Blog Mobile Security The Do You Knows of DDoS Attacks. With the rise of social media, addictive games, and on-demand apps, our mobile devices have become an inextricable part of us, like an additional limb. So how did the attack happen and what can you do to protect yourself?
![]()
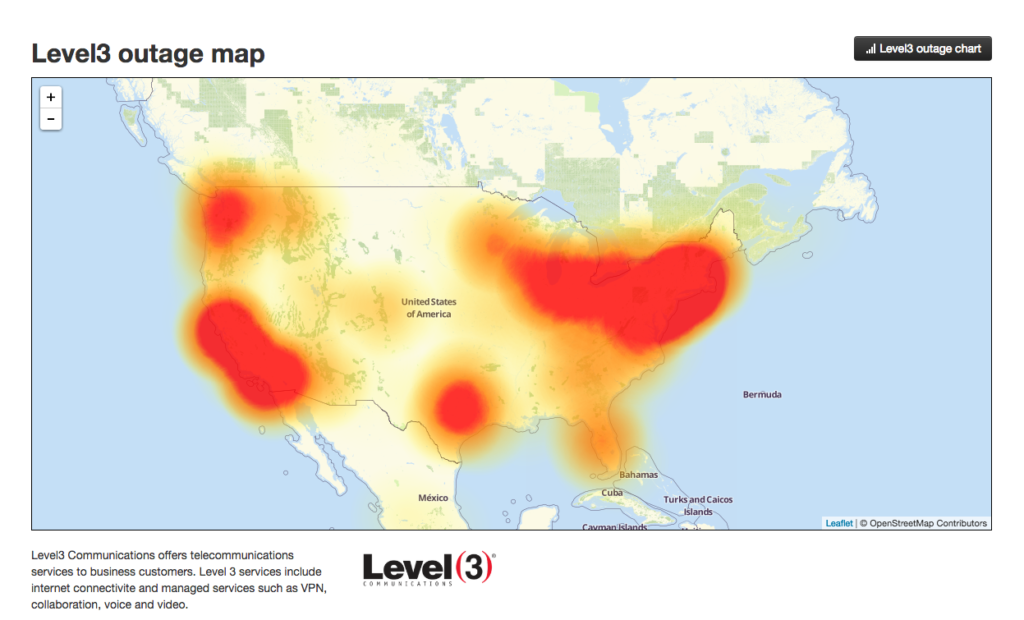
lottery national lotto last ddos peak attack hit outage minute
The description of DDOS on mobile (DDOS Android) App. "A DDoS (Distributed Denial of Service) attack is an attempt by an attacker to exhaust the resources available to a network, application or service so that genuine users cannot gain access."

ghoul tokyo dark war mobile anime android pc fantasy apk official based games wa skill ios launches gamesamba tokyoghoul battle
#DDos is Denial of Services attack which we use to take down any Website, Server, Victime's IP. #How install How to use DDoS Attack:- Just enter website domain name for example - or victim Ip address and enter port default - 8080 or 4444 press enter and attack started.
DDoS attack is an attempt to make an online service unavailable to users. Large. Shows the top reported attacks by size for a given day. Unusual. Shows attacks on countries experiencing unusually high attack traffic for a given day. Combined. Shows both large and unusual attacks.

ddos attack anatomy
Learn how DDoS attacks are performed with DDoS Tool. Here is a list of the most popular DDoS attack tools with their complete details. The duration for which the DDoS attack will last depends on the fact that the attack is on the network layer or application layer.
Denial-of-service (DoS) and distributed denial-of-service (DDoS) attacks are malicious attempts to disrupt the normal operations of a targeted server, service, or network by overwhelming it with a flood of Internet traffic. DoS attacks accomplish this disruption by sending malicious traffic from a
How to initiate Denial of service attack from android. To do a DDoS attack from android, you will require an Internet Connection and an app. Distributed Denial of Service attack is a type of cyber attack where many of computers (Infected with malware) act as a botnet and initiate DDoS attack to
"A DDoS (Distributed Denial of Service) attack is an attempt by an attacker to exhaust the resources available to a network, application or service so that genuine users cannot gain access." Source: Created by Benjamin Ruesink Powered by Unity.
29, 2018 · 5Gbps DDoS Protection Port Speed 10Gbps $ p/m SH-Plan 3: 15GB Gen4 NVMe Storage 2x CPU Core 2GB 3200Mhz DDR4 RAM 6MB/s Disk I/O EP 40 Unlimited Bandwidth 5Gbps DDoS Protection Port Speed 10Gbps $ p/m SH-Plan 4: 20GB Gen4 NVMe Storage 3x CPU Core 4GB 3200Mhz DDR4 RAM 10MB/s Disk I/O EP 50 Unlimited …
21, 2021 · How to check for and stop DDoS attacks on Linux . Jack Wallen walks you through some of the steps you can take to check for and mitigate distributed denial of service attacks on a Linux server.
DDoS attack on Bluetooth. While modern Wi-Fi-routers are able to filter unwanted packets, most Bluetooth adapters They by and large do not care what package and how many of these packets you will send. Some can drop almost all the signals of the mobile network, Wi-Fi and Bluetooth at
DDoS attack tools that can create a distributed denial-of-service attack against a target server. How DDoS Attack Tools Works? DDoS attack tools target a server or network by finding vulnerable systems within the network and injecting malware on those systems.
In a distributed denial-of-service attack (DDoS attack), the incoming traffic flooding the victim originates from many different sources. This effectively makes it impossible to stop the attack simply by blocking a single source.[2]. A DoS or DDoS attack is analogous to a group of people crowding
How. Details: Distributed Denial Of service or DDoS attack is an attack where multiple compromised systems are used to target, such as a server, website or How. Details: It is unlikely that your Android device will become the target of a DDoS attack because the IP address on a mobile device is
24, 2022 · Andorra Telecom, the only ISP in the principality of Andorra, suffered repeated distributed denial-of-service (DDoS) attacks during a multi-day Twitch gaming tournament. From a report: The DDoS attacks occurred during the scheduled SquidCraft Games tournament in Minecraft, one of the most successful Twitch Rivals tournaments ever broadcast. Eight or more …
How to Prevent DDoS Attacks on Mobile Apps. How can we Cope Up with These Attacks? What is a DDoS Attack? So, how does a DDoS attack on mobile apps look like? Well, if we take a really simple example then imagine someone built an app and put it on the mobile app store and you as
Distributed denial of service (DDoS) attack uses a large number of machines on different networks to disrupt a particular service provider; this attack is Slowloris is a highly-targeted attack, enabling one web server to take down another server, without affecting other services or ports on the target network.
10, 2020 · This article was written by Brice Pellé, Principal Specialist Solutions Architect, AWS September 14, 2021: Amazon Elasticsearch Service has been renamed to Amazon OpenSearch Service. See details. AWS AppSync is a fully managed service which allows to deploy and interact with serverless scalable GraphQL backends on AWS. AppSync uses security best …

phishing social engineering scams security attack bait report mobile spam victims attacks hackers certificates valid exploit trust fake apps using

codm virar lado
How to ddos on mobile for free. How to Boot People Offline on PS4 on Phone in 2020 DDoS People Off PS4 Using iPhone/Android for FREE Hey everyone ...
computing, a denial-of-service attack (DoS attack) is a cyber-attack in which the perpetrator seeks to make a machine or network resource unavailable to its intended users by temporarily or indefinitely disrupting services of a host connected to a of service is typically accomplished by flooding the targeted machine or resource with superfluous requests in an …
A distributed denial-of-service (DDoS) is a large-scale DoS attack where the perpetrator uses more than one unique IP address, often thousands of them. How can you tell whether you are being DDoS attacked? What are the security issues for mobile applications?
Learn how hackers launch DDoS attacks and how distributed denial of service works. We compile the best tips on how to DDoS so you can understand how cybercriminals target their victims. We also include valuable advice on what you can do to prevent getting DDoSed and show what these
16, 2022 · DDoS (Distributed Denial of Service) Is A Framework Attack Against Website(s) And IP(s) ddos ddos-tool ddos-attack ddos-attack-tool Updated Nov 2, 2019
27, 2018 · A Distributed Denial of Service (DDoS) attack is an attempt to make an online service unavailable by overwhelming it with traffic from multiple sources. They target a wide variety of important resources from banks to news websites, and present a major challenge to making sure people can publish and access important information
outage hackernews
How to Take Safeguard from DDoS Attacks on the Mobile Apps? The old wisdom that insists on prevention as the ideal measure compared to the You cannot stop DDoS attacks from taking place. At a pace, the mobile app universe is going forward, and not all security risks can be addressed

shelter fallout playstation nintendo tonight switch coming screen
mobile landscape is no different and malware aimed specifically at mobile devices is multiplying with every passing week. Learn more; How good is the malware protection on BullGuard Mobile Protection? In short, it is industry leading. BullGuard Mobile Protection uses a cloud-based Antivirus engine.
How to Boot People Offline on PS4 on Phone in 2020 DDoS People Off PS4 Using iPhone/Android for FREE Hey everyone ... Friend this video I show Ddos site with your Android mobile This video only education purpose AnDosid is a powerful hacking ...
DDos is defined as "Distributed Denial of Service Attack". This tutorial explains what is DDosing and how to hack a website temporarily using DDos method. It is very common news when you hear that a website is hacked by a group or a website is crashed and etc. etc.

mit protect info data protection securing systems technology
How to do Ddos attack from Android - Ddos attack from termux - Easy steps to do ddos attack. Hello guys welcome to Android Academy. In this tutorial we are going to learn how to ddos attack with android device.
Today, I will explain how to neutralize this 'natural disaster' without (OK, almost without) committing a criminal offense. Modern Wi-Fi routers can filter out unwanted packets, but the majority of Bluetooth adapters are dumb, to say the least. They neither care what packets you send, nor what is their

radware develops freelancer
DAVOSET (DDoS attacks via other sites execution tool) is a DDoS tool, written in Perl, that uses zombie systems to distribute the attack across multiple systems. This tool uses Abuse of Functionality and XML External Entities vulnerabilities on other sites to "zombie" them and attack the target site.
12, 2019 · A distributed denial-of-service (DDoS) attack involves flooding a target system with internet traffic so that it is rendered Recent DDoS attacks have evolved to become a serious threat to the smooth running of both businesses and governments. Botnets of malware-infected computers or IoT devices offer one common platform for DDoS attacks.
Thanks for watching guys! If your reading this, you have to like and sub!!!How to ddos anyone DdosPlayStation ddos PlayStation party ddos Xbox ddosHow
β How to become an author. All streams Development Admin Design Management Marketing PopSci. 23 April 2014 at 20:29. DDos-атака на телефон. Spamming and anti-spamming.
Устраиваем DDoS атаку на Wi-Fi с телефона.
