
protection smart platform beat bad network threat innovating guys interconnected layered
Before we can learn how to detect cyber threats, it's important to first identify what the most common threats are. According to the National Institute of Standards and Technology, five of the most common cyber threats are: Identity theft. Some of the most common cyber attacks involve hackers

command center security ibm cyber mobile range discover response
Top Cyber Threat Facts, Figures, and Statistics. Cyber threats continue to evolve, causing trillions worth of losses to the cyber world. Employees are the first line of defense against cyberthreats for every organization. Thus, organizations must conduct comprehensive cybersecurity

brand identity monitoring value scraping web build down detect protection take branding monitor prices companies company difference visual between sector
How to prioritize threats: the OWASP threat model. Using threat intelligence for threat prevention. What are cybersecurity threats? Cybersecurity threats reflect the risk of experiencing a cyber attack. A cyber attack is an intentional and malicious effort by an organization or an individual to breach
11, 2022 · What will be 2022’s biggest cyber threats to consumers? ... just getting an extra pair of eyes on a concern can help to detect a scam or provide reassurance,” Brown said,
Cyber threat hunters dig deep into a network to find malicious actors in an environment that have slipped past initial endpoint security defenses. Threat hunting is the practice of proactively searching for cyber threats that are lurking undetected in a network. Cyber threat hunting digs deep to
There are several factors security analysts consider in order to detect cyber threats. Listed below are some of them. Companies will continue to face additional security threats in 2021 as a result of widespread telework, such as: Remote Access Solutions are being used to their full potential.
With the recent and alarming news of ransomware and cyber threats, threat detection and analysis is now more important than ever. How to Detect Ransomware in your Network.
Cyber attacks are unwelcome attempts to steal, expose, alter, disable or destroy information through unauthorized access to computer systems. In addition to cybercrime, cyber attacks can also be associated with cyber warfare or cyberterrorism, like hacktivists. Motivations can vary, in other words.
17 cyber security attacks businesses need to be ready for in 2021. Recognize what a cyber attack & how to prevent one Other Types of Cyber Security Threats. Distributed Denial-of-Service (DDoS) attack? Eavesdropping is challenging to detect since it doesn't cause abnormal data transmissions.
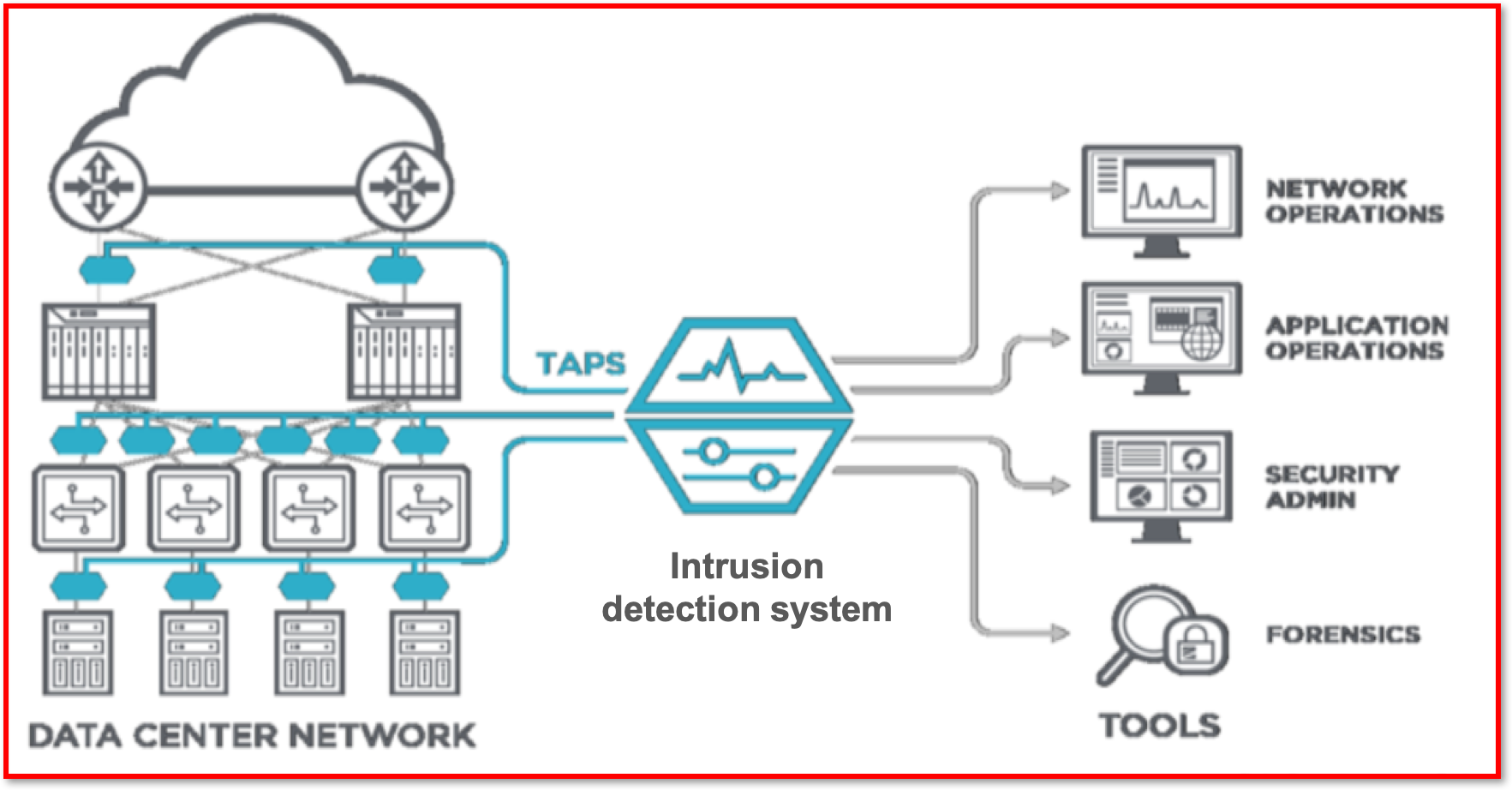
forensics network methods security cyber

nist respond cybersecurity

sqn banking essential
What are Cyber Threats? In the 1950s, the word "cyber" referred to cybernetics - the science of understanding the control and movement of machines and Modern Cyber Threats. Today, the term is almost exclusively used to describe information security matters. Because it's hard to visualize
1. Threat intelligence 2. Detection and analytics 3. Adversary emulation and red teaming 4. Assessment and engineering. In this blog the focus is on utilizing Splunk to address Detection and Assessment use-cases with MITRE ATT&CK framework. About Splunk ES & ESCU.
How can you detect cybersecurity threats before they occur? Cyber threats are inevitable. Not a day goes by when you do not hear about a breach. The loss of valuable data causes severe repercussions and it is up to us to implement preventive measures that can detect and mitigate such risks.
Detecting malware with deep learning. The traditional way to detect malware is to search files for known signatures of malicious payloads. Dynamic analysis tools try to detect malicious behavior during runtime, but they are slow and require the setup of a sandbox environment to test
Educate yourself about how cyber attacks look and work on social media platforms and learn how to Get additional protection through threat prevention software that can detect cyber threats and No threat is too small, no protection is too strong. However big or small, cybersecurity threats
Cyber detection; Threat estimation. I. INTRODUCTION. Unmanned aerial vehicles (UAVs) or drones are flying. order to detect this cyber-attack the distribution of signal. strength should be monitored. However, they do not provide. more details on how the GPS spoofing attack could be detected.

security hacked threats hackers hacker risk threat network dhs ninja breach bloatware toshiba lenovo millions bugs dell users put being
Fast detection is key to successfully containing any fallout from an information breach. To respond quickly to a cyber attack, you must first have the right Now that we've run through the right mechanisms for detecting a cyber threat, we'll explore how to respond if you do detect an attack,
Educating your employees about different cybersecurity threats, their impact and what they can The Pandemic Drove Up Compliance Costs; Here's How To Get Back On Track. • Disruption Of Business Operations: For some businesses, this is the lowest stakes result of a data breach or cyber threat.
Read about cyber security today, learn about the top known cyber attacks and find out how to protect your home or business network from cyber threats. 2. Use anti-virus software: Security solutions like Kaspersky Total Security will detect and removes threats. Keep your software updated for the
To protect against these threats, organizations need to quickly and accurately detect, investigate and respond to issues that could be indicators of insider attacks. Automate patch and vulnerability management to keep your systems up to date and protected against potential cyberthreats.
...quickly to new invisible cyber threats compared to traditional techniques and automated cyber-attack detection systems, which were used before. They also know how to quickly detect breaches. The current hybrid approach that is generally used today is to oversee automatic learning by
How to detect cyber threats. Cyber threat detection requires strong internal IT policies and advanced monitoring. While some companies utilize manual processes, research from IBM found that security automation can significantly reduce the cost of breaches.
How Dropbox Security builds tools for threat detection and incident response. The Pyramic of Pain - The relationship between the types of indicators you might use to detect an adversary's activities Cyber Kill Chain - It is part of the Intelligence Driven Defense® model for identification and
Cyber Threats. Los Angeles offers security app to safeguard public WiFi users. Comcast introduced the service at the CES 2019 held in Las Vegas and displayed a video presentation on how its product is going to monitor and help block security threats which are luring to invade home WiFi networks.
Detecting Cyberattacks Through the Ever-evolving Cybersecurity Industry. Cybersecurity has come a long way since its inception in the In the beginning, hackers were generally considered a nuisance, and their hacks - which were pretty limited in terms of their scope - were designed more
Cyber threats are constantly evolving and the processes and technology needed to prevent them are constantly changing. You need to have measures in How many times have bad actors attempted to gain unauthorized access? You may need to reference firewall logs to gather this intelligence.
Cyber threats are getting more sophisticated and intense amid increasing levels of remote work, cloud migration and advanced cyber adversaries. Cyber Threat Intelligence is Necessary for Enterprises. Advanced threat actors such as organized cybercriminals, nation-states and corporate

dhs security homeland fbi cybersecurity government counter terrorism national hackers department inside fusion center cyber hack centers threats russia clearance
11, 2022 · Consider signing up for CISA’s cyber hygiene services, including vulnerability scanning, to help reduce exposure to threats. CISA’s vulnerability scanning service evaluates external network presence by executing continuous scans of public, static IP addresses for accessible services and vulnerabilities.
Tracking evolving and increasing cyberattacks is key to better cyber security.

cyber animated gifs giphy
Detecting cyber threats can seem overwhelming when new threats are constantly making news and older threats are still capable of causing big problems. However, identifying threats can be made much easier by implementing protection and detection in depth. Executing the fundamentals of
I. Threat Detection. Detecting and identifying potential insider threats requires both human and technological elements. An organization's own personnel are an invaluable resource to observe behaviors of concern, as are those who are close to an individual, such as family, friends,
How to Detect Cyber Threats. There are a wide range of tools designed to detect and counter cyber threats, but effective cyber threat detection relies on enhanced visibility and situational awareness.
