, having an accessible FAQ page that addresses questions about cybersecurity can help trainees prepare for the training and keep answers to important topics and questions available long after the program has ended. Create visual cues: Having visual cues such as posters, emails, or newsletters around the workplace can help keep the ...

cybersecurity
Then, your cybersecurity program can raise awareness among all company employees of these security 'laws.' People need to know about secure password management, data system protection and how to Hire a specialist or a specialized company to periodically audit your cybersecurity program.

covid coronavirus pandemic health social wiggers kyle experience class user current span

police west midlands office officer computers using database computer cios flickr cgi headaches cfos cybersecurity reporting massive create dispatchers remember
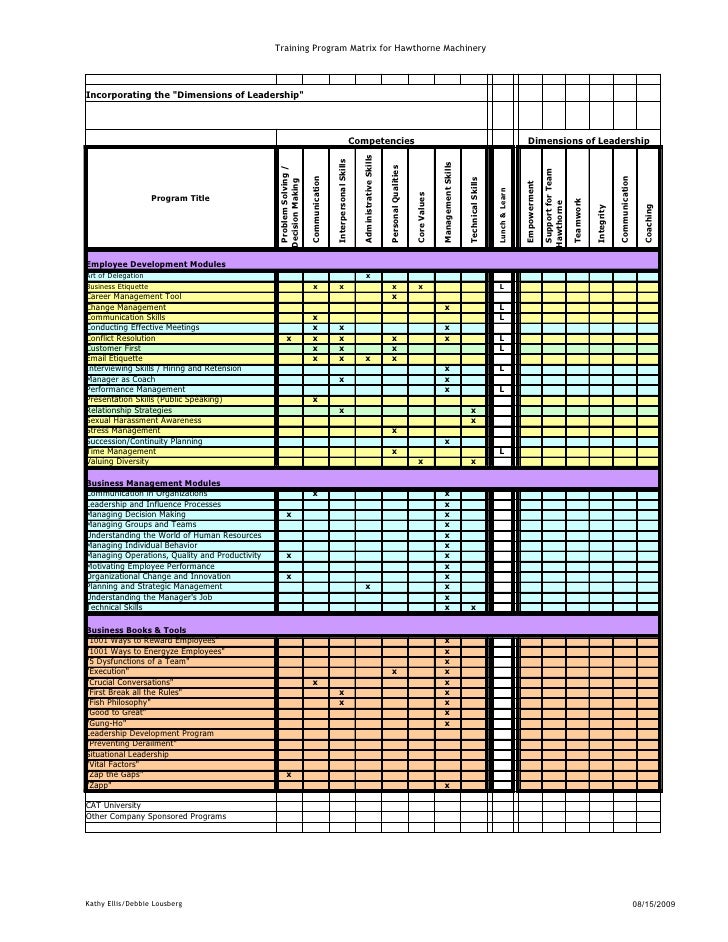
matrix training program leadership hawthorne machinery slideshare
Understanding the top cybersecurity programming languages for this year and beyond is important for either getting your next job or planning your Become a cybersecurity engineer so you can help companies and organizations of all sizes protect data from getting stolen, hacked, leaked, or damaged.
Follow these steps to create your own cybersecurity training materials. The lack of cybersecurity training for employees is directly evidenced by the spike in cybersecurity incidents. Of an average 3,269 security incidents reported in 2018, careless employees or contractors were the root cause of
Developing Cybersecurity Programs for NSF Projects. Center for Trustworthy Scientific "A cybersecurity program is a structured approach to develop, implement, and maintain an Virtual project teams are commonplace. While this can create challenges, it also creates opportunity.
Creating a cybersecurity strategy. So how do you maintain security of sensitive digital assets? BMC works with 86% of the Forbes Global 50 and customers and partners around the world to create their future. With our history of innovation, industry-leading automation, operations, and
08, 2018 · Creating a successful training program is a massive undertaking. It doesn’t just require one to grab “Cybersecurity 101” material from the Internet, stuff it in a PowerPoint presentation, and expect trainees to understand what’s at stake, let alone change unwanted behaviors. It’s more thoughtful and systematic than : Jovi UmawingEstimated Reading Time: 9 mins
16, 2021 · In that respect, the “hardest part” of how to create a cybersecurity program will be making sure you’re staying up to date with the latest vulnerabilities and exploitations, and keeping your internal and external networks patched up and well-defended. Steps For Building a Cybersecurity Program 1. Think about the data your company stores
The following steps illustrate how an organization could use the Framework to create a new cybersecurity program or improve an existing program. Nonetheless, not all activities in a cybersecurity program may give rise to these considerations. Consistent with Section ,
Creating awareness on the importance of cybersecurity and training employees on how to be proactive in safeguarding private information is just as A strong cybersecurity strategy must go beyond basic employee training and simple security hygiene practices. Attacks are becoming
cybersecurity assessment finra checklist excel spreadsheet tool firm cyber center complaint user

nist
How to Use NIST's Cybersecurity Framework to Establish a Cybersecurity Program. It should also be repeated whenever you change the scope of your program, whenever your threats, vulnerabilities or risks change, or whenever your Target Profile or Target Tier changes.

darpa drones insect flying drone uav military program autonomy prey fla lightweight fast inside buildings hawk
Building a Cybersecurity Program Tutorial. 19 видео 6 581 просмотр Обновлен 28 мая 2014 г. Specifically, this tutorial will provide an overview and process for developing a cybersecurity plan for scientific computing projects.
How can I create a cybersecurity program for my business? Is that what you are thinking? If yes, then you are at the right place. Thankfully, you don't have to create everything from scratch as there are many frameworks you can use for this purpose. You can either opt for the NIST framework or
cybersecurity
Cybersecurity Firewall: How Application Security Works? The Cybersecurity Framework defines 7 steps for establishing a cybersecurity program Here's how the Cybersecurity Framework was used to demonstrate how cybersecurity practices at nuclear power plants align to the Framework.
Tiers provide context for how an organization views cybersecurity risk. and their in-place Organizations may also use this process to align their cybersecurity program with their desired Table 5 provides an example of how a mapping can be used to create a Current Profile for a
to create a cybersecurity program?First things first. Data is now considered the new market gold, so company's confidential …Second step. After organizing the information into classifications, you have to identify where …Third step. Catalog all the hardware and software used in your company. Remember
A cyber security program is a documented set of your organization's information security policies, procedures, guidelines, and standards. How do I start learning cyber security? Basic Cybersecurity concepts can be learned with the aid of courses which are offered by multiple IT companies.
How to Create an Effective Information Security Risk Management Framework. In this post, I will share some tips about how to create an effective ISRM strategy and what a good program looks like. Risk management in cybersecurity is managing the security and privacy risks related
04, 2021 · But, when a cybersecurity breach hits, you might come to wish you’d never started relying on such technological conveniences. Luckily, there are plenty of measures that can be taken to create a safer network for your staff, students, and their private data. Essentially, you can either build or buy your cybersecurity program – or combine both.

cybersecurity
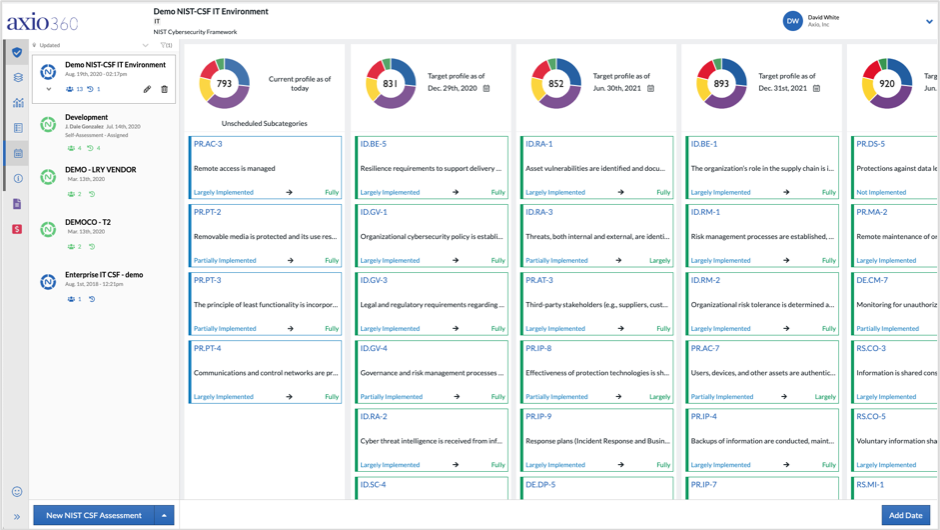
nist csf axio cybersecurity framework functions tool planning profile assessment implement roadmap interface target
What they are not sure of is how to create a strategy that helps them understand and address the threats, in all their forms, today and in the years ahead. Understanding the true costs and impact of cybersecurity programs" shows that more spending doesn't necessarily lead to better protection.

brain google fly 3d map interactive ai reconstruction data right pixel wiggers kyle above bottom using class called author avatar
Cybersecurity tutorial. Explained for Beginners. A Practical Implementation smaller companies, this can help in understanding how to provide basic security for computer systems awareness is a critical component of a comprehensive cybersecurity program. The guidelines have been developed from a technical perspective to create a sound and
Why Learn Cybersecurity? Data is valuable. With so much sensitive information online Learn how cybersecurity evolved as a field, and what standards, regulations, and frameworks arose to respond to evolving cyber threats. What you'll create. Portfolio projects that showcase your new skills.
In a world where digital transformation increases compliance burdens, understanding how to best secure on-premises, cloud, and hybrid IT Understanding the similarities and differences across the top 25 security frameworks can help you create a more robust cybersecurity compliance program.
Reading Time: 5 minsIdentify all types of data and sensitive data you store. Whether it’s customer payment …Define where that information is stored. Once you identify what sensitive data you have, you …Take record of all hardware and software devices in your network. As
days ago · 5 steps to a successful cybersecurity champions program 1. Plan your security champions program thoroughly. Barker says prior planning is key to launching and maintaining 2. Secure leadership buy-in to support your program. Leadership support has a significant impact on the success of 3. ...
How can you improve cybersecurity in your business? 1. How to identify cybersecurity risks in advance. 2. How to prevent cyberattacks and data Regardless of size and industry, any company needs to develop a cybersecurity program to preserve business continuity and operational efficiency.
on these internationally recognized best practices, we recommend creating a Cybersecurity Management Plan structured on three core principles: 1. Readiness. Firstly, you should focus on prevention. Adopt a risk-based approach to gain visibility, precede known threats, and prioritize assets that require the most protection. 2. Proactivity
Enrollment in computer science programs has also increased tremendously in the past couple years, and many schools are adding cybersecurity majors and concentrations, said Rachel Greenstadt, associate professor of Comment and share: How to become a cybersecurity pro: A cheat sheet.


awareness security posters role training poster know employees
27, 2022 · A security awareness program can be an extremely valuable tool. It helps an organization thwart active attacks and reduces the amount of weaknesses that can be exploited by an attacker. However, just as organizations differ in size, purpose and mission, the attacks directed at them also differ in method, skill set and Reading Time: 9 mins
...risk-based cybersecurity program, it's ready for the next level: creating a framework for establishing and monitoring its security risk posture. that the score is the byproduct of real data—helps enable security and business-line leaders to collaborate on how to help improve that score.
Don't know how to create a cybersecurity policy for your business? Read on to find out now. Employees sometimes give cyber-criminals access into the defense networks of businesses due to ignorance on how to handle activities in accordance with cybersecurity best practices .
How to Create a Cybersecurity Awareness Plan. As a reader, you're now aware of six serious cybersecurity threats that can be solved through employee awareness - but how can you make your fellow team members more aware of common cybersecurity threats?
Cybersecurity program best practices. ERISA-covered plans often hold millions of dollars or more in assets and maintain personal data on participants, which can make them tempting targets for cyber-criminals. Responsible plan fiduciaries have an obligation to ensure proper mitigation

cybersecurity practices

cybersecurity terms know need security
No matter how securely you create your cyber-environment, you will never be 100% safe from attack. Your school should have a plan to protect data from Educating Staff and Students. The Cybint Cybersecurity Bootcamp is an opportunity to provide your students an accelerated program that
A cybersecurity program is something which you must adapt and maintain based on your business needs. A fixed plan for everyone is not possible Faraday is a great tool to support your cybersecurity program, with a lot of possible usages, features which are updated frequently, with support for
To create effective educational programming, it's best to consult with subject-matter experts first. Create a quiz to test employees' knowledge. Checking employees' understanding of cybersecurity is a critical measure for avoiding future data breaches caused by these colleagues.
, it creates a pilot program to create an “energy star” type of label so the government – and the public at large – can quickly determine whether software was developed securely. Too much of software, including critical software, is shipped with significant vulnerabilities that can be exploited by cyber criminals.
How Logistics Procedure Optimization With AI Can Help Diminish The Transportation Sector's Mar 22, 2019,08:45am EDT|2,885 views. Building An Effective Cybersecurity Program. There are many areas of cybersecurity that support these core fundamentals (asset management, incident
A cyber resilience framework, or cybersecurity framework, is a crucial component of modern-day business. Developing cyber resilience does not come down to having the perfect incident response tools. More often than not, the companies that struggle with cybersecurity don't fail because of
