
vulnerable vm free download. Metasploitable This is Metasploitable2 (Linux) ... me @ahmaddotninja 5. Why didn`t I setup tools ? because you should learn how to install any tool on any platform Create an unlimited number of live streams, sessions, expo halls, exhibitors' virtual booths and sponsors'...
Part 3: From Vulnerable Machine to A Simple Conceptual "Cyber Range" (3 parts, A, B and C.) Before formally entering this step, it is useful to recall how vulnerable machines are usually "broken into". This is probably the most frustrating aspect of creating a vulnerable machine.
I have decided to create vulnerable machines that replicate the vulnerabilities and difficulties I've personally encountered during my last year (2017) of penetration testing. The VM can be downloaded as a .zip file or as a much smaller .7z 7-zip Archive. Both files contain the exact same VM!
Create randomly insecure VMs. Contribute to cliffe/SecGen development by creating an account on GitHub. Boxes like Metasploitable2 are always the same, this project uses Vagrant, Puppet, and Ruby to create randomly vulnerable virtual machines that can be used for learning or for
Virtual machines can seem juuuuust a bit too geeky for most otherwise computer-friendly people. The next screen asks you to either create a new hard disk image or use an existing one. Assuming this is a first install, keep Boot Hard Disk checked and hit Next to create the image.

vulnerabilities openbsd authentication vulnerability dashboard template multiple cve privilege escalation local qualys shown track below create
The OWASP Broken Webapps project is a VM that contains a whole host of vulnerable web applications. The link provided lands to sourceforge to download the VM. Vulhub is a website that contains a massive collection of vulnerable virtual machines.
Vulnix is a specially made vulnerable virtual machine of SSH and NFS [Network file system] . Vulnix will guide you on how false configuration of NFS can be used to escalate To make this happen, I can create a user in my own system with the permission same as the vulnix user in vulnix VM.
Step-by-Step: Create a VM Using Hyper-V Manager. Extra: A Virtual Machine Example—Ubuntu Extra: How to Load Your Virtual Machine. This is one of two methods to create a virtual machine using Windows 10's built-in tool. It's the quickest and visually easier of the two.
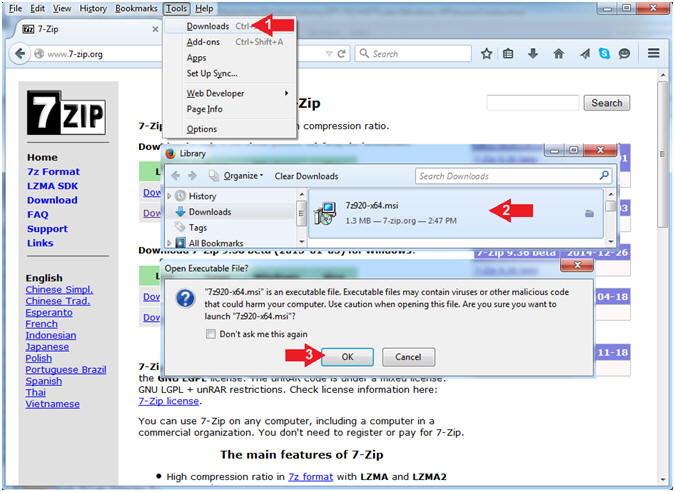
Creating a vulnerable virtual machine Now we are ready to create our first virtual machine, it will be the server that will host the web applications we'll use to practice … At the time of writing, it is Wait for the download to finish and then open the file.
Recently, I ran across SecGen, a project which allows a user to create random vulnerable machines. I absolutely love vulnerable machines, since a vulnerable VM is a safe and legal way to practice hacking tactics, test out new tools, and exercise your puzzle-solving skills.
I will be using Vagrant to create a virtual machine. I know we can use ansible or other tools but I'm not that smart. For vulnerable applications, I'm here using You have to open that file in any text editor and change Change the = " base " to = " ubuntu/xenial64 ".
Using msfvenom to create a payload. I'd like to one day learn how to do this without msfvenom. Figure out what that find command does. The validate binary, which is not a standard Linux executable, but another custom, vulnerable program in Brainpan, provides another exploitation (also an overflow)...
Creating a client virtual machine. Configuring virtual machines for correct communication. Getting to know web applications on a vulnerable VM. Now we are ready to create our first virtual machine, it will be the server that will host the web applications we'll use to practice and improve our
Building a vulnerable vm? Hi r/hacking, I'm new to the sub and new to ethical hacking. I got interested in ctfs and have been looking at how to set The web is littered with "How to hack" vulnerable vm's but not setting them up. I'm wondering if anyone knows of a good article to read up on setting them up.
How to Create a Virtual Machine Clone. Creating a VM clone is simple thanks to Microsoft's Disk2VHD or CloneVDI. Disk2VHD creates a copy of your installed software that runs on software known as a virtual machine. A virtual machine fakes the environment of a physical computer.
SecGen creates vulnerable virtual machines so students can learn security penetration testing techniques. Boxes like Metasploitable2 are always the same, this project uses Vagrant, Puppet, and Ruby to quickly create randomly vulnerable virtual machines that can be used for learning or

samba

zerologon exploit ngi vulnerabilidad exploiting 1472 cve zeros hacking servers github ciberseguridad vulnerable
The VM was built as a capture-the-flag game, where players need to gain deeper access into the Solving the easy challenge only requires knowledge of how Docker works, said Anant Shrivastava Players have to gain access to the Docker container through a vulnerable web application and
...our first vulnerable VM We are going to create a linux box If you're not aware of creating VMs then see my previous two posts Install Vagrant Create Vagrant Vagrant is a tool for building and managing virtual machine environments in a single workflow. more info click here Download Head up to
I realize virtual machines don't provide complete security and isolation for, say, loading a machine up full of viruses, but I just want to Setting up a vulnerable web app in a virtual machine is relatively safe. The risk is an attacker gaining access to that VM over the network, so as long as you

check heartbleed strength tweet test
Take a classic VM and use the VHD to create a new VM that uses the Resource Manager deployment model and managed disks. This preselected value is configured at the point of Snapshot or VHD creation and will carry over to the new VM. If you need to modify disk type take a new snapshot
Exploitation on Linux. Exploiting a vulnerable Windows VM. Creating a vulnerable S3 instance. Configuring and running Scout Suite. Setting up the tool. This section is a beginner-oriented introduction to how an individual without access to a ready-made AWS environment can set up a

Preparing a VM for Template Creation. Before creating a template, you should prepare your VM. Let's consider the main points of VM preparation. It also discusses how to create a customization specification for further cloning of VMs from your template. In order to prepare Xubuntu Linux
This post will cover how to set up a vulnerable VM running phpmyadmin which can be exploited with CVE-2018-12613. There's a Metasploit module for that, and this ties in nicely with rewriting the Ruby exploit in Python. But before that I needed to recreate the environment to personally verify
...how I go about building vulnerable VMs, so I thought that I'd write up a little guide to help others who might be thinking of creating their own vulnerable CTF or You can either use a static IP address for the VM (which can be very annoying for end users), or you can add a couple of settings (constants)
This document explains how to create a VM using the azurestack Terraform provider with Service Principal Name authentication. An active Azure Stack Hub Subscription (required to create SPN if you want to use the same SPN for both Azure and Azure Stack Hub).
Setting Up a Vulnerable Target. A test environment provides a secure place to perform penetration testing and security research. The easiest way to get a target machine is to use Metasploitable 3, which is a vulnerable virtual machine (offered in both Ubuntu Linux and Windows Server flavors)...

exploit
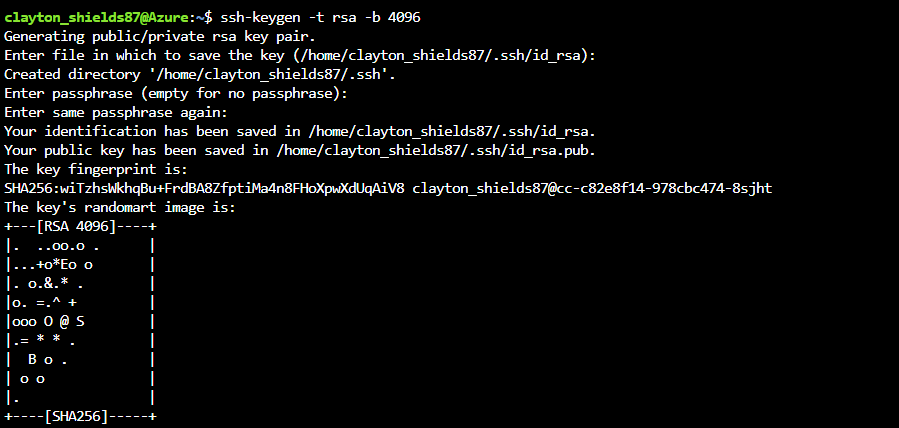
rsa
How to Setup a Vulnerable Virtual MachineПодробнее. Creating a VM to learn Linux PrivEscПодробнее. Kali Linux Course (13 Installing Vulnerable Server in virtual machine)Подробнее. Lets become HackerKids! (Vulnhub VM)Подробнее.
