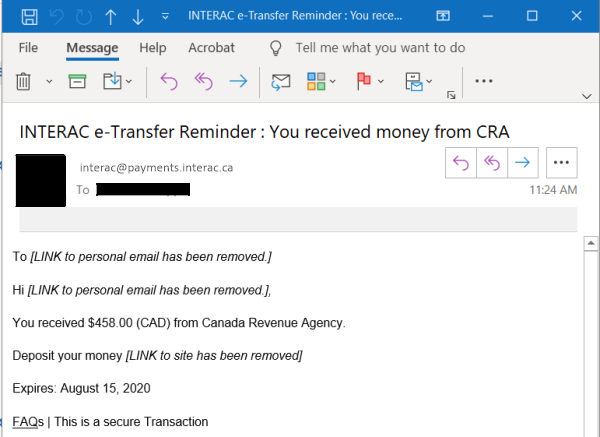
cra fbc
We've all come across spoofed emails at some point, and they are a real threat to the security and safety of our organizations and its employees. In this article, I'd like to explore what email spoofing is, how you can detect rogue emails on your network, and how you can take steps to safeguard
Protecting against email spoofing is therefore so important. But thankfully, there's plenty you and your business can do to stay safe. Another way to give your employees a helping hand to stay protected against these kinds of emails is ensuring firewalls are turned on.
Email Spoofing - a form of email fraud in which a malicious actor sends an email with a fraudulent "From" address - is a tactic frequently used in phishing While the SPF, DKIM and DMARC protocols are instrumental in protecting against attacks that leverage sender fraud, they are not a "silver bullet"...

techrepublic malicious shortened
Email spoofing is the sending of email messages with a forged "from" address. Using a spoofed email address is common tactic email scammers use to gain the trust of their victims. You need to make sure the emails your website and organization sends are marked as authentic.
Protect against phishing & prevent messages from being marked as spamUse Sender Policy Framework (SPF) to help protect your domain against spoofing, and help prevent your outgoing messages from being.
Email spoofing is sending an email with a falsified email address. How to prevent email spoofing with SPF? It comes in the form of a simple TXT record in the DNS records with the list Although SPF alone will not provide ultimate protection against malicious actors, it is a very important step towards it.
Spammers have been spoofing email addresses for a long time. Years ago, they used to get contact lists from malware-infected PCs. That means that any email host that tries to conform to the rules of DMARC wouldn't have any instructions on how to handle SPF failed emails, and would probably

scams phishing
Learn what is spoofed email, how to stop email spoofing and recognize such spam messages. Perhaps the simplest way how to identify email spoofing is to manually check email headers. In addition to SPF, there are several other effective countermeasures against email spoofing,
Email authenticity is a major concern for a lot of customers and one of the best ways of addressing this is by adding SPF and DKIM Records. Both these techniques can be used to prevent email spoofing.
SPF is both useful for protecting against MailFrom spoofing of your domain towards your users but also to external destinations where it could harm You send an email to a generated email address and then can see a report of how this email was scored, whether SPF and DKIM checks
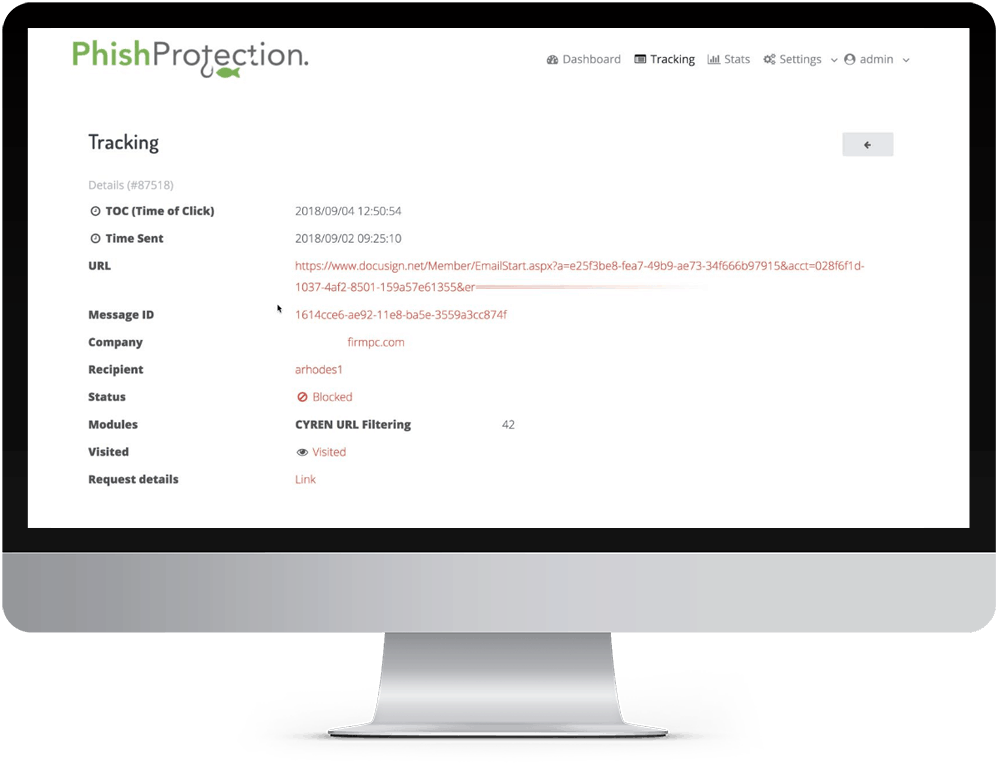
blocker spoofing
Find out how you can protect your organization against these convincing phishing attacks. Spoofed email phishing scams can be hard for end users to identify. The scams involve sending a phishing email to a user and making the email appear as if it has been sent by a known individual.
Protect your organization from email spoofing. Email spoofing is a highly damaging and increasingly frequent form of cyber fraud. Defending against email spoofing requires a multilayered approach to security. Users, often the weakest link, must be empowered with knowledge and best practices
To experience how SolarWinds Mail Assure can help protect your inboxes from cyber threats, start a trial today. Mia Thompson is product marketing manager Technologies of Trust: Protecting Against Email Fraud and Scams Infographic. Email has long been a top attack vector for cybercriminals.

education suite google updates tools every scan enterprise meet
threat defense advanced
Email spoofing is a technique scammers use to make fraudulent emails appear as if they came from a known entity in order to phish for sensitive information. Since spoofing is often the first step in a costly breach, your business has a major incentive to prevent these attacks before they occur.
But what is email spoofing—and how do you protect yourself against it? In order to prevent email spoofing, the Sender Policy Framework (SPF) was created in the early 2000s. SPF instructs every domain to specify a list of authorized IP addresses that can send emails from that domain.
How to Prevent Email Spoofing. Having someone else spoof your company's email address is bad for business, either because of losses or brand damage. Advanced spam filters to protect against sophisticated attacks; Fraud prevention system against Business Email Compromise
About this document What is Email Spoofing? Email Spoofing Defence Workflow Layer 1 Layer 8: Protecting Against Phishing URLs Layer 9: Augment Spoofing Detection Capability with However, the guidance of how to publish SPF, DKIM and DMARC records is beyond the scope of this document.

mimecast threat targeted

Email spoofing refers to when the sender of an email forges the header data in an email so that it appears to come from an address that is not the If the messages are not there, then your address most likely has been spoofed. This sounds like what's happened here, since these
Email spoofing is a technique for forging an email header to trick recipients into believing a sender is a familiar brand or acquaintance. It's a critical element of Why is email spoofing so difficult to spot? Consider the following example: You get an email from support@ asking you to
Business Email Compromise, which includes spoofing, has cost companies $ globally in the last two years Forged emails use a forged sender address
The anti-spoofing technology in EOP specifically examines forgery of the From header in the message body (used to display the message sender in email clients). When EOP has high confidence that the From header is forged, the message is identified as spoofed.
Email spoofing is a way in which anonymous spoof emails or spoof emails with a different name VPN services will not protect you against DNS-level attacks, nor will they prevent your site from In most cases, this is how spoofing works. The hacker is almost never able to create a perfect
Email spoofing is a technique used for spamming and phishing attempts. Learn two easy methods which prevent internal email spoofing in Exchange What is worse, fighting internal spoofing attempts requires a slightly different approach. I will now present how to prevent internal
Email spoofing is a serious & growing concern. Why? Because cybercriminals use it to impersonate others. 4. How to Stop Email Spoofing from Affecting Your Organization. Section also indicates that while there's an opportunity to bring a civil suit against the perpetrator, any civil
Email spoofing refers to the sending of email messages with a forged "from" address. This is a common tactic that cyber scammers use to gain the trust So, what do spoofers want, and how do you protect your email address from being spoofed in the future? That's why we're here: to impart
E-mail Spoofing and its relationship with Phishing. It is good to know that Spoofing email is like a bridge that allows the execution of whaling attacks. It is characterized by sending email messages with content or instructions to carry out actions for malicious purposes. The main difference is that
Find out what is email spoofing, look at email spoofing examples and learn how to protect your domain from malicious actors. When a malicious sender forges email headers to commit email fraud by faking a sender's email address. Email spoofing turns into a phishing attack when the

authentication mfa
How to Protect Yourself Against Email Spoofing. The Technical Way. Check whether the email passed a Sender Policy Framework (SPF) check. SPF, DMARC, and DKIM are authentication checks that happen in the background when you receive an email. Not all email domains have
Email SecurityProtect against today's advanced email threats. Cloud Security. Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions. Email spoofing attacks are on the rise. Cyber criminals are getting more skilled at faking domain names and using
Spoofed emails are emails where the sending address was forged by the real sender. You may have been contacted by someone claiming to have While there is no way to reliably stop spoofing in all circumstances, there are some technical tools you can use that allow email recipients to check if
