Protecting against the spear phishing threat requires companies to deploy security solutions that identify and block phishing attacks before they Training employees on the warning signs of phishing emails and how to properly respond to them is essential to managing the spear phishing threat.
How do we prevent spear phishing? Spear phishing can be blocked with a strong defense system like those offered in Paubox Email Suite Plus, which impedes such techniques as spoofing while providing up-to-date protection with advanced threat detection features like ExecProtect.
Spear-phishing is among the most popular cyber-attacks used by criminals today. Find out more about this social engineering attack and how to defend against it. The UK's National Cyber Security Centre (NCSC) defines spear-phishing as "where the phisher is deliberately attacking a specific person
7 Ways To Protect Against Spear Phishing Attacks. Here are some of the steps you should take for spear phishing prevention. How do you safeguard your business from spear phishing attacks? Feel free to share it with us in the comments section below.
5 common phishing scams, and how to protect yourself from them. Since phishing scams are designed to appear as if they come from reliable sources, it is smart to know the difference between real and fraudulent messages and how to spot some of the clues that a message may be a scam.
How does spear phishing work? Spear phishing usually targets enterprises, as a large majority of their data is available online which can be mined The first line of defense to protect yourself against scammers and hackers is to educate yourself on the best practices in cyber security. If you're

phishing common attacks protect security deceptive against attack scam awareness spear them tripwire sherman which
How to protect yourself. One way to reduce the risk from spear phishing is use multi-factor authentication, which adds an extra layer of security by requiring not just a username and password, but knowledge or possession of something that only that user has, such as a code sent to a cell phone.
How to Avoid Spear Phishing. The threat of these scams is real. Even if you haven't felt it first-hand, we can see that the matter is urgent, considering 2. Protect Your Privacy. Spear phishing attacks are custom-tailored because the criminals manage to piece together a lot of personal information
How to Protect Your Business from Spear Phishing Attacks? Here are some more advanced tips on how to protect from spear phishing attacks
How to Protect Yourself against Spear Phishing. If you're concerned about the danger of spear phishing attacks or looking for ways to make your environment more secure, we suggest you implement these seven steps in your company. They may help stop a potential attack before it
Spear-phishing attacks are harder to detect than most other kinds of cyber attacks - a link or form from a cybercriminal can look identical to the authentic More important is teaching your employees how to avoid common cyberattacks like phishing attacks. 65,000 users were affected by this most
Spear phishing tactics use trust to scam victims. Find out about spear phishing attacks, including examples and tips for preventing an attack. What spear phishing is (with examples) and how you can avoid it. Spear phishing can be the cause of huge financial losses, both for individuals
Spear phishing, if executed in the right way, can be more dangerous than all the malware in the world combined. What exactly is it and what can you do to protect yourself Read Also: 4 Data Protection Tips To Keep Your Data Secure On-The-Go. How to Protect a Business from Spear Phishing.

phishing anti virus examples software computer methods firewalls include howstuffworks
Spear Phishing Protection - Definition & How To Recognize Spear Phishing Email. Spear phishing is the act of sending fraudulent emails that appear to be from a known or trusted sender in order to obtain Read an article here for detailed info on 'What helps protect from Spear Phishing'.
How to Defend Against Spear Phishing. To protect against this type of scam, organizations should conduct ongoing employee security awareness To protect against vishing attacks, users should avoid answering calls from unknown phone numbers, never give out personal information over
How does spear phishing work? Spear phishing email attacks are more sophisticated in nature compared to phishing attacks because they are Are you wondering how to prevent spear phishing attacks to protect your users and their private information? Fortunately, there are a number

phishing spear protection diagram barracuda sentinel domain fraud

phishing emails scam expert hackers hacker hat usa clicking tricked even got
"Spear phishing is the act of sending and emails to specific and well-researched targets while purporting to be a trusted sender. Cyber security expert recommended that use a strong and smart password in order to protect from spear phishing attack.
In this video we are covering spear phishing. What is spear phishing? How do I protect my organization against spear phishing attacks?To learn more
How Does Spear Phishing Work? Spear phishing usually takes the guise of in-house emails, asking employees to fill in credential requests. Apart from spear phishing and whaling, another interesting phishing approach is the… rose phishing, although it's not as common as regular or spear phishing.
How to identify spear phishing. So, what does a spear phishing attack look like? Is there a way to recognize the bait? Email is the preferred medium of spear phishers. Let's learn how spear phishing works so you can defend yourself effectively against this treacherous form of online crime.
Spear phishing is an evolution of this phenomenon — online attackers target prey like fishermen with a sophisticated ploy that works like a proverbial spear. Rather than sending out a mass number of e-mails and seeing what comes back, spear phishers have a specific target in mind.
Spear phishing attacks continue to increase in popularity among cybercriminals, and businesses must take steps to protect against them or risk seeing Spear phishing attacks are particularly dangerous because they are designed to get around traditional email security like spam filters, the report found.
Learn how spear-phishing emails are crafted to infiltrate your network and how to protect against them. (video - 3:46 min). Spear-phishing attacks are delivered via a standard approach: email . They appear as ordinary emails. The body of the email may contain a link or an attachment.
Spear phishing is different from other forms of phishing because, in this case, the perpetrator already has some first-hand information about the target right before they attack. Thankfully, there are actionable steps you can take to protect yourself from spear phishing and related attempts, such as
Spear-phishing attacks: why they are successful and how to stop them. Putting spear phishing best practices into place can make a significant difference to your cybersecurity. For flexible per-user pricing, PhishProtection's integrated email security solution protects your employees from

phishing infographic statistics facts threat rising attack businesses graphic security attacks identify social numbers physical inspired infographics impact wallace david

phishing phish emails phishme sophos spear whaling annually sottrazione ransomware safely techzine traint werknemers contromisure pymnts knowbe4 cofense corrispondenza convivente

phishing types attack prevent login scams security phish hackers attempts retailers account services nextgov identifying

phishing spear
And how can individuals and enterprises protect themselves against such an invasive tactic? Spear phishing attacks usually appeal either to human greed or fear. This means they will either offer targets money, discounts, bargains, etc. or threaten targets into acting by saying their checking, PayPal,
So what exactly is spear phishing? How can MSPs recognize spear phishing attacks before it's too late? With such alarming numbers, it's clear that security experts have a duty to better educate their customers about spear phishing to protect them from falling victim.
Learn more about spear-phishing prevention and how organizations can protect against critical spear-phishing attacks! Spear-phishing comes in many forms, as fraudsters work across email and other communications channels to steal from your company.
Spear phishing has been associated with most of the largest cyberattacks in recent history including the attacks on JPMorgan Chase, eBay, Target, Anthem, Sony and various To learn more about how Duocircle can protect your small or mid-size business from spear phishing attacks, click here.
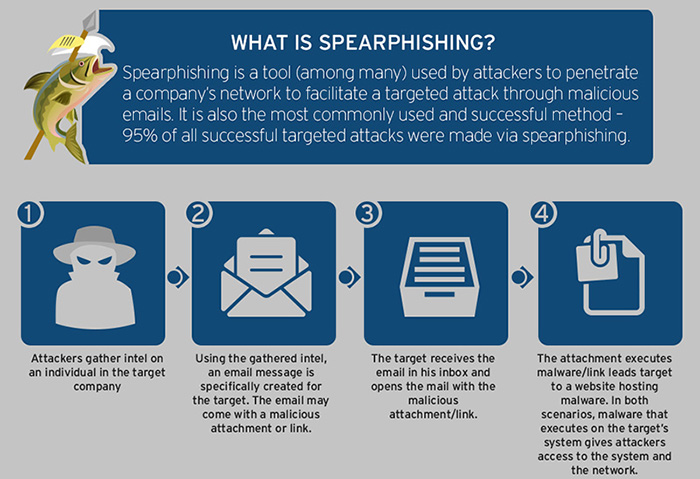
phishing spear security cyber attacks infographics micro trendmicro trend
