
congo basin oyo brazzaville memorandum fund river understanding protect signed prnewsfoto efforts economies warming contribute reduce improve global local prnewswire

theft identity preventing security uncategorized mar
Data in motion is also known as data in transit or data in flight. Data in motion is a very important part of big data analytics. Processing this data in real time can help an organization analyze the latest trends as they are 8 Ways to Avoid Death by PowerPoint: How to Make A Slide Deck Shine.
Cryptography was invented to protect communications: data in motion. This is how cryptography was used throughout most of history, and this is how the Even when cryptography was used to protect stored data — data at rest — it was viewed as a form of communication. In "Applied Cryptography,"
Protecting data at rest is far easier than protecting data in use -- information that is being processed, accessed or read -- and data in motion Encryption plays a major role in protecting data in use or in motion. Data should always be encrypted when it's traversing any external or internal networks.
Data in motion security with respect to organizations. Data in motion can be broadly classified into two categories. The first is virtual information transferred How to protect data in motion? Identify and classify the types of data. Within an organization, numerous types of data can exist, such as
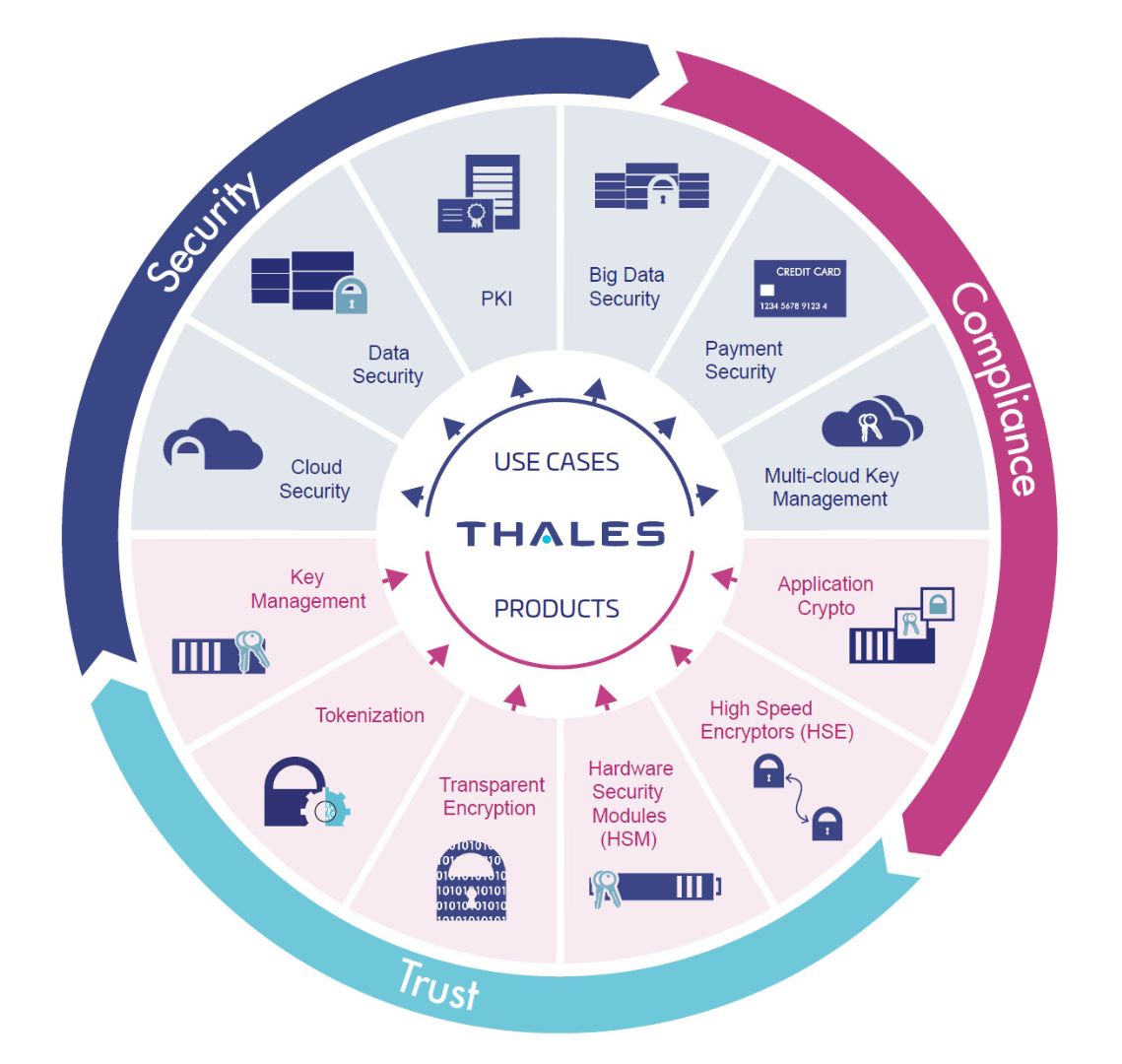
thales encryption
Data is the most valuable asset you control. Losing intellectual property, a customer's personally identifiable information (PII), financial information, and Now, more than ever, it's important to protect your data in motion and at the file level. In our environment today you need to be able to classify

infrastructure diagram visio network services technology templates template management structure architecture diagrams process mapping creately networking system networks data speed
It achieves full information protection for data confidentiality, and maintains all the advanced features of the original JPEG2000 codestream such as Security of Data is the most important task in today's world. Over the years various encryption schemes have been developed in order to protect
How Data in Motion is enhancing customer experiences. By leveraging a potentially unlimited variety of data sources, Data in Motion's XaaS platform engages customers across all channels, providing real-time insights into what they are feeling in the moment, and reshaping the future of a
Data in motion indicates data that is transitioning from storage, such as a file or database entry, to another storage format in the same or to a different Data may be cached on intermediate systems, or temporary files may be created at either end point. The best method to protect data in motion is
Protecting Data In Motion. 429 просмотров • 12 дек. 2013 г. • It is not uncommon for end users to forget to apply protection to sensitive information before distributing You will see how you can apply automatic protection of sensitive content through transport protection rules and data loss prevention.
The difference between data in motion vs. data at rest can determine the technology and processing capabilities required to glean insights from the data. For data at rest , a batch processing method would be most likely. In this case, you could spin up a bare-metal server during the time you need

users fast class move width wiggers kyle
3 Intro 4 Data-Centric Security 5 How to differentiate? Data-centric security focuses on the protection of data itself and is based on two principles Data Protection Risk and Impact Assessments The threats to personal data and cardholder data are changing constantly.
Protect data in motion without additional hardware or modification of applications. Satisfy compliance requirements with ease. Data in motion encryption allows you to minimize risk in your organization, but a solution like Illumio Core takes this a step further without the need for manual configuration
The Lenses Data Policies module can protect data in motion. As a user, you can track, secure and Data protection of sensitive or classified data is not a new problem. Analyzing and acting on data Policy Name - A short description to say what the policy is for. Redaction - How to protect the data.
What is data loss prevention? This article explains how it works, why it matters and the types of DLP Data loss prevention processes are information protection practices designed to protect sensitive or Enterprise data can be at rest, in motion or in use, and each state involves different vectors
The data is protected while residing on the device or hard disk, but is no longer protected once it is extracted from the device (copied to another device MDM (Mobile Device Management): One way to control data in mobile devices is through MDM tools. They allow limiting access to certain
Data in motion can be data sent from desktop to cloud, portable devices or other exit points. Once the data arrives at its final destination, it becomes data at rest. In the following, this article takes a close look on how data in motion can be best protected in order to avoid data breaches.
Data in motion is data that is being transmitted over a network. The biggest threats to data in motion are interception and alteration. Data in motion is particularly vulnerable to attackers because the attacker does not have to be Encryption tunnels can protect data along the path of communications.
data and platform protection in cloud implementations • Provides guidance on encryption to protect data • Describes the importance of a trusted foundation 12 Step 3: Four Things an IT Manager Can Do to Mitigate Security Vulnerabilities. 13 Step 4: Protect Data—in Motion, in Process, and at Rest.

jeremy ipad iphone way code class special alt apple
Data security - protecting data from malicious or accidental damage. Data availability - Quickly restoring data in the event of damage or loss. Data protection laws in Australia. The Australian Prudential Regulatory Authority (APRA) introduced a mandatory data privacy regulation called
Securing data at rest also should be complementary, rather than a replacement, to securing data in motion. The vast majority of data in motion moving Seagate has put no security back doors in the. 12 SED. How to Protect Data and Reduce Drive Retirement Costs. Performance at Full Drive
This data must be protected in motion and at rest. Personal data10 is data (or information) that can identify It must be protected to ensure its authenticity and reliability. Data-at-Rest vs Data-in-Motion vs The IISF provides guidance on how to consider motivations for security, including
Data in motion can be data sent from desktop to the cloud, portable devices, or other exit points. Once the data arrives at its final destination, it becomes data In the following, this article takes a close look at how to protect data in motion to avoid data breaches . 1. Identify critical assets and vulnerabilities.
Data security, includes the security of: Data-in-transit. Data-at-rest. And the right storage mechanisms should be chosen for storing these data. The most common way to protect data in motion is to utilize encryption combined with authentication to create a conduit to safely pass data.
Learn how to analyze fast-moving data streams on the fly with event stream processing. Managing data in motion (streaming data) is different from managing data at rest. Event stream processing relies on three principal capabilities - aggregation, correlation and temporal analytics - to deal with data
Data encryption, which prevents data visibility in the event of its unauthorized access or theft, is commonly used to protect data in motion and increasingly Tokenization is a non-mathematical approach to protecting data at rest that replaces sensitive data with non-sensitive
That depends-how much data can you afford to lose if your system crashes completely? You can protect data you want to share with someone else by encrypting it with the public key of its #8: Protect data in transit with IP security. Your data can be captured while it's traveling over the
Protecting your digital privacy is a wide spectrum, so whether you're the person who simple wants to avoid the commercial exposure and release (either legally or illegally) of your personal information on the internet or the person needing to protect (and secure) their privacy from unwanted attention,

They uniquely protect data-in-motion and data-at-rest in ways that help organizations reduce costs, streamline and secure operations, and perform more Recent data breaches illustrate how encryption fails to adequately secure data-at-rest. These violations will certainly increase in frequency as
Data in transit, or data in motion, is data actively moving from one location to another such as across the internet or through a private network. Data can be exposed to risks both in transit and at rest and requires protection in both states. As such, there are multiple different approaches to
So how is using environment variables better than defining secrets in source code? Doesn't this mean the application is still at risk? The simple fact is that client-side data in the browser cannot be adequately secured and at best this technique only keeps sensitive data out of plain sight.
