How does a hacker pick their unlucky contestants? It's not unlike police trailing a suspect or thieves casing a location. Hackers find individual targets most easily by combing social media accounts of their victims; the past decade's social media explosion makes sharing one's info easier than ever—
Ransomware has been pervasive since the mid-2000s. The latest forecast, from Cybersecurity Ventures, estimates that global But it's not just ransomware itself that is cause for concern. It's that the nature of ransomware has changed. In its original format, bad actors and cybercriminals

eci broader bolder

kund bhishma dharma kurukshetra
Learn more about ransomware attacks, how to prevent them, and how security software can roll back ransomware attacks if they happen. Ransomware is a form of malware that locks the user out of their files or their device, then demands a payment to restore access.

Ransomware is a type of computer virus that blocks access to a computer and asks the user to pay money first before they can use the computer again, or it may encrypt your files and demand payment to decrypt them—hence its name.
03, 2020 · Training will reduce the risk of ransomware entering your network. Use email security software: Since a majority of ransomware attacks begin with end users clicking on links in an email, email security software will reduce the number of emails with malicious links and attachments arriving in your end users' inboxes. Systems can filter suspicious emails for review …Estimated Reading Time: 5 mins
to20%cash back · Protecting Against Ransomware Employee Education on Phishing Awareness, best practices, simulation testing Improve Security Posture Follow best practices …

zdnet pysa
In a 2018 blog post on defeating ransomware, we outlined some practical steps — still necessary and Cybersecurity Tactics to Prevent Ransomware. Ransomware is a type of malware that prevents or limits Find out how to increase efficiency and profitability with complete accessibility to all
Ransomware attacks are increasing because patch management techniques lack contextual intelligence and historical data needed to model threats based on previous breach attempts. As a result, CIOs, CISOs, and the teams they lead need a more data-driven approach to patch management
05, 2021 · Is There Any Protection Against Ransomware? In addition, Kaspersky Internet Security should be installed as well. By using this software, you can protect yourself from infected files while you download or stream something in real time. Ransomware cannot infect your computer, so cybercriminals are prevented from gaining access to your computer.

ransomware skyrocketing monetary demands attacks evolved quite become past course lot
Data Backup and Disaster Recovery. Hackers are a persistent lot. Even the most secure infrastructure may be exposed to the occasional bit of malware. However, organizations that have a comprehensive business continuity plan with data backups and/or disaster recovery can overcome a successful ransomware Reading Time: 5 mins

ransomware trojan wanted cryptolocker
However, this screen locker ransomware is easier to defeat, and just doesn't pose the same level of threat as encrypting ransomware. The most obvious way to test ransomware protection is to release actual ransomware in a controlled setting and observe how well the product defends against it.
How To Defeat Ransomware! how to clean ransomware tutorial, step by step. Details: Security Notes: How to Defeat Ransomware. Stolen data presents a burden to the thief. He needs to bring it to market, find a buyer, and compete with other hackers.
Help! Infected by Ransowmare? This video is a full guide on how to deal with a ransomware attack, how to decrypt your encrypted files, lockdown your
Ransomware-as-a-service is changing the game. Threat actors are getting bolder, stakes are higher, ransom costs and extortions are growing exponentially. See how CrowdStrike experts and our leading Falcon technology protects our customers from ransomware.
As more organizations confront ransomware threats, IT teams must take proactive steps to protect data and applications, which have become a high-value target for attackers. One of these steps is enabling multi-factor authentication (MFA) wherever possible, especially in the backup environment.
What Is Ransomware? Ransomware comes in many forms, but two main varieties have emerged: locker-ware and crypto-ware. Locker-ware involves a hacker taking control of a specific computer or network and then changing passwords so that systems cannot be accessed.
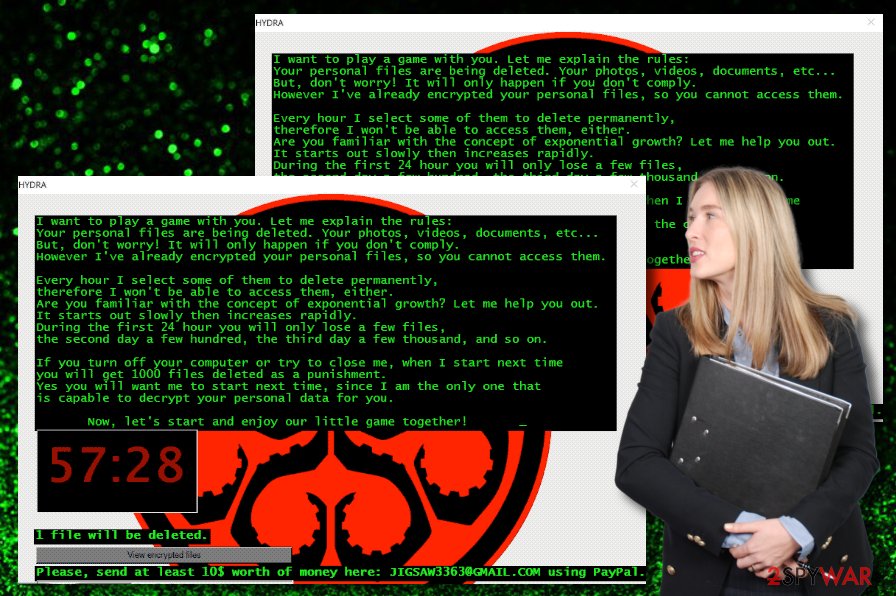
ransomware
How to Defeat Ransomware. So, you've been attacked by ransomware. What should you do next? 6. How to Prevent a Ransomware Attack. "Ransomware is at an unprecedented level and requires international investigation."—European police agency EuroPol.
Share on Facebook. Embed. Thwarting Cybercrime: How to Defeat Ransomware. Don't miss the ransomware protection tips you can only get from You will learn: • Danny's tips to protect yourself, your colleagues, and your family from cybercrime • How to defeat ransomware attacks by
How directors and board members can help defeat ransomware. October 29, 2019. When the subject is ransomware, we usually think of smaller municipalities and school districts, which often don't have the resources to fend off increasingly sophisticated cyberattacks.
Despite a recent decline, ransomware is still a serious threat. Here's everything you need to know about the file-encrypting malware and how it works.
Do not dispair , ransomware can still be defeated with the right controls in place. Bare in mind, ransomware is a well understood type of malware and there are effective existing countermeasures you can put in place in your It cannot be stressed how important it is to educate your staff on this too.

While knowing how to fight back if your company is attacked by ransomware is critical, taking proactive steps to minimize the odds that your organization falls Ransomware has significantly evolved over the years since it was first introduced back in 1989 as the 'PC Cyborg' Trojan and the user had to
Connect With Us. 3 Understanding Ransomware and Strategies to Defeat it. In Figure 3, we see that there was a spike of ransomware building to a peak in Q2 of 2013, and then dying down until mid-to-late 2014, when the pace picked up again. WHITE PAPER. Primer: How Ransomware Works.

ransomware
are four precautions you can take to foil ransomware demands, enabling you to confidently deny data ransomers: Have a backup plan: Even if it happens once a week on your uncle’s tape drive, make a point of duplicating your data,... Have a restoration plan in place: J ust h aving backups is not ...
Ransomware is a virus - a malicious program, that is designed to encrypt files on local and networked drives. Ransomware-as-a-service (RaaS). RaaS is one of the main factors why the crypto-malware business is booming. If felons, who are interested in earning easy money but lack
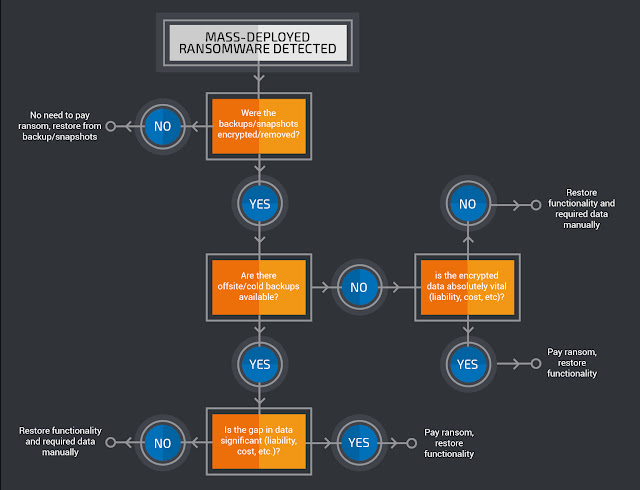
ransomware future breach event figure
What is ransomware, what does it do to my computer, and how can I protect myself from it? Here's what you need to know about encryption Trojans.
Keep reading to learn how ransomware works and how to get ransomware protection using strong antivirus software. The first recorded ransomware attack occurred in 1989, when evolutionary biologist Joseph Popp infected floppy disks with the AIDS Trojan and distributed them to
02, 2020 · Ransomware is everywhere these days, and we want to help DFIR investigators take a methodical approach to responding to an attack. In this post, we’re going to talk about briefly review ransomware and the basics of the Divide and Conquer DFIR Process, then we’ll summarize the big-picture investigative questions that need to be answered for responders to …
Save as PDF. Overview. Defeat ransomware with frequent backup. Prepare your Code42 environment. Set file backup frequency and version retention. In Frequency, drag the slider on Backup new version to indicate how often to back up and create new versions of files in the archive.
![]()
kaspersky antivirus 1085 computerbase

ransomware equal created must know fix
Ransomware targeting Linux servers is on the rise. See who was hit and how to protect your system from Linux ransomware. Linux Ransomware: Famous Attacks and How to Protect Your System. June 10, 2021.
The REvil ransomware gang is in the news again! How can we stop this malicious ransomware group? What will it take to defeat REvil, other ransomware gangs, and really all malicious hackers and malware? Five things: Better local security controls, political agreement, global law
Ransomware attackers are getting better at evading security software. Find out how to stay a step ahead with the latest in our series There Are Many Ways to Repel Ransomware, Only One Way to Defeat It. The ransomware infection starts quietly encrypting every file it can find on your hard drive.
Ransomware attacks continue to dominate headlines and plague organizations of all sizes in both the private and public sectors. As with other cybersecurity attacks, no organization is immune. Your best option is to prepare for this type of attack by using a three-pronged approach: plan, prevent, and
Ransomware attacks have been getting more dangerous. I'm going to show a method to recover files by In this post, I'm going to show how you can use active defense and cyber deception techniques to After that, I'm going to demonstrate how it works by using an open-source ransomware sample.
To effectively defeat ransomware, we have to be able to distinguish between legitimate user activity and an infection. It would take some time to come up with a good baseline (how many file modifications are considered "normal") that we could use as a threshold, and there would still be
wiped remotely mybook geformatteerd afstand unplug viruses backup formatted ghacks reset suddenly koppel attackers owners eksterne mistet androidpolice sunpeak meilleurs
Ransomware - Still Going Strong and No End in Sight. How Attackers Gain Initial Access. To prevent a ransomware attack, and most other malware attacks for that matter, defenders must stave off attackers' attempts to Defeat every attack, at every stage of the threat lifecycle with SentinelOne.
