We'll learn how to identify open ports using Nmap within Metasploit using the db_nmap command in the next section. In the real world, I exploited some systems by identifying open ports and try to attack this port. Both of these utility applications are available on many platforms, but Kali
Here is how to see what ports are open listening on a server. Having ports listenting to outside traffic also takes CPU effort, which consumes electricity and thus reduce battery life. Compare those against known vulnerabilities and exploits. Devices on the Internet with open ports are indexed
Details: Open ports allow black-hat hackers to exploit misconfigurations such as default insecure configurations, take advantage of vulnerabilities in services, and learn more about your network. Every unnecessary open port increases the threat landscape. Find out how black hat hackers select
Risks of open ports, port scanning and how to monitor. Learn more on attack surface reduction. Administrators should block such ports at the firewall level, which could be exploited in an already exploited situation where an attacker has compromised another system.
An explanation of how to exploit port 80 on the metasploitable 2 virtual machine. If you found another way to exploit this service Port scanning is a method of determining which ports on a network are open and could be receiving or sending data. It is also a ...
So the question is: how easy or difficult it is for someone to hack and gain access to the server instance of my web server with my setup? My main concern is: Can a person use the open ports 443 and 80 to gain access to my actual windows server instance?
Hello guys, Well, in a LAN cenário, lets say we do some reccon and we find a host with those normal ports opened like 135 -msrpc 139- netbios 445 - microsoft ds. Among others, Is there any new exploits and good articles about this matter?

log4j cve code deserialization execution remote apache impacts

bayz 6moons
You can find open ports by clicking here. How to use. Port Forwarding NetStat Grab wpa_supplicant Turn WiFi On/Off. Show Mac/Inet Remove Password Extract apk from app Use Keycode.

skynet writeup
Using nmap Open ports are ... Found insideA tester using Metasploit can exploit known vulnerabilities for which an exploit has been created or can create To scan Nmap ports on a remote system, enter the following in the terminal:. They can then attempt to exploit potential vulnerabilities in any
Port 80 is the default port for http services (web pages). In a previous scan we've determine that port 80 is open. It's now time to determine what is running Port 80 is a good source of information and exploit as any other port. We'll come back to this port for the web apps installed. In this article we
Today we will learn how to exploit this vulnerability using Metasploit, for this demonstration an intrusion test will be performed towards the Blue machine of the HackTheBox platform. Online, live, and in-house courses available. It is important that this port number be a port that can be opened on the
Pentesting-Exploitation. GitHub Gist: instantly share code, notes, and snippets. Pentesting-Exploitation Programs and Commands , Protocols Network / Ports. Table of Contents.
SMB Exploit via NTLM Capture. SMB DOS-Attack. Post Exploitation. We had use nmap UDP and TCP port scanning command for identifying open ports and protocol and from the given image you can observe that port 137 is open for NetBIOS network service in our local machine.
The use_exploit command exploits vulnerabilities of a system and helps the hacker to gain access to ... This is similar to the TCP connect() scan but it We'll learn how to identify open ports using Nmap within Metasploit using the db_nmap command in ... Found inside - Page 584Attack tools send
In Port scanning we scan for the open Ports which can be used to attack the victim computer. In Port scanning a series of messages sent to break into a computer to learn about the This is done either for the purpose of attacking them or for network security assessment how secured the network Is ??
Metasploit is a security framework that comes with many tools for system exploit and testing. As you saw during the scan process, a DOS slowloris vulnerability was found, in order to find how to exploit it As you can see ports 22,25,23 and 21 were found open. Carrying out a SYN scan with Metasploit
Proper enumeration and reconnaissance is needed to figure out the version and the service name running on any given port, even then you have to enumerate further to figure out whether the service
Exploiting HTTP PUT for shell. Now that we know we can upload files to this directory let's have a Otherwise script will fail in uploading the file and only display an open port and unknown service. In this tutorial we have learned how to assess a webserver for uploading files using the HTTP

#1 How many ports are open on the target machine? ANSWER: 1. All other ports are closed. In this case, we can call the "backdoor" port only for the open port. [Task 10] Exploiting FTP. #1 What is the password for the user "mike"? We should run this command
Preparing the Metapsloit Framework for Port Scanning using nmap and db_nmap, while also taking a look at SMB Version and Idle Scanning. Preparing Metasploit for Port Scanning. Scanners and most other auxiliary modules use the 'RHOSTS' option instead of 'RHOST'.
How To Open Ports in Kali Linux. Checking for open ports is among the first steps to secure your device. Here, we have assumed that you have Metasploit- this is an open source tool for developing, testing and using exploit code. How to input or read a Character, Word and a Sentence from user
Purpose: Exploitation of port 445 (SMB) using Metasploit. Description: Step by step informational process exploiting a vulnerable Linux system via port Port 445 is a TCP port for Microsoft-DS SMB file sharing. Many (to most) Windows systems, as well as Linux, have this port open by default,

computer netinfo collect network using following should screen
This should clear your concepts on how to open a port in . Enter the Shell Port number. Getting ready The Apache web server must be started in order to complete this recipe. Click Run to launch the exploit. Compare the times required for all. Use below command to open port only for Single IP.
You are here: Blog » how to exploit open ports using metasploit. Now, we know that port 135 is open so, we search for a related RPC exploit in Metasploit. Found inside - Page 293One "solution" is to attack a smartphone via the PC's USB port. For example, a cybercriminal could begin an attack
In this video, Alexis @HackerSploit and I share thoughts on how to attack common ports like 22, 23, 80, 8080 for penetration testing. Full
generator paypal hack proof run
To find the open ports and services, the command is Once you find the open ports and service like the samba port and service ready, get set for sending an exploit through that port to create a meterpreter session. Hi Sir, How can we do it without metasploit, like by running a exploit manually.
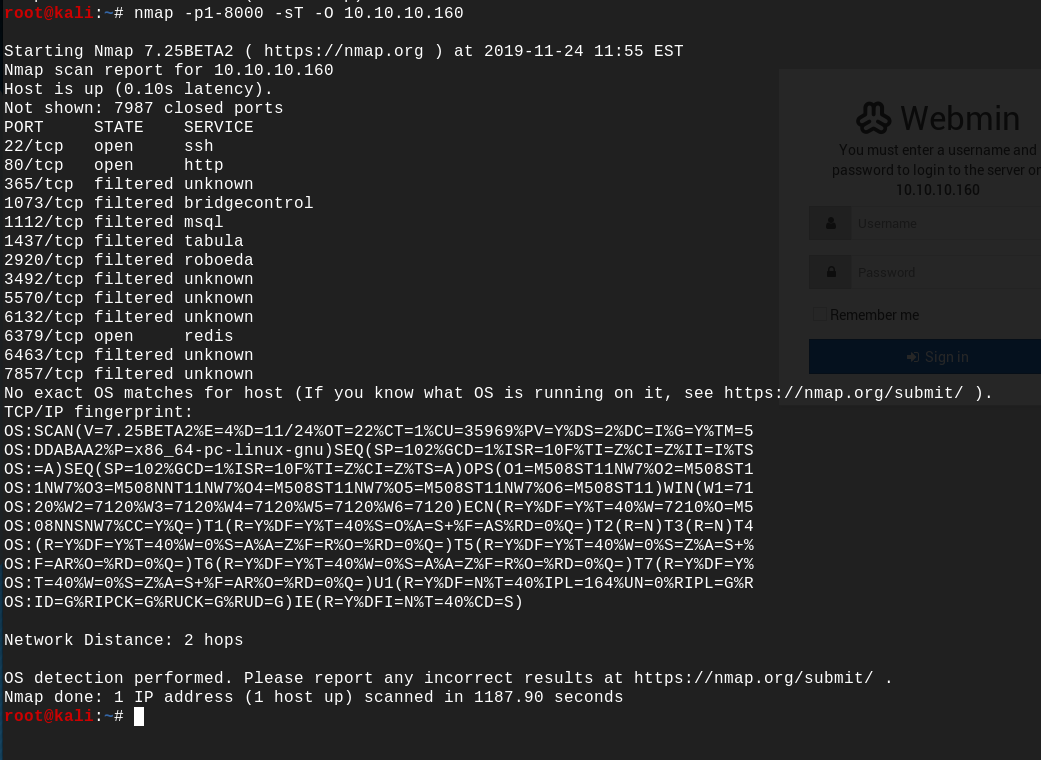
ctf hackthebox postman redis open installed interesting port


smb windows exploit metasploit xp msf module ms08 netapi options
Understanding port configuration and how to discover what the attack vectors are on your server is only one step to securing your information and your VPS. Execute it like this: A TCP "SYN" scan exploits the way that TCP establishes a connection. Get the latest tutorials on SysAdmin and
Can i exploit this port? It's open, but its not common or anything, how would I go about exploiting an open port that doesnt really have a well known Is there a guide on how to enumerate freebsd for privilege escalation manually because many of the commands in freebsd are different from Linux.
First, a reminder of the information nmap returned about the SSH service after a port scan: 22/tcp open ssh OpenSSH Debian 8ubuntu1 (protocol )...
