Denial of service (DoS) and distributed denial of service (DDoS) attacks are an ever present threat to online businesses that can lead to downed websites, lost traffic and damaged client relationships. DDoS scripts, the software that enables the execution of DDoS attacks, greatly vary in severity,
Anti-DDoS provides Representational State Transfer (REST) APIs, allowing you to use HTTPS requests to call them. For details, see API Calling.
How to make the website: API SCRIPT DOWNLOAD ... In this tutorial we are going to learn how to write a basic DDOS script in Python! ◾◾◾◾◾◾◾◾◾◾◾◾◾◾◾◾◾ Programming ...

terraform env0

how to add a ddos api to a c# console app. how to use asynctask to make api connection. can we use post request instead of put for creating a resource. ApiResponse.
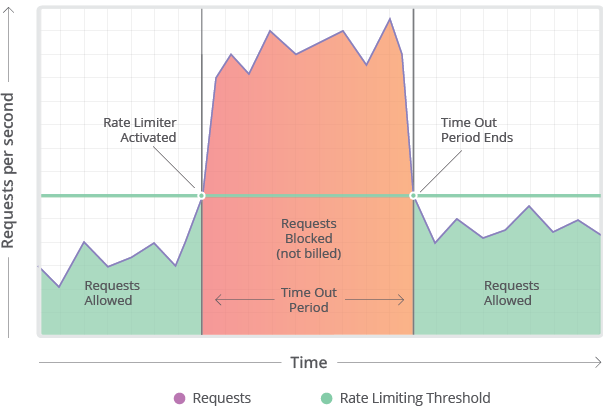
rate limiting cloudflare graph traffic network ip
Making Ddos Panel with an api for the public PART 1Подробнее. HOW TO MAKE A DDOS/ Подробнее. NEW PANEL DDOS + API BY MATSAKI 50 GBPS BYPASS MÉTHODEПодробнее. HOW TO MAKE A DDOS ATTACK HUBПодробнее.
DOSR DDOS API Denial Of Service Recovery Coded by Ben Jones Overview Usage. The API is designed to be used to receive data on a single socket specified in the configuration and if more sockets are needed, the user will need to instantiate additional instances of the API.
Learn how DDoS attacks are performed with DDoS Tool. Here is a list of the most popular DDoS attack tools with their complete details. To make a DoS attack on the server, this tool uses SOCKS proxies and SSL connections. Features: The attack can be made on HTTP, FTP, SMTP, IMAP, and Telnet.
How JavaScript DDoS Works. Most of the interactivity in modern websites comes from JavaScript. Sites include interactive elements by adding While the ability to make HTTP(S) requests from JavaScript can be used to make websites more fun to use, it can also be used to turn the browser into a weapon.
How to make Make a full booter ddos] - 16/10/2016 · is the number one paste tool since 2002. Pastebin is a website FAQ? How to prevent DDoS attacks? Using an access control framework, such as OAuth, you control the list of APIs that each specific API key can access.
A retarded command line injection vulnerable API source for ddosing. DDoS-API's People. Contributors. A server is a program made to process requests and deliver data to clients. Machine learning.

server security operating system robots cyber
› Get more: How to make booter panelDetail Install. MAKE AN API DDOS WITH A VPS - Install. Details: C# answers related to "how to add a ddos api to a c# console app" C# graph api upload file one drive; console application in c# ms crm; how crate cron netapp; C#
Видео FREE DDOS API [TCP] канала TRC. Показать.
Booter API Stresser API Anonymous DDoS Anonymous Booter Anonymous Stresser Cheap Stresser Cheap Booter ddossing How to DDoS Hot to Boot software network youtube gui booter high quality unseen clean ddos tool tutorial tool how to use to easy new free ip booter denial-of-service
C++ Program to print Geometric Progression (
API Protector .NET allows to combine different protections (by ip, by user, by role, in general, etc) decorating each function with a single line, which makes it easy to This approach will be more limited against a DDoS attack where the remote IP addresses will be over a wide range, and also
Learn how hackers launch DDoS attacks and how distributed denial of service works. We compile the best tips on how to DDoS so you can understand how This makes it a few orders of magnitude more powerful than its smaller sibling. Measuring the strength of a DDoS. According to this study,
Validate how Azure DDoS Protection helps protect your Azure resources from DDoS attacks. Optimize your incident response process while under DDoS attack. BreakingPoint Cloud API Script.
In this video from our API Security: Offence and Defence online course (now only available in a subscription plan) you can learn how does a DDoS attack work on API. What makes an API a great target for a DDoS attack? How to recognize a vulnerable API?
...Distributed danial of service - GitHub - ekovegeance/DDOS: script simple [DDOS] Distributed danial of DDOS. Version A bash script inspired by pentbox. Designed to be a simple way to Limiting the number of TCP connections per client; this will prevent a single machine from making

security end web performing check servers configuring properly cloud
Video for How To Make Ddos Api How to make an API booter - Visual Studio How To Create A Simple REST API in PHP

website penetration testing digital security company
DDOS stands for Distributed Denial of Service and it is an attack where we block the ressources of a server by flooding it with requests. could you do a tutorial on how to write a program to embed into a computer or any device and send files back to the host device?
This DoS (Denial of Service) Tutorial covers topics like Types of Dos Attacks, How DoS attacks work, DoS Attack Tools, Dos Protection, and more. Botnets- these are multitudes of compromised computers on the Internet that can be used to perform a distributed denial of service attack.
Disclaimer: I am not responsible for what you use this for, or responsible for ur server to be suspended if you are not in an offshore host! This script automatically installs the api on to your server. Attack Scripts: UDP, NTP, XSYN, SSDP,
› Get more: How to make ddos apiShow All. [Free+Source] Profound's C# API Stresser + How to setup an. Details: C# answers related to "how to add a ddos api to a c# console app" C# graph api upload file one drive; console application in c# ms crm; how crate cron netapp; C# get user
First of all DDos means distributed denail of service attack, and yes i don't know what the HELL it means either. but anyway DDosing is where you Now open LOIC (obvious but I want to get some of them little credit thingys so i'm trying to make it however many words long) and you will be

consequence gifs consequences gfycat
Distributed denial of service (DDoS) attack uses a large number of machines on different networks to disrupt a particular service provider; this attack is The goal of the attack is to flood random ports on a remote host. This causes the host to repeatedly check for the application listening at that port,
