number of logs to be sent per batch. Maximum is 100. Logs are batched before sending, and multiple batches are sent each time the extension runs.
HEC allows applications and services to send data and events to your Splunk facility using HTTP and HTTPS protocols without the need for a forwarder. The next set of instructions shows you how to configure log aggregation from Ansible Tower to Splunk Enterprise using HEC (

splunk json servicenow

splunk splunking input
splunk-library-javalogging's Introduction. Splunk Logging for Java. Version Example configuration files for all three frameworks, showing how to configure them to write to Splunk TCP Advice. Splunk Universal Forwarder vs Splunk TCP Inputs. If you can, it is better to log to files
That tag is how Drupal knows to send log message to this service. Without the tag, Drupal wouldn't know this service was a destination for log messages. If you have code that sends log messages to Splunk from a standalone program then I think it is pretty clear from examples provided by core
Splunk Logging. Sumo Logic. DataDog Agent. Cloudwatch. 4. Log management system Apps. Splunk App for Aviatrix. Logging¶. 1. Introduction¶. The Aviatrix Controller and all of its managed gateways can be configured to forward logs to well known log management systems.
Splunk is incredibly precise in how it collects and represents your data; however, if you send it bogus or duplicate data it may index this as well. When this user logs in to Splunk, they are given their specific capabilities and rights assigned by the role. This is granular Role Based Access
For quite some time, Splunk has recommended to collect syslog messages using syslog-ng, save them to files, and send them to Splunk using forwarders. Unless you have a very high message rate, the HTTP destination of syslog-ng can greatly simplify
Recently I started using ELK but I still kept my Splunk setup just for comparison. custom allows additional http fields to be included in eve-log #. the example below adds three I wasn't running my ELK stack on the same machine as suricata so I decided to use Filebeat to send the json file to
# Local splunk configurations splunk: # Configurations for HEC (HTTP Event Collector) hec: # host is required and should be provided by user host To make this easier, I'll map our Harness Delegate Source Type (Splunk) to a very nice SED command, in "System Local." This will do the trick for us!
I've always noticed that Splunk lets you send events data to it via TCP/UDP but have never had cause or reason to use it. If you need to verify that log4net is sending events over UDP you can use Wireshark. Here I have set it up to capture packets from my wifi adapter and monitoring port 9977.
Configure Rsyslog to Send Logs to Splunk Server. I will use my laptop for the test, my laptop is running Fedora Encypted Data vs Non-Encrypted Data. Here is how tcpdump looks like without SSL: [[email protected] ~]# tcpdump -i eth3 tcp port 514 -X -s 0 -nn 17:13 IP
Quering splunk from the splunk interface. Now that we have Apache logs inside Splunk, let's do some simple query. Let's say I want to know how much bandwidth was consumed by one of my websites () in the past 7 days, including today, in megabytes. To do so, I can run
What has to be the host name of Splunk that I have to use to save the logs? curl: (7) Failed to connect to port 8088: Timed out. Later noticed that, in the doc mentioned above, there is a "notes" section which says to prefix "input-" to the host name for self service cloud instances.
This tutorial describes how to install and use Splunk Connect for Kubernetes to collect logs from Kubernetes applications running on Anthos in Google Cloud. Anthos lets you take advantage of Kubernetes and cloud technology in your existing on-premises investments or in the public cloud.
The splunk logging driver sends container logs to HTTP Event Collector in Splunk Enterprise and Splunk Cloud. Usage. How many pending messages can be in the channel which is used to send messages to background logger worker, which batches them.
Splunk logging for Javascript is tested with Splunk Enterprise and An HTTP Event Collector token from your Splunk Enterprise server. : Shows how to configure a logger and send a log message to Splunk.
How to send OpenShift logs and events to Splunk. How to stream logs in AWS from CloudWatch to ElasticSearch. How to ship Kubernetes logs to external Elasticsearch. You can download this article in PDF format via the link below to support us.
: vRealize Orchestrator Discussions. : 1. How to send Logs to splunk? By 'send all the logs' do you mean you want to configure vRO server logging to automatically send all incoming log messages to Splunk?
In this post, we're going to show you how to send audits logs generated from CloudHSM into Splunk. We'll also create a dashboard in Splunk that visualizes critical metrics, such as failed crypto officer login attempts, cryptographic key generation, and deletion events. AWS CloudHSM is
How To Send OpenShift Logs and Events to Splunk. How To Stream Logs in AWS from CloudWatch to ElasticSearch. How is the splunk instance created here?. I read in a docker/splunk website that both the splunk instance and universal forwader container need to exist with a docker network.
In this article we are going to see how to aggregate Kubernetes / Docker events and alerts into a centralized logs system like Elasticsearch and Splunk. Let's create a WebHook callback to send Sysdig events to Elasticsearch and Splunk as an example!

splunk forwarder heavy
In part 1, "Splunking AWS ECS Part 1: Setting Up AWS And Splunk," we focused on understanding what ECS and Fargate are, along with how to get AWS Since NGINX writes two logs to STDOUT, we'll be trapping those events with the firelens router and using FluentD to aggregate and send

splunk aws firewall
Splunk Client Load Testing. Logging to Splunk from a Python Shell. Publishing Logs to a Remote 5 Publishing Logs to Splunk using the Spylunking Logger. 11. 6 Get Splunk Logs from the The default logger will send logs over TCP using the TCP Splunk Publisher. To change this, you
