API, ; Application Programming Interface. Web applications hosted by your organization. We have already established that pentesting in AWS differs from traditional pentesting in terms of Related Guide - How to conduct Website Penetration testing. In a traditional pentest for a
API Pentesting notes. . Contribute to omkar-ukirde/api-pentesting development by creating an account on GitHub.
Android Applications Pentesting. iOS Pentesting Checklist. These kind of APIs may be vulnerable to XXE, but usually DTD Declarations are disallowed in the input from the user. Read this document to learn how to search and exploit Owasp Top 10 API vulnerabilities:
Penetration Testing tools help in identifying security weaknesses in a network, server, or web application. If unauthorized access is possible, the system has to be corrected. Following is a handpicked list of Top Pentest Tools, with their popular features and website links.
API Penetration Test using Burp suit is very popular. In this video, we have seen an example of how to configure Postman to use with Burp to perform
A penetration test is also known as a pen test and a penetration tester is also referred to as an ethical hacker. Automated tools can be used to identify some standard vulnerabilities present in an application. Pentest tools scan code to check if there is a malicious code present which can lead to
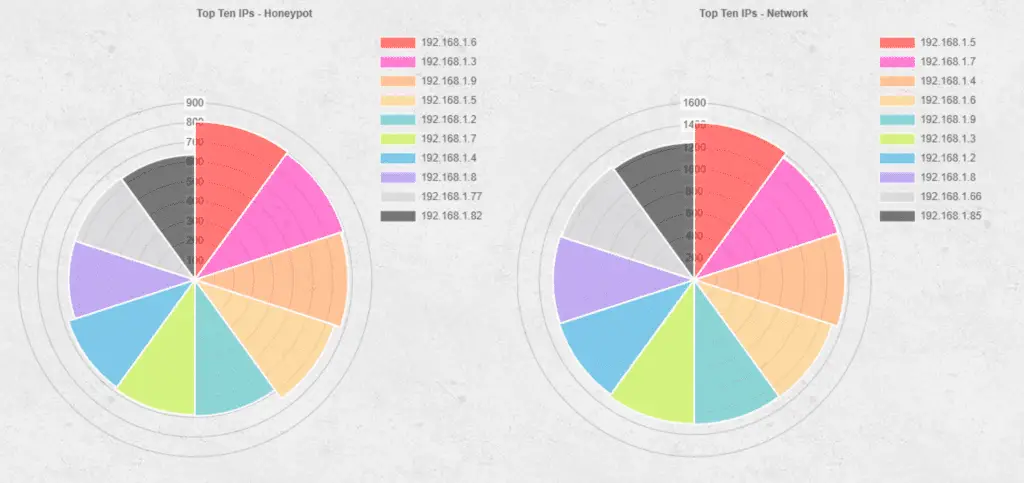
honeypot honeynet
Learn how to conduct pen tests to uncover weak spots and augment your security solutions and policies. Dynamic analysis - Inspecting an application's code in a running state. This is a more practical way of scanning, as it provides a real-time view into an application's performance.
Pen Testing REST API with Burp Suite. Introduction: Welcome to our 3-part blog series where we will take a dive into the technical aspects of conducting exhaustive penetration tests against REST API services, generating reports based on what tests were performed, and what our findings are.
API Penetration Testing is a mix of API schema review and black-box API Security Assessment mimicking real attacker. It is important to include in scope is Web Penetration Testing, where we exploit various functions of a web site - file uploads, input forms and others. Because we utilise

pentest
API stands for "application programming interface". Put briefly, an API consists of a set of rules describing how one application can interact with another, and the mechanisms that allow such interaction to happen. There are two primary benefits that an API brings

29, 2021 · API tests are distinct from GUI testing in that they do not focus on the appearance and feel of an application. It focuses mostly on the software architecture's business logic layer. API automation is a term that refers to the Testing that necessitates the use of an API-enabled application. To test an API, you'll need to do a few things.
pentest reporting. Get instant access to custom vulnerability scanners and automation features that simplify the pentesting process and produce valuable results. The platform helps you cover all the stages of an engagement, from information gathering to website scanning, network scanning, exploitation and reporting.
There's also "Advanced API Security - The Definitive Guide to API Security", but that comes out in September 2017. Can someone hit me up with some learning material on REST API pentesting? edit: I've set up Hackazon, but I just don't get to use the REST API, it will always tell me that
30, 2021 · A collection of resources, tools and more for penetration testing and securing Microsofts cloud platform Azure. - GitHub - Kyuu-Ji/Awesome-Azure-Pentest: A collection of resources, tools and more for penetration testing and securing Microsofts cloud platform Azure.
REST API provides the information that the developer provides in the API, that is, if you need to get more or less information than the API suggests After we have dealt with the basics, go directly to Pentest. How to understand that the application uses GraphQL? Here is an example query in

disassembler interactive plasma arm x86 mips generate syntax pseudo readable assembly colored write code
PwnDoc is a pentest reporting application making it simple and easy to write your findings and generate a customizable Docx report. The main goal is to have more time to Pwn and less time to Doc by mutualizing data like vulnerabilities between Documentation
I want to pen test rest apis, the use case I have is a client(desktop app with username and password) connecting to a server. Furthermore, I did some search on google I noticed postman is mentioned many times, I know it's a tool for building apis, but is it also used in the pentesting with the burp?
Building A Pentest Program To Prevent A Data Breach. Pentesting is the manual process of assessing an application or network for security vulnerabilities. However, today's pentesting market has transformed due to disruptive cloud and API technologies, as well as a faster and more
the right pentester talent needed for your assets, whether it be a web, mobile, or desktop app, API, network, or cloud services (AWS, GCP, Azure) Get …

packer pe amber reflective poc pentest
17, 2021 · Pentest Tools got more than 20 tools for information gathering, website security testing, infrastructure scanning, and exploit helpers. Miscellaneous Information In a situation where we need information on internet-connected devices such as routers, webcams, printers, refrigerators, and so on, we need to rely on Shodan.
API (application programming interface) testing is performed at the message layer without GUI. It is a part of integration testing that determines whether the APIs meet the testers' expectations of functionality, reliability, performance, and security. There are two broad classes of web service
API tests are straightforward. For those types of tests you're examining a backend service without a front end interface. As we've already covered before, an API pentest is different from a web We've also covered how to prepare for a pentest in general, so what's different when preparing for API tests?
Get expert insights with a command injection tutorial with insights from pentesting experts at Cobalt, a Pentest as a Service (PtaaS) provider. These kinds of attacks are possible when an application passes unsafe user-supplied data (forms, cookies, HTTP headers etc.) to a system shell.
• If REST API try to use as SOAP changing the content-type to "application/xml" and sent any simple xml to body. # Check if supports SOAP. Change the content-type to "application/xml", add a simple XML in the request body, and see how the API handles it.
I am trying to Pentest an application which is built in AngularJS. Here, Acunetix was bit helpful to give the brief idea how the application is parsing the contents. Yeah, at some point you'll see a comm leave for a back-end server or API but most of the logic and processing has been done in
Learn how to pentest REST APIs. Web or API Developers. Mobile Application Developers. Security professionals who are interested in REST API Security.
Similar to web applications, web APIs (Application Programming Interfaces) should undergo security testing to determine whether or not any vulnerabilities exist. How to Use Insomnia To Create Data for Pentesting.
What is Pentesting? Protecting your business through hacking is a complex and When it comes to pentesting, its actor - the pentester - simulates an attack against a Network That's not how it happens on a pentest, where you need to implement post-exploitation techniques,
Before starting with test, pen testers should have an better understanding of users, roles, resources & responses of each APIs to find cool vulnerabilities. Find more attack surface by finding the…
Scan which performs an active scan against APIs defined by OpenAPI, or GraphQL (post ) via either a local file or a URL. The packaged scans are the simplest way to automate ZAP in docker, but also see the GitHub actions if you already use GitHub. In …
api-pentesting's People. Contributors. Recommend Projects. React. A declarative, efficient, and flexible JavaScript library for building user interfaces. A server is a program made to process requests and deliver data to clients. Machine learning.
pentest reporting. Get instant access to custom vulnerability scanners and automation features that simplify the pentesting process and produce valuable results. The platform helps you cover all the stages of an engagement, from information gathering to website scanning, network scanning, exploitation and reporting.
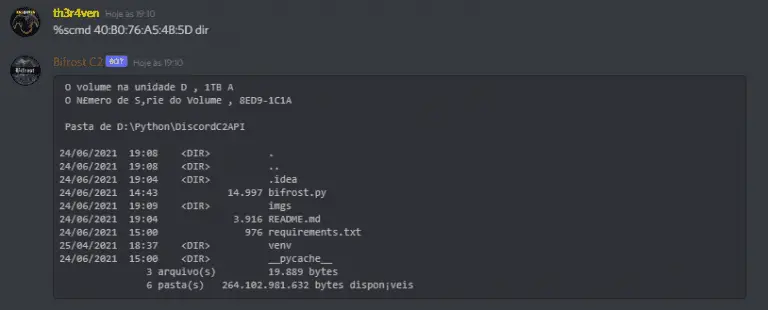
bifrost discord exploitation
In this article, I tried to prepare a write-up for the "CC: Pen Testing" room on tryhackme. The idea behind this room is to provide an introduction to various tools and concepts commonly encountered in penetration testing.

twint osint scraping advanced tool tools python
API (Application Programming Interface) usage increased tremendously in recent years. These days, APIs are less secure than ever and are continuously How to run an API Penetration Testing? You need to configure a project and configure the authentication. Then it just starts scanning and lasts
Integrate our pentesting and vulnerability scanning tools into your internal security testing flows. Enhance your Continuous Integration (CI) flows or add extra data to your custom Establish continuous security testing and automate it for maximum efficiency with the API.
Learn how solving UnCrackable Apps challenges from the OWASP MSTG can help you in pentesting Android applications. Home Dev Blog Pentesting Android Applications: Tools and Step-by-Step Instructions.

pentest
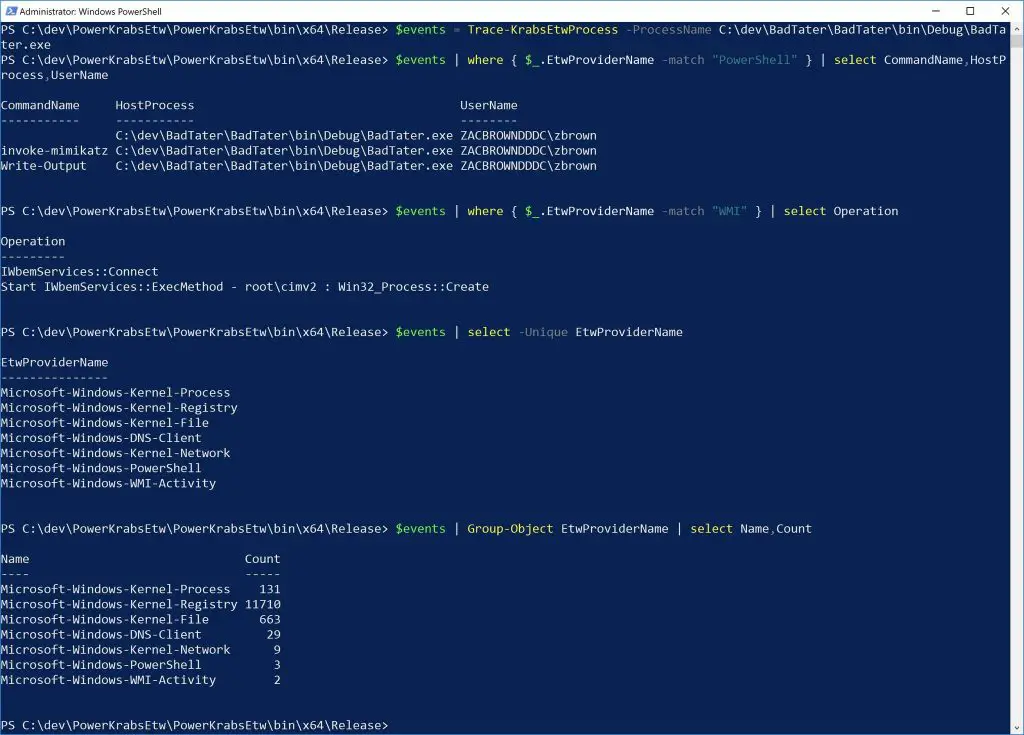
etw tracing powershell
Brief about API Penetration Testing: API Penetration Testing is one of the favourite attack surfaces, where the attacker can use to gain into further access to the application or server. During the blog
