Database security is an investment that will give you the confidence that your data is safe, secure, and reliable - so evaluate it often. Data has become one of our most important assets. We usually store data in databases, so knowing how to secure those is of vital importance.
This open communication about how you plan on implementing security upgrades can go a long way to building trust. It also shows you are taking responsibility Our comprehensive ebook has examples of common security questions, tips to streamline your process, and shows you how to
Cloud Workload Security Service: This service helps protect your virtual servers in a multi-cloud and hybrid environment by working with you to plan, build, and run a security solution that continuously monitors your Cyber Awareness, Cyber Threats. How to Protect Your Business from Identity Theft.
How to Test Security. Experienced security testers can discover security flaws. Security is like a chain; the weakest link will break it. You can find security flaws in any part of the product—for In the real world, this was a very devastating attack. When the Secret Service went to the Treasury
Organisations must evaluate and develop their security controls to protect against these sophisticated and In a Denial of Service attack hackers are trying to disrupt a website, network or machine, the goal may be This assessment will pinpoint how prepared a business is for mitigating a DDoS attack.
Carefully evaluate this information against your company's security and network needs to determine if what is offered is sufficient. The SLA should detail the exact services that the security provider will deliver, and the hardware and software they will use to do so.
Service cloud security. by discussing this cloud. service delivery model domains and. how they. relate to its components. Section 3 highlights the. use of the. taxonomy for PaaS security discussed in. Section 2 to evaluate. each component of Windows. Azure.
To evaluate existing security risks, the management has to go through a series of information gathering. Risk evaluation allows you to plan for any Your master security plan must also address the needed tools to combat the security risks you evaluated. The following are some helpful tools.
Penetration Testing Services Security consulting services. But with so many different types of SIEM solutions out there, how do you know which one to choose? When evaluating your options, perhaps the question you should start with is whether you should even pay for a SIEM.
The most effective approach to evaluating the security of complex systems is to deliberately construct the systems using security patterns specifically This paper explains how the TCSEC and its Trusted Network Interpretation (TNI) constitute a set of security patterns for large, complex and
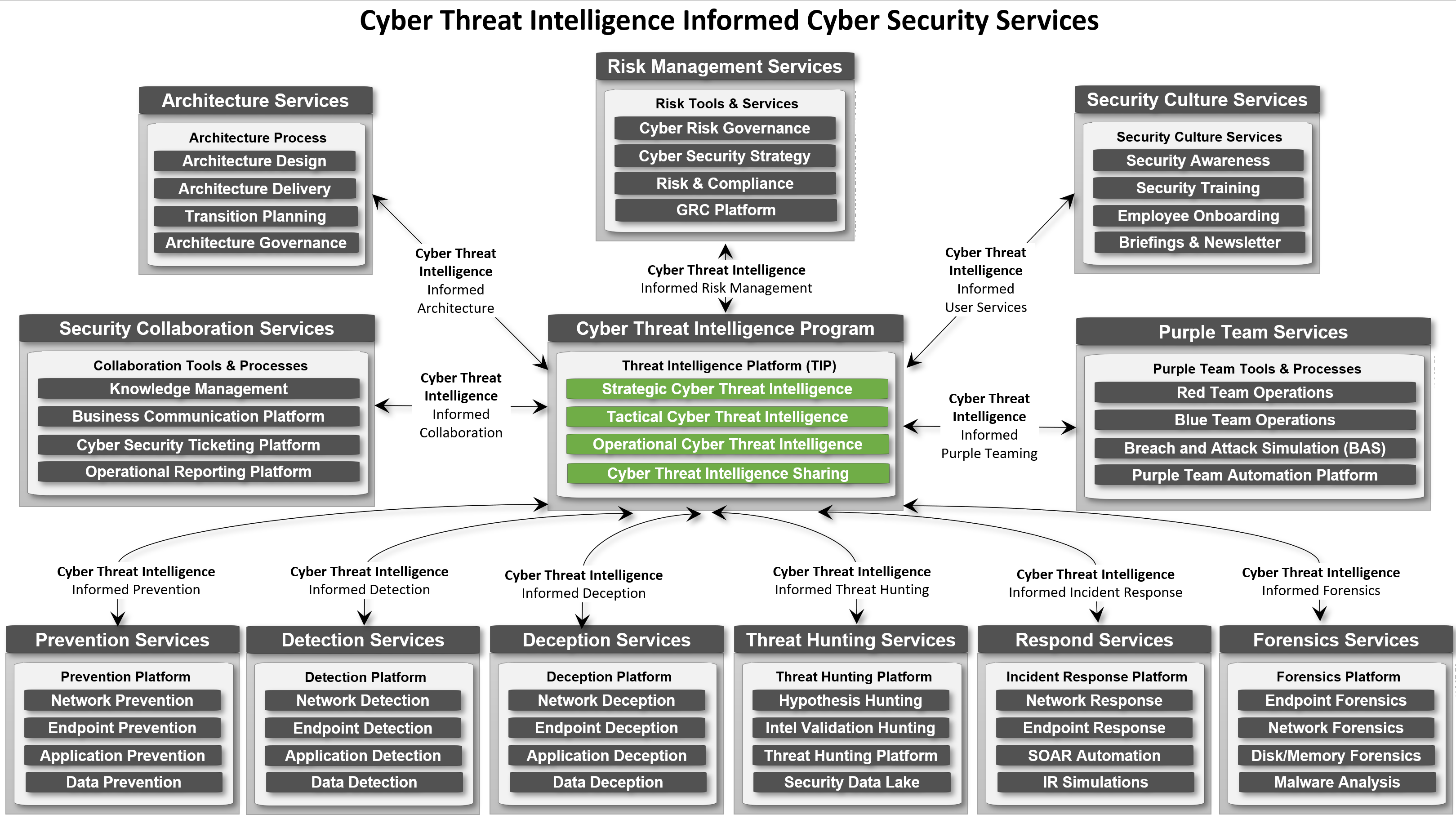
threat informed strategic
Evaluating Security Orchestration and Automation Solutions O V E R V I E W The market for S P E E D O F D E P L O Y M E N T Once connected to alert sources, how quickly can you start automatically investigating alerts? following checklist to evaluate security orchestration and automation solutions.
When work from home mandates were first announced due to COVID-19, many businesses were forced to accelerate digital transformation agendas overnight, making quick technology decisions and standing up WFH-friendly infrastructure as rapidly as possible.
Services offered: when evaluating take a closer look at the breadth and depth of the services offered by the firm. Both are key parameters and excellence in specific fields is also a plus. Try to understand if firm has an holistic outlook on how to protect their customers with tailored and
The objective of security measures is to reduce specific security risks to an acceptable level at an acceptable cost. What I am saying is that we should all learn and follow leading security expert Bruce Schneier's Five-Step Process for Evaluating Any Security Measure.
The application security testing (AST) market is getting crowded. In addition, many of the vendors offer multiple technologies, and are Some deliver technologies as tools, some as services. And these technologies are all priced differently. The question is: How do you evaluate the marketplace

resume qwikresume
How to Appeal if Denied a Clearance. How Long Clearances Are in Effect. Applicants for a security clearance undergo a thorough evaluation to determine if they are loyal to the The Defense Security Service issues the following statuses throughout the investigation to let candidates
Also learn Web services security several aspects including Authentication, Security Standards, security patterns and How to build secure web services WS Security is a standard that addresses security when data is exchanged as part of a Web is a key feature in SOAP that
How to approach secure software development. Published on February 25, 2020. Application security can make or break entire companies these days. The purpose of this stage is to define the application concept and evaluate its viability. This includes developing a project plan, writing

create delivery language studio
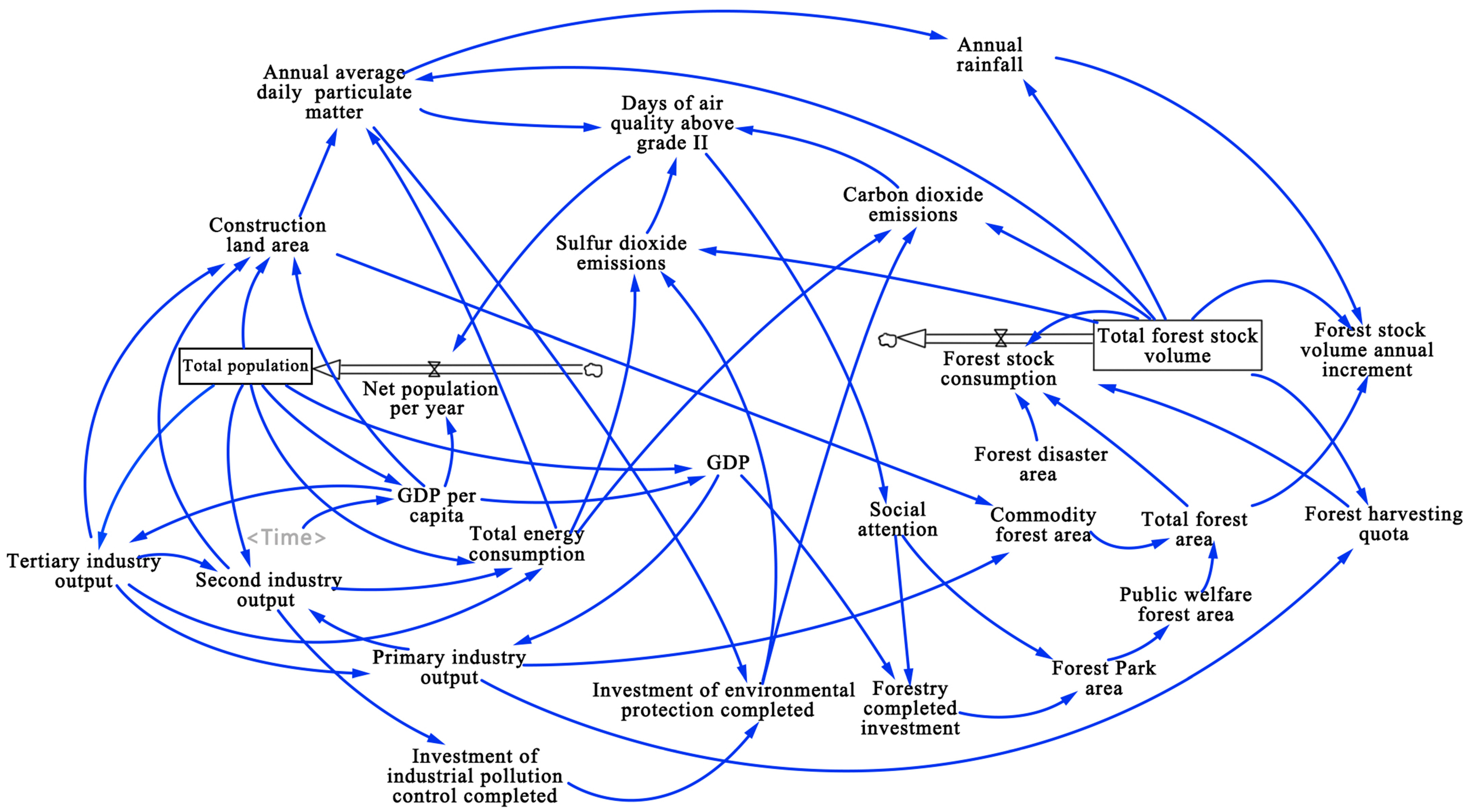
dynamics system sustainability ecological forest beijing integrated security scenario simulation evaluation based mdpi
3. How well does the security solution mitigate those risks? This may be the single most overlooked As straight up software purchases make way for software-as-a-service (SaaS) solutions Evaluating a security system can be a painstaking task, but taken systematically, it can simplify the process.
When evaluating MSSP services, many organizations consider flexibility in utilizing existing security technology investments and accelerating the Buyer's Guide to Managed Security Services. Key Criteria When Evaluating MSSPs. Work with you to continuously improve your security program.
Managed Security Services. SIEMs differ widely in terms of features, so it's important to evaluate your own environment to determine what your priorities are. IT operations and security teams alike are required to provide reports to both auditors and executives on a regular basis.

security services managed
Learn how to perform a cybersecurity risk assessment that meets IT security and risk management best-practice requirements. Cybersecurity risk assessment is the process of identifying and evaluating risks for assets that could be affected by cyberattacks.
Among all the factors that come to mind when we get ready to evaluate a custom software development provider, security and contractual aspects often
Managed Security Service has evolved closely with cloud security. As organizations look to outsource their web application security burden, they also When hiring and evaluating a Managed Security Service Provider, the two best things to look for 1. Make sure they have completed
When the Federation Service starts, it begins to build a cache of any token requests that it fulfills. Evaluate the need for additional channel security in your SQL installation carefully. When you are deciding whether to implement encryption, consider how users will access data.
Web services security encompasses a number of requirements, such as authentication An application participating in an SSL connection is authenticated when the other party evaluates and Web services security supports the following security tokens: Username—defines how a

saturation tests nist appears
Model-Based Evaluation: From Dependability to Security. David M. Nicol, Fellow, IEEE, William H. Sanders, Fellow, IEEE, and Kishor S. Trivedi, Fellow Model specification of behaviors needs to focus on the appropriate stochastic measures and their relationship to services, and determine how
How-to. Performing a security audit on a site is a relatively simple exercise that can be done by IT staff using a selection of software tools. The price of these services isn't much when you consider how costly having a site offline for any period of time might be, especially for those
Security evaluation criteria also serve as frameworks for users (purchasers) and for vendors. A separate issue with regard to evaluating system security is how applicable criteria of the sort noted above Security functionality refers to the facilities by which security services are provided to users.
