analysis is a broad class of techniques that often employs message lengths to infer sensitive implementation about traffic flows by aggregating information about a large number of messages. Padding a message's payload before encrypting it can help obscure the cleartext's true length, at the cost of increasing the ciphertext's size and ...
Encrypts only network traffic; it is not used for authentication. Has a compatibility mode that lets you use old and new components in the same environment (with and without SSL). Using SSL significantly reduces traffic bandwidth and performance. Not all probes support SSL. SSL settings are specific
Network-based encryption and application-layer encryption are not mutually exclusive either. They can, and often are, used together to apply two layers of encryption to data traffic. Talking specifically about the network, Wood recommends enabling two types of protection: IPsec and MACsec.
However, network traffic in server-to-server communications and inside data centers is often not encrypted. If an attacker gains access to such a To prevent attackers from snooping on data with unauthorized access, organizations are increasingly monitoring their own network traffic to
For debugging encrypted network traffic for iOS, I cover Proxyman and Charles Proxy, and for Android, HTTP Toolkit and Proxyman (I skip Charles Proxy I only cover how to debug the traffic of your connected iOS tool with Proxyman, for example, and not with Charles Proxy (though it's possible).
The Consul agent supports encrypting all of its network traffic. The exact method of encryption is described on the encryption internals page. There are two separate encryption systems, one for gossip traffic and one for RPC.

iscsi protocol scsi solidfire
14, 2018 · The word of caution here is that you should only connect to the network you trust – home network, office network etc. Encrypt! Encrypt! Encrypt! : Encrypt all the traffic that leaves your system. This will ensure that even if the traffic is being sniffed, the attacker will not be able to make sense of it.
How To Install Linux, Apache, MySQL, PHP (LAMP) stack on Ubuntu. At some point, you may find yourself on a network that is insecure or has an overly restrictive firewall and you'll A SOCKS proxy is an SSH encrypted tunnel in which configured applications forward their traffic down, and then,
Network encryption refers to encrypting data as it travels across the network between the client and server. The reason you should encrypt data at the You can configure network encryption by using either Oracle Net Manager or by editing the file. This guide explains how to use Oracle
13, 2018 · Routing all traffic through an OpenVPN client on a CentOS 7 NAT; Guide: Using Let's Encrypt SSL Certificates for local or network server; Programming Philosophy. Is programming an art form? The importance of getting terminology correct; SoCcam's Razor: Applying the Single Responsibility Principle using a practical approach; Other
Smart DNS will not encrypt your traffic. If you use Tor, it will protect your privacy, but many websites will block your access. So if you want a service that protects your privacy, gives you new IP addresses, and encrypts your data at the same time, opt for a reliable VPN provider.
For a corporate network, is there a way to possibly encrypt all network traffic on the local network? For #2 - Your physical and network security policy should limit access to the network devices to prevent an attacker from gaining access.
Encrypt your Internet traffic. Sometimes you want to encrypt your outgoing and incoming Internet traffic. If you're on an unsecured Wi-Fi network (at an airport, for instance), a hacker can intercept the data traveling to and from your laptop, which might contain sensitive information.
Why Should You Encrypt Your Internet Traffic? Encryption is all about keeping your online activities and its accompanying personal and business-related information safe from the eyes of third parties, who would just love to be able to observe your online antics, as well as steal your login,
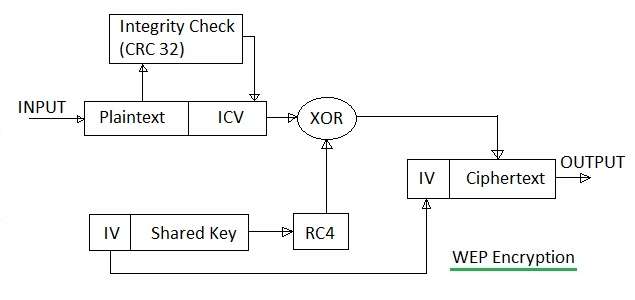
wep encryption wpa diagram wpa2 vs process block wireless network enterprise difference figure attacking decryption between pentest rfwireless

hardware firewalls barracuda firewall software network spam vs security networks machine solutions getvoip protect protecting voip
Learn how to use built-in Encryption with Overlay networks. Learn Step 1 - Initialise Swarm Mode, Step 2 - Create Unencrypted Overlay Network, Step 3 - Monitor Traffic, Step 4 - Create Encrypted Overlay Network, via free hands on training.
Video for How To Encrypt Network Traffic How To Threat Hunt in Encrypted Network Traffic- How to solve encrypted network traffic issue eset
How Encryption of Network Traffic Works. Sender and receiver are each calculating a secret number which will be used to encrypt the How to Encrypt Your Wireless Network. Locate security settings in your router's administrator console. Change encryption to WPA2-PSK or WPA3-SAE.
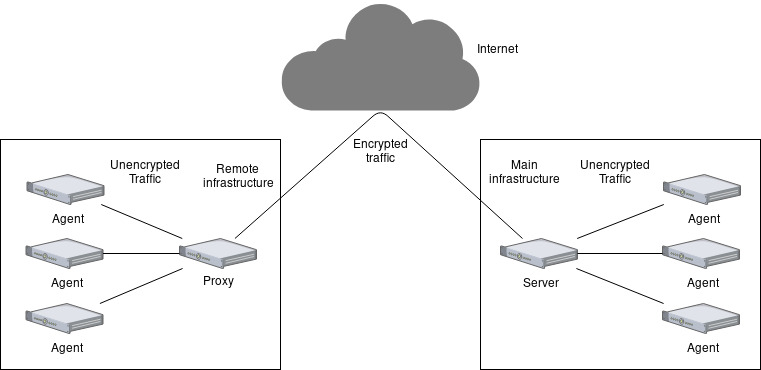
zabbix proxy encryption infrastructure remote brendan server agent psk supervision based encrypt let
Encrypting Network Traffic. Mark Lomas Computer Security Group University of Cambridge. Alternativelythey may not be aware how insecure their computers are; for example most of the computers in use within the Computer Laboratory here in Cambridge transmit user's
A lot of it is encrypted. Here's how I decrypt SSL with Wireshark. Wireshark is a network traffic analyzer; it's a core utility that many administrators use to troubleshoot problems on their networks.
This Instructable covers how to encrypt all outgoing network traffic on your home network, and is geared towards people in the United States. Encryption is an important step towards keeping your browsing and other internet activity out of the hands of corporations and governments.
Encryption: IPsec encrypts the payloads within each packet and each packet's IP header (unless transport mode is used instead A network port is the virtual location where data goes in a computer. Ports are how computers keep track of different processes and connections; if data goes to a
Encrypting Data at Datastore Layer. Encrypting traffic between nodes with IPsec. Any number of additional subnets to encrypt may be added to this file, which results in all traffic to those All nodes within the cluster need to allow IPsec related network traffic. This includes IP protocol numbers
For my first article, I wanted to dive into how to use your Raspberry PI to encrypt your network traffic while traveling or using public WiFi. When traveling you probably find your self using a lot of public wifi spots, one problem when using these hotspots is that anyone can snoop (rather easily) on
How to encrypt local network traffic? In Windows, you can configure the built-in Firewall via Group Policy to only allow encrypted traffic outwards. A Virtual Private Network (VPN) is arguably the best way to encrypt your internet traffic - all of your internet traffic. A VPN encases your
Flowmon Encrypted Traffic Analysis collects network traffic metadata in IPFIX format using passive probes and enriches it with TLS protocol information (among others). These attributes of the encrypted session between clients and servers are available regardless of the client's physical location
How to get end to end encryption Possible threats Encryption is the encoding of a message so that only the intended addressee can decode it.

superfast
A VPN encrypts and anonymizes your data traffic online. But how secure is a VPN connection and how do you set it up?
IPsec can protect our traffic with the following features: Confidentiality: by encrypting our data, nobody except the sender and receiver will be able to read our data. Integrity: we want to make sure that nobody changes the data in our packets.
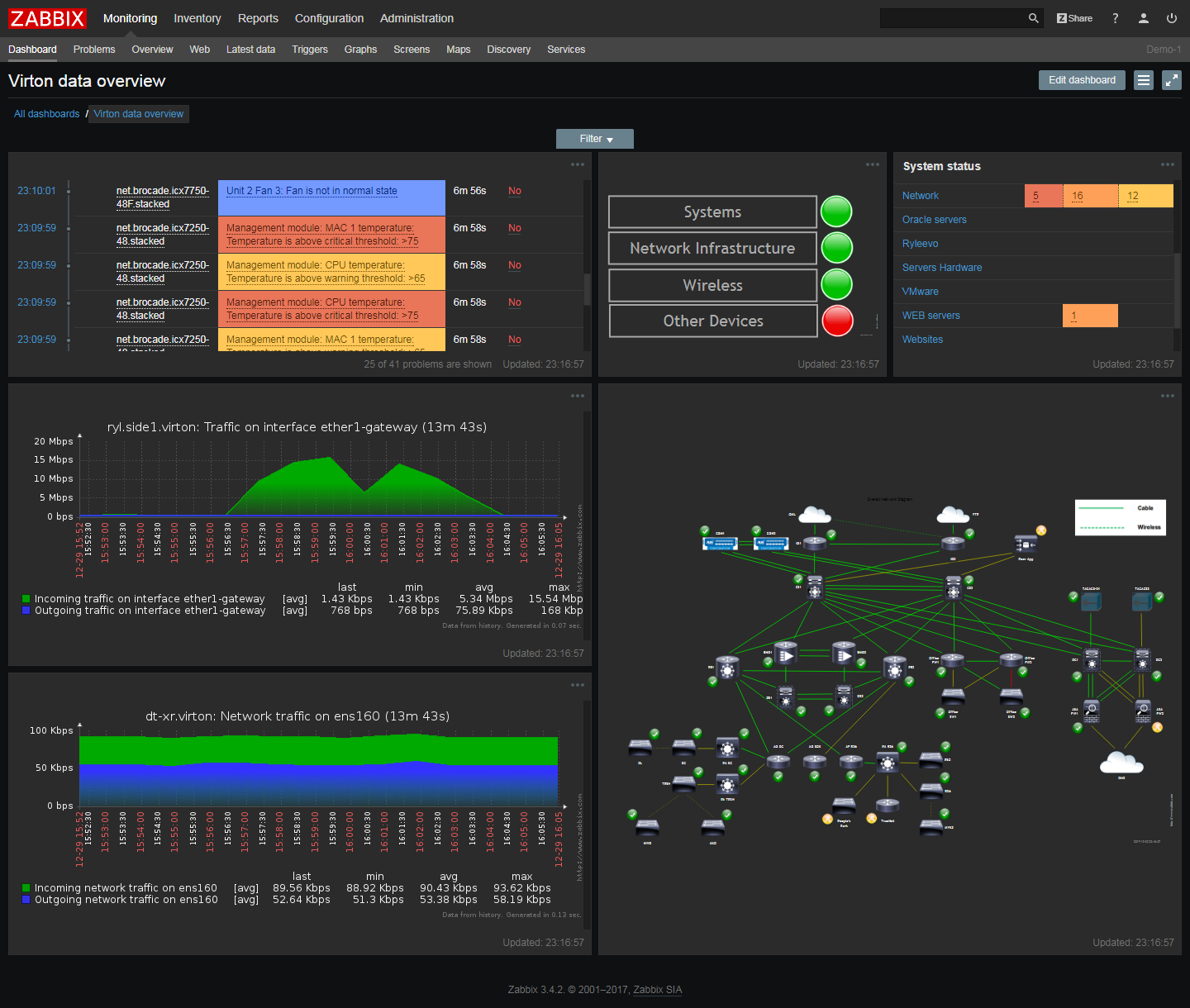
zabbix monitoring dashboard server network source tools open monitor software management nagios performance windows dark script availability screenshot screenshots
...create a secure, encrypted networking topology in Azure but I can't find a lot of information on how Microsoft encrypts the traffic that is going between Azure VNETs do not encrypt traffic between 2 VMs in the same VNET. VNET Traffic is isolated, and functions in the same way as an

security network encryption
Sender encryption provides tools for users to encrypt their emails, such as flagging as "urgent" or installing a plug-in with a clickable encryption button. In sender encryption, however, businesses are relying on the judgement of employees to decide what should be encrypted.
01, 2017 · So someone eavesdropping on your network traffic, say from a car parked nearby, will only see encrypted data. (Some routers may offer the WPA2-Enterprise option as well - that is meant for an enterprise network with many computers and most people would want the help of an IT pro to set that up.). The steps below explain this in more detail.
While VPN does encrypt the network traffic it does so only until it exits from the VPN endpoint, post the network traffic is unprotected. Encrypting your DNS network is no more a stringent security measure. Due to rise in the number of spoofing and man-in-the-middle attacks, it is very important
To encrypt traffic between networks (or a network and a host) you have to use tunnel mode. This example explains how it is possible to establish a secure and encrypted GRE tunnel between two RouterOS devices when one or both sites do not have a static IP address.
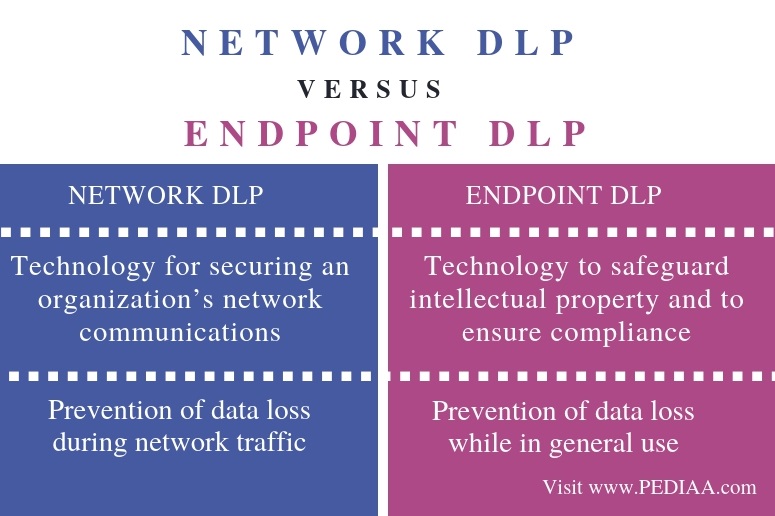
dlp endpoint pediaa
Learn how this powerful open-source tool helps you manage components across containers in any First of all, MACsec and IPsec operate on different network layers. IPsec works on IP packets, at layer 3 MACsec also cannot protect against malicious layer 3 traffic coming from a different
Do I Encrypt My Internet Connection? - 5 Tools To Use There are many ways to encrypt your internet connection. You can use encrypted browsing apps and get your WiFi encrypted with the help of special apps that also encrypt network traffic. In short, there's no single best method on how to encrypt your internet traffic. 1.
How to Optimize Your VoIP Network. How to Set Up a Home Office. How to Start an Online Business. By encrypting your traffic and routing it through a VPN server, it is harder but not impossible for observers to identify you and track your movements online.
