The splunk logging driver sends container logs to HTTP Event Collector in Splunk Enterprise and Splunk Cloud. Usage. To use the splunk driver as the default logging driver, set the keys log-driver and log-opts to appropriate values in the configuration file and restart Docker.
splunk log solutions management
splunk network
Search for events in Splunk by using the following query: source="http:VCNFlowlogs". This post shows you how to configure a low-overhead and highly scalable data pipeline to stream your valuable VCN flow logs to your existing Splunk Enterprise by using Oracle Functions and Events alongside
Splunk — Download and Follow the Splunk installation on Linux https Select App Context to Search & Reporting and Select Allowed Indexes to Events, Metrics and Objects. Review Page appears as below and submit for HEC Token to be generated.

splunk log analysis why analytics should advantages visualization
I have one of the another machines sending logs to this ubuntu the splunk interface i have added in the network ports as UDP port also have added in the "file and directory" /var/log. The client has also been configured do I show analysis of the logs??
In Splunk I want to search for any exceptions EXCEPT concurrent timeout exceptions. Concurrent timeout exceptions appear in the logs as either Splunk will find all of the exceptions (including those that contain "concurrent timeout exception", which is expected) that do not
In this article, we will show how to install Splunk log analyzer and how to add a log file (data source) and search through it for events in CentOS 7. Splunk is a powerful, robust, and fully integrated software for real-time enterprise log management to collect, store, search, diagnose and report
splunk architecture enterprise forwarding benefits data devopsschool slides
How do I use a Splunk log driver with an Amazon ECS task on Fargate? 1. Connect to your Splunk Cloud account. 2. In the navigation menu, choose Search. Now, you can see your logs in the Splunk log collector. Note: You can follow the preceding steps to create a task definition in
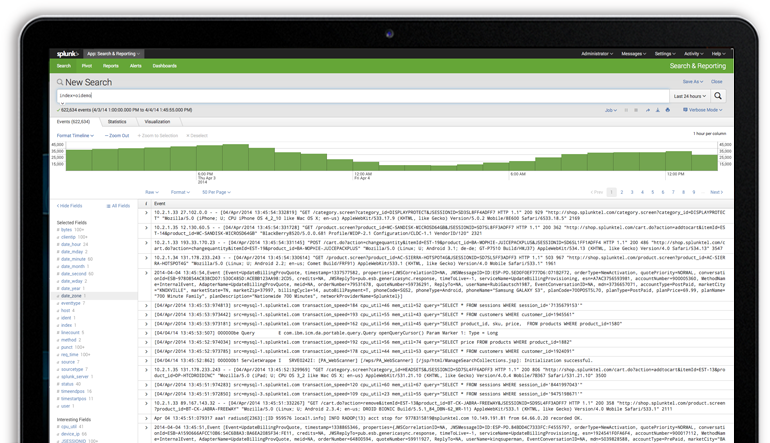
Splunk - Basic Search, Splunk has a robust search functionality which enables you to search the entire data set that is ingested. This feature is accessed through the app named as Search & Reporting which can be seen in the left side bar after logging in to the web interface.
In this Splunk Architecture blog, you will learn what are the various Splunk components & how they interact with each other to perform various operations. Splunk Forwarder is the component which you have to use for collecting the logs. Suppose, you want to collect logs from a remote machine,
Logging - How to find duplicate log events in Splunk ... best I'm trying to query my Splunk logs to find duplicate data, but am unable Search Application Logs Application logs can be accessed through Splunk. To start a new search, open the Launcher menu from the HERE

splunk dashboard sample example report firehose io using docs tanzu vmware nozzle data
2. Configure Splunk HEC input. Now that you have flow logs being recorded, we'll start setting up 3a. Create Lambda function using the "CloudWatch Logs to Splunk" Lambda blueprint from AWS After few minutes, you should start seeing events in Splunk Enterprise. You can search by sourcetype.
splunk competitors brandongaille waves making
To leverage those logs effectively, you need great search. When you're troubleshooting an issue, you don't have time to comb through logs line by line. It's designed to work in enterprise environments with lots of data. If your team is serving 5,000 requests per day, plugging in Splunk can be a little
Other than log centralization, Splunk provides following benefits too. Insanely fast search: whether we're searching keywords, key value pairs or regex patterns Easy to read results: can create custom tags for spotting important events; can view logs in raw format or in table view for easy interpretation.
The following short tutorial explains how to install Splunk server (on Windows or Linux server) and how to use Python to programmatically query Splunk and visualize Apache data by plotting them on a graph by using the Matplotlib library. In this post, show step by step, how to add Apache logs

splunk log analysis data worth inc enterprise software why screenshot management should beats expectations again proves its start source infrastructure
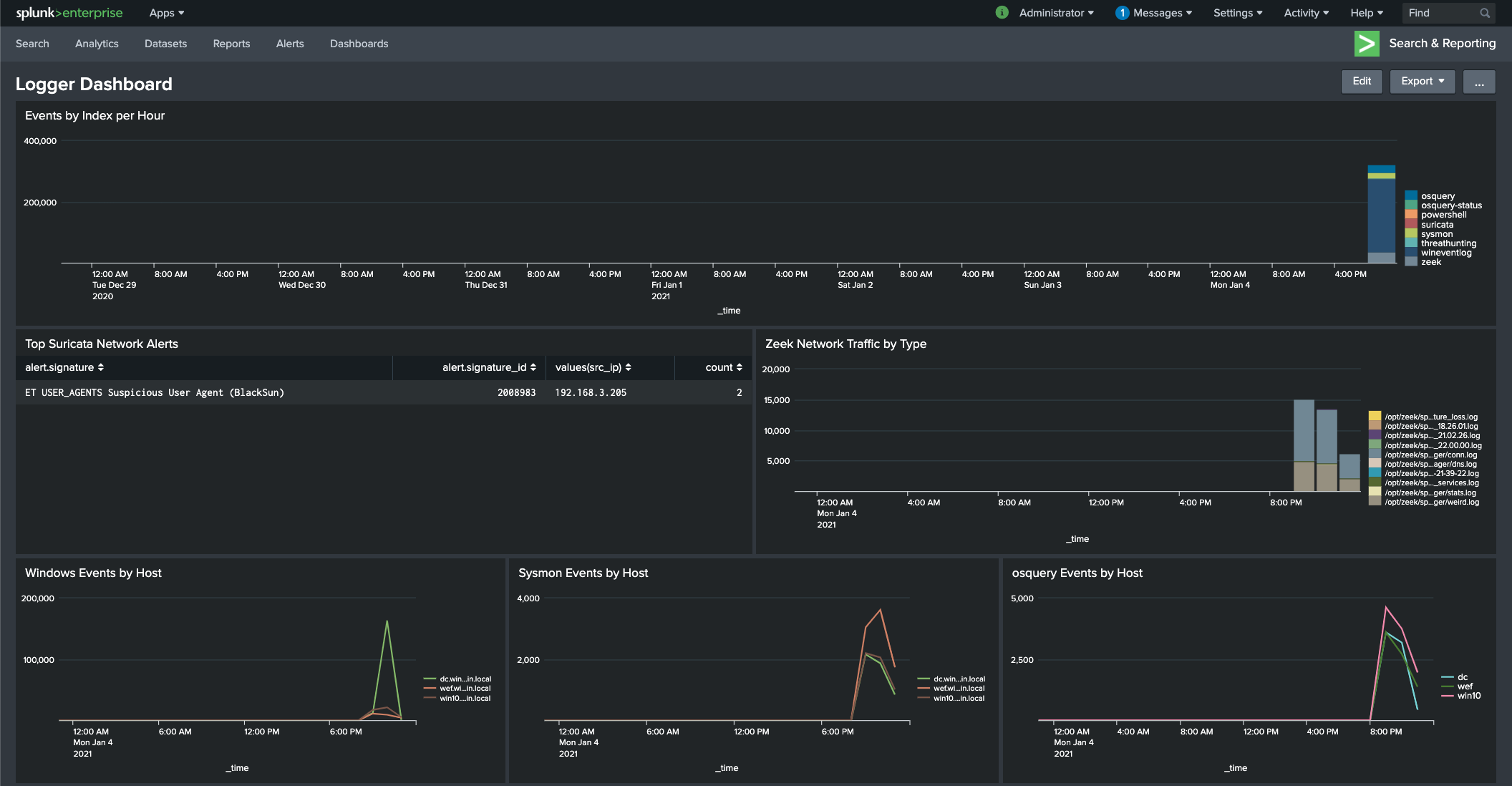
I decided to use another tool to visualize the suricata events. Recently I started using ELK but I still kept my Splunk setup just for comparison. Enable JSON output for Suricata. This is covered in Eve JSON
In this video we demonstrate how to perform basic searches, use the timeline and time range picker, and use fields in the Splunk Search & Reporting app.
Application logs can be accessed through Splunk. To start a new search, open the Launcher menu from the HERE platform portal and click on Logs (see Any single log line exceeding the allowed limit of 900 KB will be discarded and will not be available in Splunk. For more information on using
Learn about monitoring Vault telemetry metrics and audit device log data, including configuration and key metrics. A hands-on scenario is included with The following are details about the audit device log data and how you can effectively search them in Splunk. Get to know the key fields accessible
Splunk Data Sources. Splunk provides a wide range of plugins to support various resources. For example, to understand Windows event logs, it provides one plugin. For understanding Ubuntu machines logs, it provides different plugins. Based on the analysis of
Threat hunting in Windows event logs can be tricky. This tutorial shows the examination of process creation logs and Splunk for analysis. Windows event logs are, in a word, complicated. There are so many things that can be captured by Windows, it's hard to know where to begin if you're trying to
This tutorial describes how to install and use Splunk Connect for Kubernetes to collect logs from splunk-kubernetes-metrics: kubernetes: insecureSSL: true splunk: hec: indexName: metrics EOF. Browse to Search in the Splunk Web UI and search for the sample app's logs in the events index
1 Splunk - Calculate duration between two events 2 Useful Splunk search functions ... When you are debugging an application, you may need to extract some data from logs (like an id in an ). To help you to do that, Splunk has the rex command.
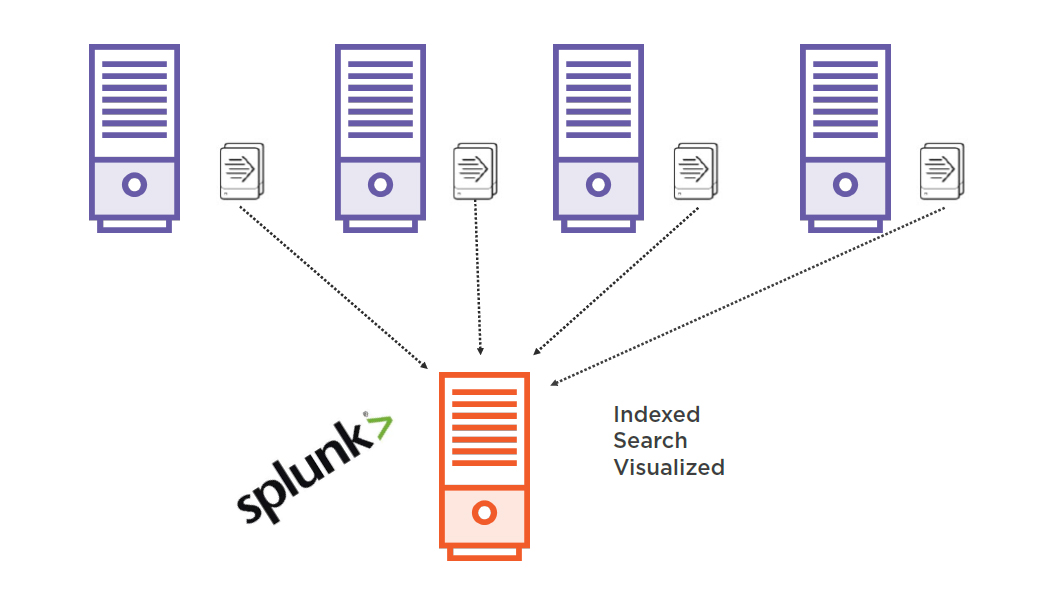
How does splunk work? Splunk pulls data from different sources and stores it in a repository form where it is able to generate graphs, business statistics, develop alerts and visualizations. It stores the data very efficiently, to be used later for developing reports and analyzing the system performance.
Tweet. One of the most powerful features of Splunk, the market leader in log aggregation and operational data intelligence, is the ability to extract fields while searching for data. Unfortunately, it can be a daunting task to get this working correctly.
Such as: management, log collection, web UI/search head and use separate IPs for different major sourcetypes. All of this makes your Splunk deployment Perform integrity checks. Splunk is incredibly precise in how it collects and represents your data; however, if you send it bogus or duplicate data

splunk buckets indexer understanding
Prerequisites Install and configure Splunk Connect for Docker Step 1: Get an HTTP Event Collector token Step 2: Install the plugin Install the Plugin from Docker Store Install the plugin from the tar file Step 3: Run containers with the plugin installed Examples Step 4: Set Configuration variables How
How Splunk Works: Stages in the Data Pipeline. Splunk is a distributed system that ingests, processes and indexes log data. There are a few common topologies for distributed search in Splunk: One or more independent search heads to search across indexers (each can be used for a different type

splunk observability techpark conquer
