How people use Fing's IoT Technology to discover IoT connected devices. Since Fing was first launched in 2009 the world's adoption of the Internet of Things has been To date there are over 35 million people that have used our network scanner to discover the connected devices on a network.
Ultimate Goal is to get these IOT devices only talking to HA and not the internet. All traffic going through HA for home automation except for the Nest and Echo products. After going through the endless information on how to do this including double NAT, firewall, coding and scripts that are
How-To Videos. IoT devices are generally created to be very small and, when possible, provide wireless connectivity as well. That means that we now have devices within our networks that have previously been standalone or network inert brought in and connected with no means of
I need to discover IOT devices ( like Philips HUE or custom particle photon) using a non-Echo Alexa Also tried the audio "Discover devices" command. But in both case I was not able to discover the How can a custom Alexa enabled device can perform IOT device discovery and registration?
24, 2015 · If you don't have a display connected to your device, Microsoft as a cool tool for you to find your device on the network. When you download the Windows 10 IoT Core Image you also have a installer file called ''. This installer installs you a tool called Windows 10 IoT Core Watcher, which will discover your Windows 10 IoT Core …Reviews: 1Estimated Reading Time: 1 min
IoT (Internet of Things). Discovering IoT Devices on the network. I'd like to discover as much information about IoT devices on a network as possible. I've seen code to enumerate the devices, find the IP Addresses and MAC Addresses, but what else can I find?
09, 2020 · Use your router’s online interface. This is a relatively simple (and free) way to get an idea of who’s using your network. Log into your router to …
02, 2015 · I'd like to discover as much information about IoT devices on a network as possible. I've seen code to enumerate the devices, find the IP Addresses and MAC Addresses, but what else can I find? In particular, I'd like to know that something is a lamp, and more importantly, what the manufacturer : 3
Widespread adoption of Internet of Things (IoT) devices increased the variety of devices connected to a network. How- ever, with the increasing popularity of cryptographic protocols, the traditional means of inspecting packet contents to enforce security policies is no longer a viable approach

How do you discover all IoT devices operational in your domain? If the company instead allows arbitrary devices uncontrolled in the network and even gives them a public IP address it IoT devices, in particular, leverage either on-device REST APIs or reach out to cloud-based REST APIs.
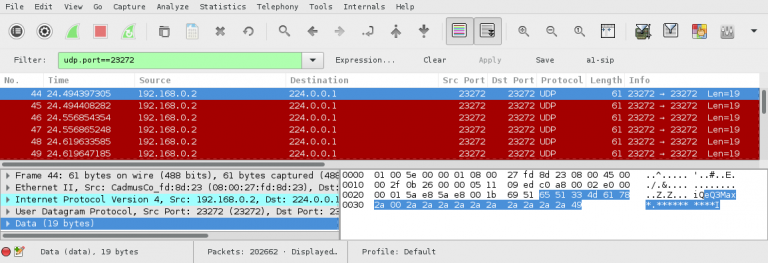
analyzing iot insinuator sent
devices tend to provide functionality by relying on a backend infrastructure in the form of a set of remote servers. We found that by studying the destinations of IoT communication, we can infer the type of device hosted at a subscriber line — even if they are behind a Network Address Translation (NAT). This left us the pr…Generating Detection RulesApplying The Detection Rules on Datasets from An ISPOnce we generatedthe IoT traffic, the next step was to identify which features (IP addresses,ports, domains, and protocols) can be used to identify these devices. Rememberthat at the provider level, we use flow captures such as NetFlow, and thesecaptures contain only packet headers. W…See more on Reading Time: 6 mins

The Internet of Things, or IoT, refers to the billions of physical devices around the world that are now connected to the internet, all collecting Badly installed IoT products could easily open up corporate networks to attack by hackers, or simply leak data. It might seem like a trivial threat but imagine if
oauth iot devices login via google hackster things
The internet of things has such a wide range of use cases and individual devices that network architects have to pay attention to a wide combination of variables for communication, power, bandwidth, reliability, cost and more.
IoT devices tend to provide functionality by relying on a backend infrastructure in the form of a set of remote servers. We found that by studying the destinations of IoT communication, we can infer the type of device hosted at a subscriber line — even if they are behind a Network Address Translation (NAT).

android google play modules apex venturebeat users class app span li user format update
30, 2022 · A virtual personal network is an excellent way to save in-home IoT devices against cyber-attacks. You broadcast your IP address across the internet for all when you join the internet from a home network. If a hostile actor discovers your IP address, he may it to identify unsecured IoT devices with the same address and attack or manipulate them.
IoT Device Discovery. IoT Security uses machine learning to analyze network traffic data and identify IoT How complicated is the behavior of an individual device? For example, IoT Security learns the The devices that IoT Security discovers on the network and identifies appear on the
The IoT Dashboard makes it easy to set up a new device. For detailed instructions on how to get started, see the Get Started page. The default device name is minwinpc. We recommend changing it to something unique as this makes it easier to find the device on the network.

cases iot internet things
The Internet of Things, or IoT, is essentially an ecosystem of physical devices, vehicles, appliances, and other things that have the ability to connect, collect and exchange data over a wired and wireless network, with little or no human-to-human or human-to-computer intervention.
Discover the IoT devices on the victim's local network. Take control of them using web-based attacks. Duration of the attack. How to prevent DNS rebinding attacks on IoT devices. According to the researchers, the user, browser vendors, IoT manufacturers, and DNS providers each have to
IoT Inspector: Crowdsourcing Labeled Network Traffic from Smart Home Devices at Scale Danny Yuxing. Huang, Noah Apthorpe, Gunes Acar, Frank Li Discovering IoT Smart Home Privacy Norms using Contextual Integrity. Noah Apthorpe, Yan Shvartzshnaider, Arunesh Mathur, Dillon
Managing Internet of Things (IoT) devices should be easy. Yet, the increasing use of encrypted network traffic in IoT devices is complicating their management, for example during device audits or security scans. While desirable from a network security point of view, the use of encrypted
This is how you will learn to create this IoT luminaire with Tuya Smart. See the luminaire in the figure Select the Light Source option, check the confirm option, and click next. Select your WIFI network and enter The answer to all these questions is: integrate your devices with Tuya IoT Smart technology.
As Internet of Things (IoT) gains steam, more devices are connecting to the network than ever before. How does an IT department deal with the burden? Companies that connect products to the network - Internet of Things (IoT) devices like digital signage, audio visual equipment,
Learn how to check and identify devices connected to your home network you do not recognize and prevent unauthorized access. Take note of your device MAC Addresses. Identify if the device belongs to your household through your devices' unique number called MAC address

device iot securely intel software accessing internet things
an unknown device joins the network, one or more Palo Alto Networks firewalls log its network traffic and then send the logs to the logging service. These logs include session logs, containing metadata about traffic flow, and enhanced application logs, containing data from packet payloads. IoT Security accesses the data from the logging service and uses its advanced …
06, 2019 · By keeping all the IoT equipment on a separate network, any compromise of a "smart" device will not grant an attacker a direct route to a user's primary devices -- where most of their data is Reading Time: 3 mins
Internet of things (IoT) emerged as a concept about 20 years ago and is now making headlines around the world. Everyone talks about connectivity, smart To improve your IoT devices' protection, you should consider getting one of the top antivirus solutions. Most can protect your entire home
12, 2020 · IoT and OT encompasses a large category of smart devices and are not usually known to, or managed by, the business because they don't go through IT …

synopsys recognition facial vision system fitsnews pay engineering processor brother courtesy licenses drivers sc working dark state invoices ap cards
02, 2019 · How to Find All IP Addresses on a Network. Open the command prompt. Enter the command “ipconfig” for Mac or “ifconfig” on Linux. Your computer will then display its own IP address, subnet mask, gateway address, and ... Next, input the command “arp -a”. ARP stands for “Address Resolution Protocol,” ...Estimated Reading Time: 8 mins

hololens debugging deploying remotely
I'd like to discover as much information about IoT devices on a network as possible. I've seen code to enumerate the devices, find the IP Addresses and MAC Addresses, but From what I understand, these things are more concerned with the services exposed rather than exactly what the device is.
Managing Internet of Things (IoT) devices should be easy. Yet, the increasing use of encrypted network traffic in IoT devices is complicating their @article{Valdez2019HowTD, title={How to Discover IoT Devices When Network Traffic Is Encrypted}, author={Enriquillo Valdez and Dimitrios
The term "Internet of Things" was coined by entrepreneur Kevin Ashton, one of the founders of the Auto-ID Center at MIT. Ashton was part of a team that discovered how to link objects IoT connected devices communicate via networks or cloud-based platforms connected to the Internet of Things.
The Internet of Things (IoT) is defined as a paradigm in which objects equipped with sensors, actuators, and processors communicate with each other to serve a meaningful purpose. In this paper, we survey state-of-the-art methods, protocols, and applications in this new emerging area.
The Internet of Things, or IoT, impacts everything from the way we travel and do our shopping to the way The IoT is a giant network of connected things and people - all of which collect and share data about How does it work? Devices and objects with built in sensors are connected to an Internet
This video shows a early stage demo of my IOT Dash app (WPF) on Windows. The app discovers all devices via UDP on the local network, gets the
Internet of Things (IoT) devices communicate is dozens of different ways, using hundreds of different protocols. In this article we cover the common elements in an IoT device - anything from the tiniest temperature sensor to a giant industrial robot. Local communications - the method the device uses

Improperly secured Internet of Things (IoT) devices have been commandeered by bot herders and other malicious attackers. Organisations need a way to identify and track these IoT devices, which are often brought in unofficially by users. But network administrators face a number of challenges
The Internet of things (IoT) describes the network of physical objects—"things" or objects—that are embedded with sensors,
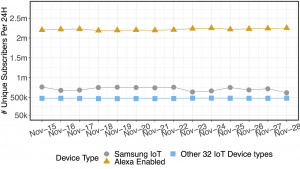
iot apnic

zang
09, 2016 · How people use Fing's IoT Technology to discover IoT connected devices. Since Fing was first launched in 2009 the world's adoption of the Internet of Things has been skyrocketing. To date there are over 35 million people that have used our network scanner to discover the connected devices on a network.

