![]()
virus matrix trojan binary skull viruses glowing malware hackers computer services firewall shutterstock
![]()
privacy security vector illustration clipart icons

bark identification tree identify elm guide virginia recognize barka often nysobukyfi

cyber security powerpoint template themed deck templates presentation computer theme network crime return slidemodel

hacker firewall data

virus sign round
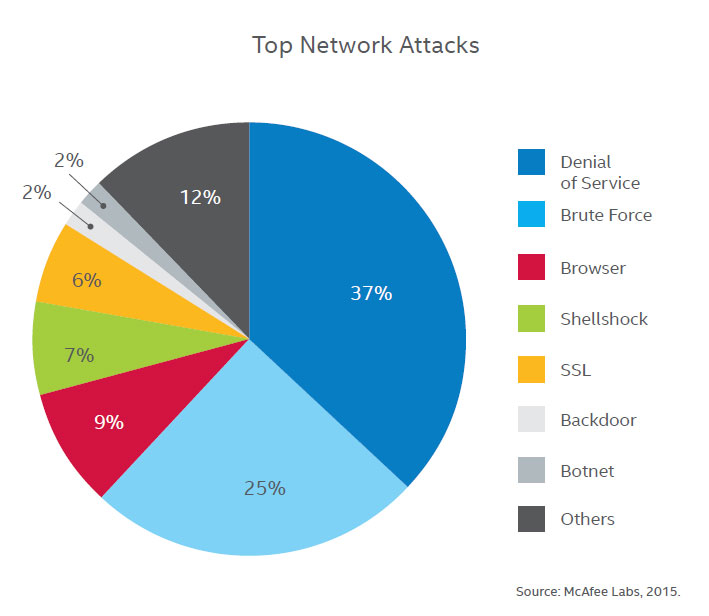
types network attack attacks common threats

hacker crime types anonymous cybercrimes cyber cybercrime prevention computer unit tips crimes attack graphic committing phishing spear employees protect vectors

ddos python ardt dns lookup
