Insider threats hurt every organization. Learn how insider threats happen and give your Insider threats are threats from people with access to systems and inside information about your *** Share This Section on How to Protect Against Insider Threats with Your Employees ***.
Five More Essential Tips For Protecting Against Insider Threats. How safe are their systems? What safeguards do they have in place? Your security may be tight, but infiltrating a business you partner with may give a malicious individual the opportunity to damage your organization or steal
How to prevent insider threats? Include training on insider threat awareness for employees. Since not everyone is knowledgeable about cyber threats, it is crucial to educate your Here's a list of programs you need to protect your organization: Endpoint protection system.
Insider Attacks: How to Use Artificial Intelligence to Prevent Insider Threats Webinar. Microsoft shares tips on how to protect your information and privacy against cybersecurity threats.
When creating an insider threat program, you want to make certain you can maintain a healthy security culture. It's important to be transparent about the nature of your insider threat program. First, it's essential to establish the proper protocols for good data management, including how and
The term insider threat refers to the threats that organizations face from employees, former employees, business Anger/Revenge: Disgruntlement to the point of wanting to retaliate against the organization. Employees are not trained on how to properly protect proprietary information.
What Threats Are You Up Against? Insider threats cover a broad range of different activities and can come from anyone in your organization. Work with HR and legal to protect the privacy and rights of any individuals suspected of being an insider threat. Prepare for future data leaks and put that
To help organizations better protect themselves against insider threats, Code42 offered the following recommendations in its report: Security teams must evolve their data loss protection strategies and think beyond prevention - prevention solutions aren't enough to stop insider threat.
Nevertheless, considering the cases related to the insider threat in the past few years, it would be negligent for an organization to disregard the threat of somebody intentionally exploiting the position of trust or Emmanuel Zidafamor (2015.). Management Methods To Protect Against Insider Threats.
Before explaining how healthcare organizations can protected against insider threats, it is worthwhile covering the main insider threats in healthcare. An insider threat is one that comes from within an organization. That means an individual who has authorization to access healthcare
Insider threats can be challenging to identify and even can be even harder to stop them from causing harm. By following best cybersecurity practices. Employees should be prepared to recognize phishing and other social media threat vectors, as well as how outside attackers might approach them.
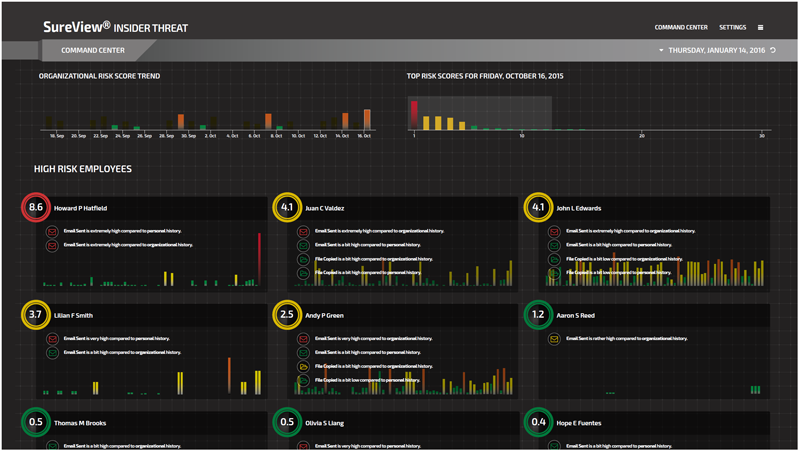
threat insider sureview forcepoint command center risk trend

questions tests checkpoint adjust gave
A guide to balancing external threats and insider risk. Natalia Godyla Product Marketing Manager, Security. Dawn Cappelli Vice President and Chief Information The security community is continuously changing, growing, and learning from each other to better position the world against cyber threats.
radar under threat insider
Data Protection 101. How Does UEBA Protect Against Insider Threats? Learn about how User and Entity Behavior Analysis, or UEBA, works and how it leverages machine learning to help mitigate insider threats, password attacks, and more in Data Protection 101, our series on the
Protecting against insider threats is something all businesses have to manage and is an ongoing process. Shareth Ben, Insider Threat SME at Securonix, discusses a best practice approach for detecting and protecting against insider threats, as well as bringing awareness to the different types.
Many, if not most, insider security threats to businesses come from employees who are poorly trained, careless, or in search of a convenient shortcut, not from employees with malicious intent. Take a look at what you need to know about protecting against and dealing with malicious insiders.
While insider threat may not be malicious, an insider attack, simply put, is an attack executed on a computer system by an insider with malicious intent who has authorized system access. In most cases, there is less security against insider attacks because many organizations focus on protection
While large breaches involving consumer personally identifiable information make the headlines, insider theft of intellectual property and other confidential data can threaten an organization's very existence. Jan 12, 2018,07:30am EST|. How To Defend Against Insider Threats.
Insider threats could cost your company hundreds of thousands of dollars and hurt the trust you once felt with your employees. While most companies have adequate strategies in place to protect themselves against outside threats, many lack a system that protects the company's assets
Protect Against Insider Threats. Get real-time insight into threats that can cause data loss and brand damage. According to the recent Verizon Insider Threat Report, "Regular users have access to sensitive and monetizable data and are behind most internal data breaches."

phishing cyber attacks start against protect
As infrastructure communities work internally at protecting against insider threat and share lessons learned, they can protect the Nation. The key steps to mitigate insider threat are Define, Detect and Identify, Assess, and Manage. Click on the icons below to learn more about each step.
worry
Defining insider threats, identifying their source and describing measures to protect against them. Insider threats come from users who have authorized and legitimate access to a company's assets and abuse it either deliberately or accidentally.
Insider threats are a real danger as well and should not be overlooked. Implement Prevention Training for Insider Threats. Training about how to identify the difference between malicious emails and legitimate ones is a vital part of this employee education.
How PAM protects against insider threat. The most important accounts to keep track of are the ones with elevated admin rights to sensitive corporate systems. Best-in-class PAM solutions such as the WALLIX Bastion offer a range of ways to protect against insider threat.

threat cybersecurity threats ninety overview insiders
The Insider Threat Profile. Insider Threats are categorized in three ways. The most dangerous are your malicious insiders. Implement technical controls. Create and enforce physical security measures. How to Defend Against Insider Threats. So how do we protect ourselves from insiders.
Insider threats can be managed by policies, procedures and technologies that help prevent Understand how the service provider's data security works. Identify and confirm the responsible Work with HR to develop strong user termination procedure to protect your organization legally and Train and test your employees against social engineering attacks, active-shooter situations and

threat breach
maltego
How To Protect Against an Insider Attack: Best Practices. Imperva recognizes that user behavior analysis is key to protecting against insider threats, but is not enough. We provide a stack of solutions that not only monitors how users move through the network, but also protects assets on
Insider threats aren't just employees, they can also be contractors, vendors, or even volunteers that come in and work in the organization. Encrypting data, enforcing two-factor authentication and physical security are few of the common themes in protecting against today's cyber-threats.
Insider threats are on the rise. Some of this trend may be because more insider breaches are Protect: The zero-trust model is based on the assumption that no one can be trusted, so people aren't given Discover how Fortinet Teleworker Solutions enable secure remote access at scale to
Against this type of threat, the best technical defenses must address the ability for data to be removed from the organization. For any organization, Edward Snowdens are the worst case scenario — an insider with deep privileged access, high-level technical skills, and no desire to protect their identity.

threat
