
splunk forwarder
Splunk logging driver. Estimated reading time: 8 minutes. log-opts configuration options in the configuration file must be provided as strings. Boolean and numeric values (such as the value for splunk-gzip or splunk-gzip-level) must therefore be enclosed in quotes (").
Splunk vs Elastic Search — The Basics. Splunk inherited the long-term solution of the BIG-DATA Conclusion: It totally depends on the choice of the user how the dashboards should be aligned as In short, both Splunk and Elastic Search are competent, enterprise-grade log management
Search: Splunk offers the ability to apply free-form searches and investigate log files, raw events, and statistical information using its SPL and eventually Splunk has an inbuilt mechanism for extracting fields from any logs. So let's search using field name. Now I want to see all logs having method
Such as: management, log collection, web UI/search head and use separate IPs for different major sourcetypes. Perform integrity checks. Splunk is incredibly precise in how it collects and represents your data; however, if you send it bogus or duplicate data it may index this as well.
This scenario shows you how to export selected logs from Cloud Logging into Splunk Enterprise or Splunk Cloud in real time. Splunk enables you to search, analyze, and visualize logs, events, and metrics gathered from your on-premises and cloud deployments for IT and security monitoring.
In this Splunk Architecture blog, you will learn what are the various Splunk components & how they Splunk Architecture: Tutorial On Forwarder, Indexer And Search Head. Last updated on Jul 29 In fact, you can install several such forwarders in multiple machines, which will forward the log data to
1. I want to search the log event. "Closure request counts: startAssets: " and find occurrences where the startAssets are larger than 50. How would I do that? Something like
In this video we demonstrate how to perform basic searches, use the timeline and time range picker, and use fields in the Splunk Search & Reporting app.
Splunk Data Sources. Splunk provides a wide range of plugins to support various resources. For example, to understand Windows event logs, it provides one plugin. For understanding Ubuntu machines logs, it provides different plugins. Based on the analysis of
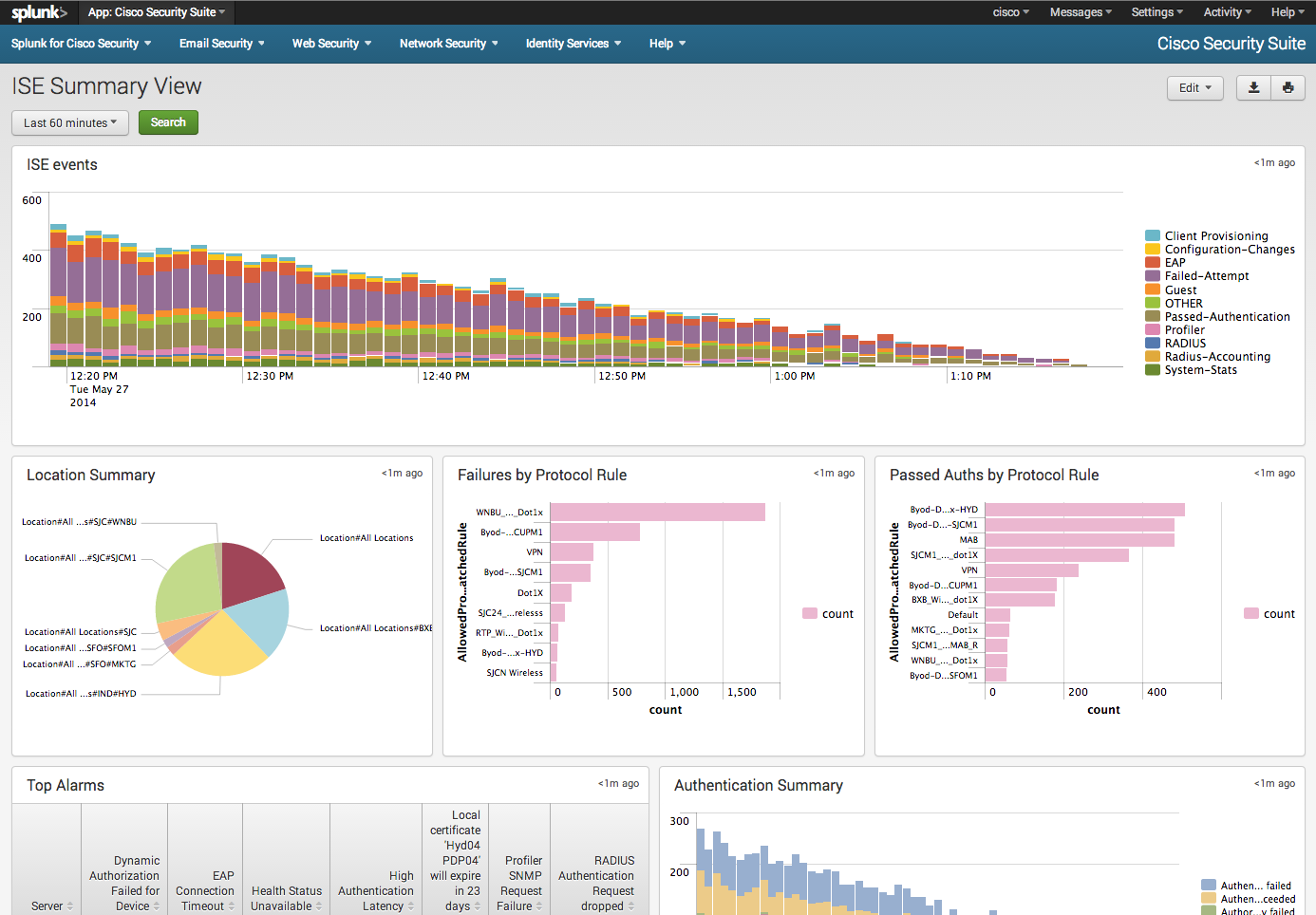
cisco splunk security dashboard ise reporting app dashboards expanding centralized alerting vendor multi identity engine services thesecurityblogger
Splunk® Log Observer on-boards some of the most popular data sources, including OpenTelemetry, Kubernetes, Fluentd and multiple AWS services Reduce time-consuming context switching between monitoring and troubleshooting. Splunk Log Explorer is designed so that an attribute of a
Tweet. One of the most powerful features of Splunk, the market leader in log aggregation and operational data intelligence, is the ability to extract fields while searching for data. Unfortunately, it can be a daunting task to get this working correctly.

splunk app jenkins
A Splunk search retrieves indexed data and can perform transforming and reporting operations. An event is a result that has a timestamp and raw text. Typically in event is a record from a log file, such After teaching Splunk how to extract out more fields from the raw underlying data, the same
Splunk helps in monitoring, analyzing, search, and visualization of machine-generated data in real-time. Let's know more with the Splunk tutorial! Splunk is the ideal choice for addressing the requirements of IT infrastructure through an analysis of log generated in different processes.
Splunk - Basic Search, Splunk has a robust search functionality which enables you to search the entire data set that is ingested. This feature is accessed through the app named as Search & Reporting which can be seen in the left side bar after logging in to the web interface.
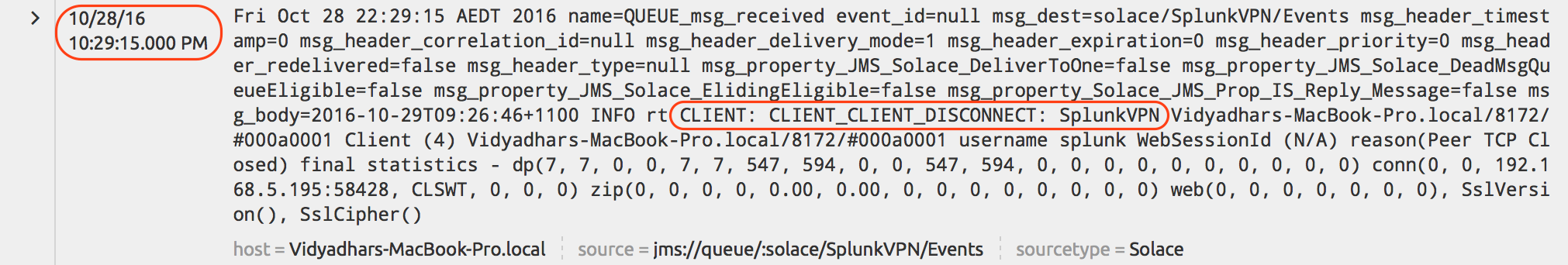
solace jms splunking
Splunk is a powerful log database that can be used for searching, monitoring, and analyzing machine-generated big data through a web-interface. Splunk Search Head : Provides web interface for for searching, analyzing and reporting. In this tutorial, we will be going to learn how to install Splunk
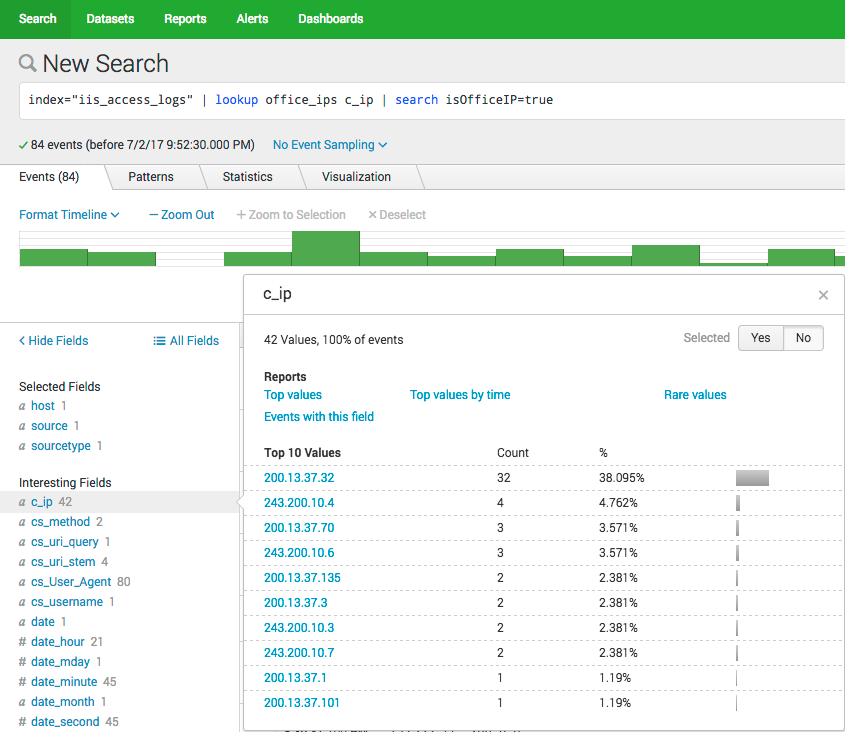
lookup splunk command access range ip logs
And here Splunk enjoys the reputation of being the "de facto Google of log searches." But this is changing as well. One of the first challenges users face (especially those who have been using Splunk for years) is how to export and where to store data.
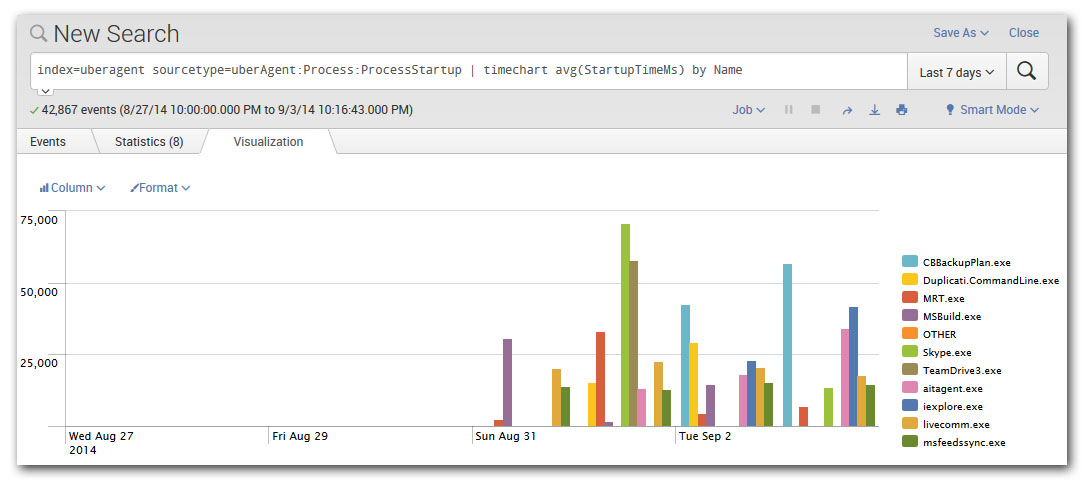
splunk chart sources data does ons apps klein
Splunk Enterprise, Splunk Light, or Splunk Cloud version or later. Splunk Connect for Docker plugin is not currently supported on Windows. For customers deploying to Splunk Cloud, HEC must be enabled and a token must be generated by Splunk Support before logs can be ingested.
In this article, we will show how to install Splunk log analyzer and how to add a log file (data source) and search through it for events in CentOS 7. Splunk is a powerful, robust, and fully integrated software for real-time enterprise log management to collect, store, search, diagnose and report
Today, let us see how to use Splunk Log Driver. 3. Eventually, we enter index="main" in the search box. Now, we can see the logs in the Splunk log collector. [Stuck with the procedures?
1 Splunk - Calculate duration between two events 2 Useful Splunk search functions ... When you are debugging an application, you may need to extract some data from logs (like an id in an ). To help you to do that, Splunk has the rex command.
Splunk search and reporting on Amazon FSx for Windows File Server audit logs. To simplify the search queries, you can install the Splunk add-on for Microsoft Windows. Select Install and then enter your user name and password, accept the EULA conditions, then log in and install.
Application logs can be accessed through Splunk. To start a new search, open the Launcher menu from the HERE platform portal and click on Logs The Splunk home page opens and you can begin by entering a search term and starting the search. For more information on performing a
Logging - How to find duplicate log events in Splunk ... best I'm trying to query my Splunk logs to find duplicate data, but am unable What information of How To Search Splunk Logs will be provided besides the login link? For each search from the user, besides the login link, we

splunk audit cloudhsm hsm
How Splunk Works: Stages in the Data Pipeline. Splunk is a distributed system that ingests, processes and indexes log data. Data Search - at this stage Splunk enables users to query, view and use the event data. Based on the user's reporting needs, it creates objects like reports, dashboards and alerts.
Choosing between Elasticsearch vs Splunk is a tall task. Learn about these two technologies and find which is right for your team. See how SentinelOne works with trusted names worldwide to enhance programs, process, and technology.
force-magic: no # force logging magic on all logged files. Then from the splunk UI just go to the application section (App: Search and Reporting -> Manage Apps) After that's installed, let's create a suricata type to parse the JSON file (as described in Suricata and Ulogd meet Logstash and Splunk)

splunk log analysis why analytics should visualization advantages
We will explain how to setup splunk server on a local environment and how can we feed splunk in with container(s) logs. After you completed this post, you will be able to understand basic concept of docker logging driver and how to use it.
